BlackHat USA 2010
Learning from the Best
I've been to BlackHat twice now, and both times I have taken the same lesson home: If you think things are getting better in the field of computer security, you're probably wrong. Over the years, progress has been made identifying bug types – currently the CWE lists 668 weaknesses in 120 categories – and some progress has been made with projects to identify and remove them systematically (e.g., OpenBSD has had remarkable success). However, you then come to the BlackHat conference and see a presentation like "HTTPS Can Byte Me," in which Robert Hansen and Josh Sokol disclosed 24 vulnerabilities (Figure 1) that can compromise the integrity and security of SSL-encrypted web traffic [2].
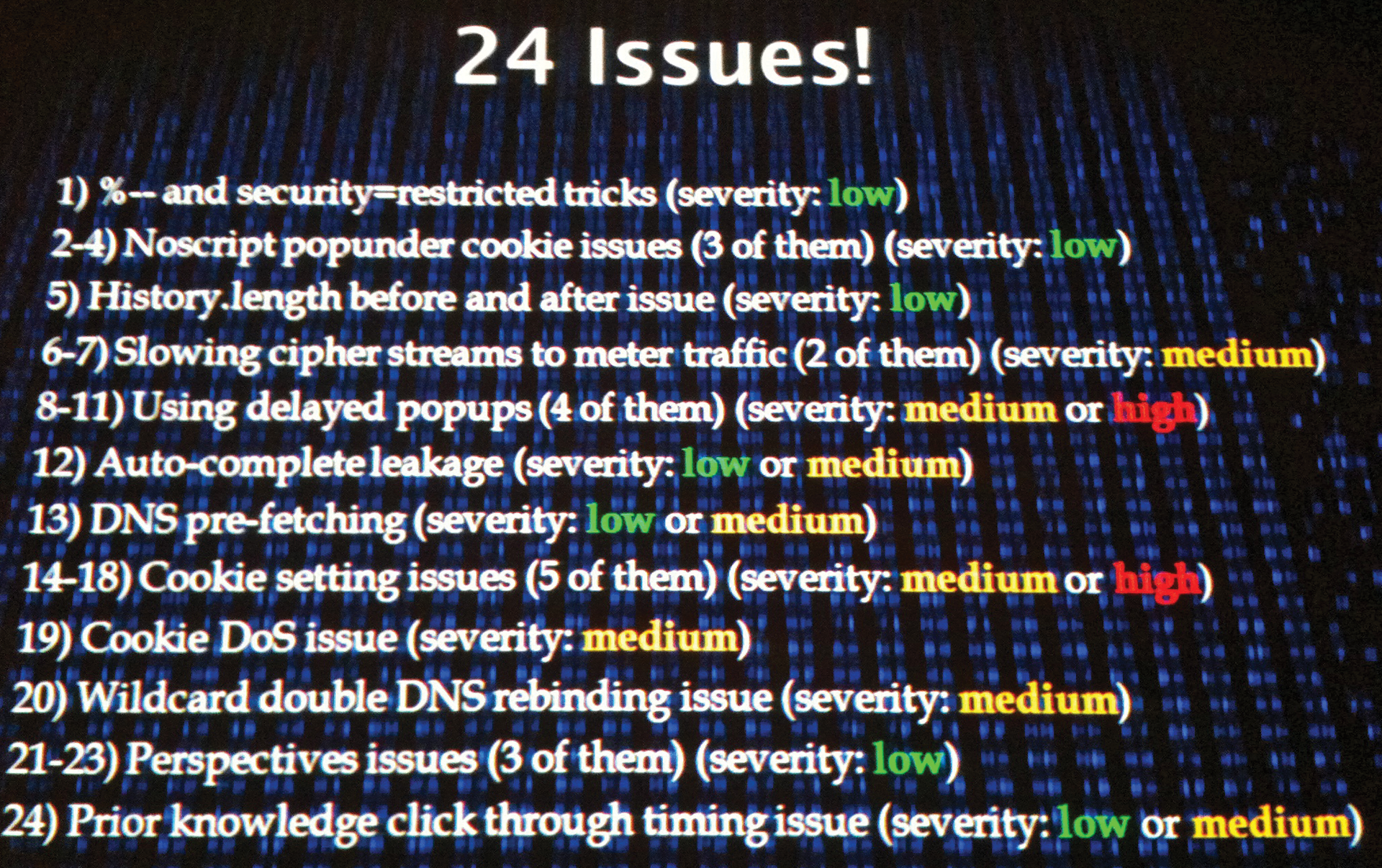
The problem is not so much a failing within SSL, but unless you're taking extreme measures to protect network traffic against analysis (e.g., padding traffic out, introducing time delays, etc.), chances are, attackers will be able to glean information even if they can't read the traffic directly.
Also, consider the case of the well-meaning web browser that attempts to be helpful. I guess people hate typing in personal information, so almost all browsers support "auto-complete," which automatically fills out form fields (e.g., name, address, and credit card number). Unfortunately, this feature can be abused by attackers (imagine that), allowing them to steal personal information saved within your web browser if you visit a web page. Using JavaScript, they can set it up so you don't even have to type anything in – combined with a hidden IFRAME, you might never realize that it happened.
The security talks are especially worrying – the ones in which researchers don't find new vulnerabilities but simply quantify existing ones. In the case of SSL certificates, they scanned the Internet and found 1.2 million SSL-enabled websites [3] [4]. Among the problems found were certificates for reserved addresses (e.g., 192.168.1.2, a reserved IP address used by multiple sites) that never should have been allowed. Also, they found 50 percent of servers configured to allow SSLv2 (known to be insecure for 14 years).
Now, I'm not a glass half empty kind of guy, but seeing 50 percent of servers configured insecurely is a bit depressing (which is probably why most security people buy beer in pitchers, not glasses).
BlackHat isn't an unending stream of bad news, however. Many of the presentations not only present problems but also discuss the solutions. The perfect example was a presentation called "Lifting the Fog" [5], in which Marco Slaviero scanned for memcached (a memory-caching program widely used to speed up web-based applications). He found many memcached servers open to the world, and by using two poorly documented commands, stat detail on (which enables debugging) and stats cachedump (which lists all the key names), he was able to retrieve all the items stored in the memcached server. And by "all" I mean everything; according to his presentation, he retrieved 136TB of data from 229 memcached servers.
The good news is that securing your memcached is simple: Firewall it so that only local trusted systems can connect to it (and if you must use it over the Internet, set up a VPN to connect systems to it). This solution is not magical, but it drives home the point that you need to test and verify security measures using tools like Nmap [6] (which is how he found all the memcached instances).
So, if you need an excuse (well, a work-related excuse) to go to Las Vegas, BlackHat, and Defcon afterward, they're not only a lot of fun, but very educational. My only complaint is that with 10 tracks, chances are you'll have to choose between two or more interesting talks, which is definitely a glass half full type of problem.
