
Free Security Compliance Manager hardens server systems
Defending the Baseline
When companies deploy multiple Windows servers, they often have a problem defining and distributing security settings uniformly and for best possible effect. The free Microsoft Security Compliance Manager (SCM) contains templates and recommendations for protecting servers via Group Policies and PowerShell scripts. The focus is on protecting the Windows operating system. In the new version, the tool can also protect Exchange Server 2007 SP3/2010 SP2.
Basically, the tool creates templates for Group Policies that integrate Microsoft recommendations. Administrators can customize the policies to meet their enterprise needs and then add new policies via Group Policy for distribution to servers.
The SCM tool supports not only Active Directory servers but standalone servers as well. SCM also offers a command-line tool that administrators can use to harden servers through batch files.
Free Tool
Microsoft provides SCM for free [1]. After you install the tool, import the existing group policies from Active Directory and compare the settings in your policies with the configuration recommendations from SCM. You can then import the custom policies back into Active Directory. If you are not currently using group policies, you can create new policies easily with SCM or secure individual servers with SCM via local security policies.
SCM helps protect Windows Server 2003/2008/2008 R2, as well as the client operating systems Windows XP/Vista and Windows 7, including Service Pack 1. Version 2.5 of SCM still lacks the support for Windows 8 and Windows Server 2012, but by the time these operating systems are released in the last quarter of 2012, Microsoft will probably have an updated version of SCM on offer. Additionally, SCM protects Internet Explorer 8/9, Office 2007/2010, and Exchange Server 2007/2010, including the latest service packs – above all for Exchange Server 2010 SP2.
Admins can easily run SCM on their own workstations (Figure 1); however, they must have a 64-bit version of Windows 7 installed. If they later want to export the SCM settings to an Excel sheet, they must have Excel 2007/2010 on the corresponding computer. This is optional and only necessary if they want to import various settings from SCM into Excel.
SCM Hands On
SCM requires .NET Framework 4.0 [2]. The free SQL Server 2008 R2 Express Edition database [3] is also required on the server. You should install these dependencies before SCM. Use the default settings for both when you install. SCM stores its configuration data, baselines, settings, and documentation in SQL Server 2008 R2.
The next step is to install SCM on a workstation or a server. After the installation, the SCM management tool is available. When first started, the tool reads the corresponding configuration recommendations, known as baselines, for the server systems and starts the SCM management interface. On the left, you can select the recommendations (baselines); in the center, you create and change settings. On the right, you'll find actions for saving the templates and importing them into group policies.
Updating SCM baselines via the Internet at regular intervals is a good idea. To do so, use the Download Microsoft baselines manually link on the SCM welcome screen. The tool opens Internet Explorer and suggests new baselines for installation. A Microsoft site [4] lets you download and integrate baselines manually in SCM.
Editing Baselines
On the left side of the Manager are various baseline recommendations. To modify servers or programs to create your own policies, click on the baseline you want to use and, on the right, select the Duplicate action under the Baseline section. The duplicated template already contains the settings and recommendations from Microsoft. The next step is to adapt the settings in your new baseline to match your needs.
When the settings are complete, you need to export them. Various options are available to do so. The best approach for the export action is to create a Group Policy Object (GPO) backup folder. In this way, you can import the backup as a new Group Policy on the network in Group Policy Manager – although importing the policy does not apply the settings. For that, you need to assign the new policy to an organizational unit or domain. The imported settings are effectively a normal Group Policy.
After exporting the baseline as a GPO backup, copy it to a domain controller or use the Group Policy Manager on the local workstation. To do this, you must install the appropriate Remote Server Administration Tools.
The settings can also be imported as templates in System Center Configuration Manager. Companies that use System Center can thus integrate SCM directly, but integration via a Group Policy backup works just as well. You can compare and merge settings from different baselines using the Compare/Merge menu item.
After selecting the policies, you can compare them or merge them to create a new policy. In this way, you can also compare baselines that you edited yourself with the default baselines and see the changes you have made at a glance. The results of the comparisons can be exported to Excel, thus making it easier to see differences. This process is useful, for example, if you import a *.CAB file provided by another SCM installation.
Expanding Baselines
Besides using Microsoft recommendations in a baseline or modifying existing settings, you can integrate and configure settings from other baselines. For example, you could add settings from Office 2010 to an Exchange policy to manage Outlook settings on Exchange servers. To add more settings to a baseline, click Add below Setting. You can remove settings with Delete. To view the new settings in a group, use Add in Setting Group to create new groups of settings.
Editing and Documenting Baselines
Once you have created the baselines and started editing, you will find multiple columns at the center of the screen that let you specify the settings (Figure 2). On the far left is the name of the setting. The Default column contains the default settings for the corresponding server system. The Microsoft column displays the Microsoft recommendations. If you change the settings, they appear in the Customized column. The Severity column shows the importance that Microsoft attaches to the corresponding setting. The last column, Path, indicates where the setting is located in the registry or whether the setting is set via the PowerShell.
