
Better Active Directory with Windows Server 2012
Refurbished
Active Directory is the heart of most Windows networks, and now a new version of Windows Server 2012 brings several improvements over the previous version. One important advantage is the easy virtualization of domain controllers. And, making snapshots of domain controllers is no longer a problem either (see the article on Hyper-V 3.0 in this issue). VMware and other virtualization vendors likely will upgrade soon to include easy virtualization of domain controllers with Windows Server 2012.
Managed Service Accounts (MSAs) that automatically manage passwords for services can be shared on multiple Windows Server 2012 systems as group MSAs (gMSAs). DHCP servers can be grouped into teams, even without clusters. Windows Server 2012 has retained the command line, but the server and the Windows 8 client now both include the new PowerShell version 3.0, which is much easier to use than its predecessor in Windows Server 2008 R2.
Using Dynamic Access Control, administrators can more easily control permissions for access to files, folders, and even SharePoint libraries. Files can be assigned metadata that only permits access for certain users (e.g., the staff of a department or the management), regardless of the directory they are saved into or the sharing options they have been saved with. This all works smoothly, even when files in SharePoint libraries are moved. And, with Active Directory Rights Management Services, you can set which devices are allowed to access the data. Insecure PCs, home offices, computers in Internet cafés, or smartphones can be locked out.
Virtualizing Domain Controllers
In the future, domain controllers will be easier to install and manage. For this purpose, Microsoft has implemented server groups in the new Server Manager (Figure 1).
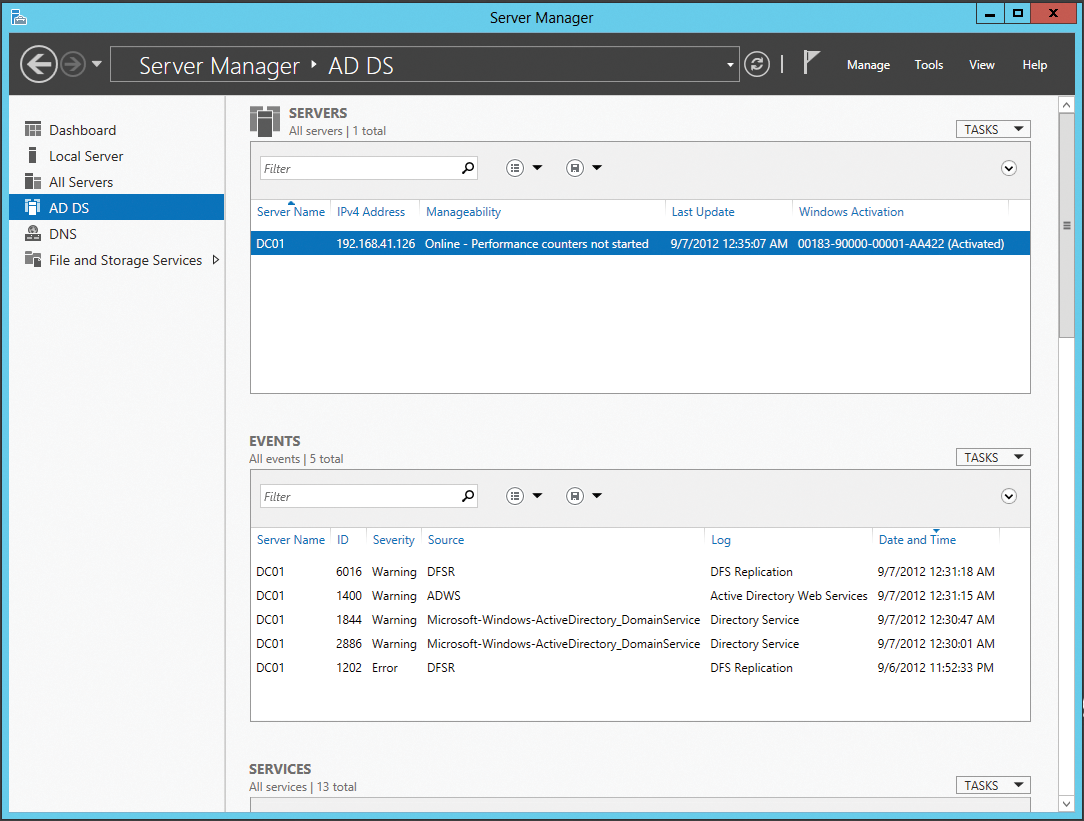
As a result, administrators can manage all servers in the network centrally with on-board tools and install server roles and features over the network.
The new version, for example, makes it possible to activate and use