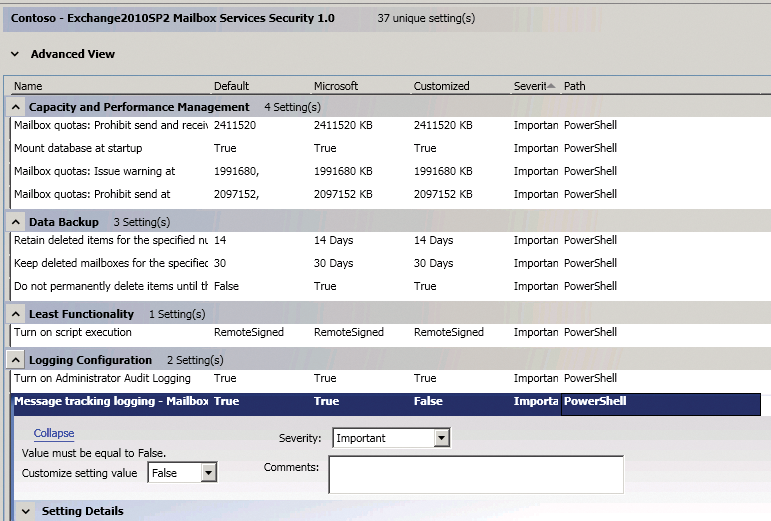
If you have created your own baselines, they appear in the Custom Baselines section on the left side along with the new Attachments\Guides menu item.
This section lets you append your own documentation, tools, and information to baselines, as necessary for implementation. Attachments can be printed, viewed, exported, saved, or viewed directly. SCM 2.5 supports the following file formats: .cab, .doc, .docx, .mp, .rtf, .txt, .url, .xls, .xlsx, .xlsm, .zip.
To protect a baseline against unwanted changes after its completion, select the menu item Lock in the action pane. This action prevents changes to this baseline, but you can re-enable editing at any time via Edit. All changes you make into baselines in SCM are logged. To open the log file, select View | Baseline Change Log. The window shows all the actions you have made in SCM, including changes to the baselines.
Exporting and Importing Settings
Once you have completed all the settings in one or more baselines, you can select the Export section on the right and choose how you want to roll out these settings to your servers or document the settings. The following options are available:
- Excel: The tool creates a XLSM file compatible with Excel 2007/2010. You can also use the file for other purposes; you do not necessarily have to install SCM on the target computer.
- GPO Backup: The backup creates a directory with a GPO backup of the baseline. You can import this back into your production environment just like a normal Group Policy. To do this, create a new Group Policy in Active Directory and restore the settings from the GPO backup in the new backup.
- SCAP: This option creates a file on the basis of the Security Content Automation Protocol (SCAP). This option can also be used on other systems.
- SCCM DCM: The tool creates packages that are compatible with Microsoft System Center Configuration Manager. They can be used to monitor and configure the connected target computers.
- SCM: This option creates a CAB file, which you can import into another SCM installation where you can edit it further.
After creating a SCM-compatible export, although you cannot use these settings for importing Group Policies, you can import the settings back into the SCM interface and edit them again. Start the import either in the Import menu on the right-hand side, or press the keyboard shortcut Ctrl+I. In the Import Baselines Wizard, select the package you want to import. When you click Next, the wizard reads the data and shows the integrated baselines. Clicking on Import tells the wizard to integrate the baselines in the CAB file in SCM on the local computer. In this section, you can also import Group Policy backups. To do so, select the Import | GPO Backup (folder) option.
Settings
Active Directory is not necessary for securing Windows Server with SCM; the settings also can be programmed in local policies. SCM provides the LocalGPO command-line tool for this purpose. The tool from the Microsoft Security Compliance Manager program group lets you import settings locally from SCM into a policy on the server. The tool provides various options for the import process. LocalGPO is especially intended for servers that do not have a domain assignment. The first step is to install the tool on the server; you then import the settings at the command line.
After installation, launch LocalGPO Command-line in the LocalGPO program group. To import the settings from a SCM baseline onto the local server, you must first create the baseline, as previously described. Next, export this as a GPO backup to a directory. Copy the directory to the server on which you want to implement the policies. Then, type the command
cscript LocalGPO.wsf /path:<path to GPO backup>
(Figure 3). When transferring the new settings, LocalGPO saves the settings in the local policy. You can restore the policy at any time. To restore the original settings on the server, use the command:
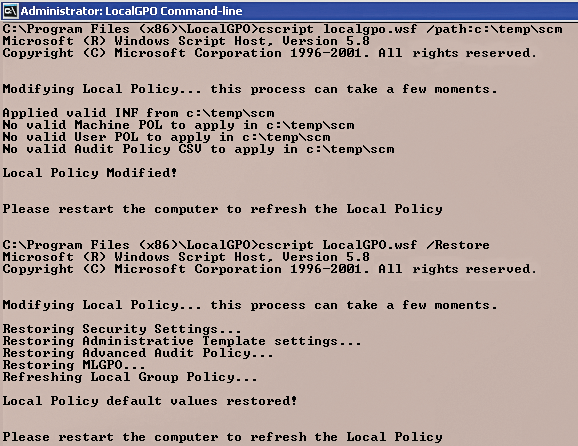
cscript LocalGPO.wsf /Restore
LocalGPO also lets you back up local security policy settings in a GPO backup, and you can use this for a restore by reimporting it to the server. Additionally, you can import the backup on other local servers, and it is possible to create a new Active Directory Group Policy on the basis of a backup and to import the policy. To do this, use the command:
cscript LocalGPO.wsf /path: <path> /Export
You can import this backup with LocalGPO, or you can use the Group Policy Management Console. Moreover, you can export the local security policy on a server to a GPOPack, which lets you import the security settings on another server without having to install LocalGPO on the target system. To do this, use the command:
cscript LocalGPO.wsf /path: "<path>" /Export /GPOPack
For more details on this subject, visit the website [5].
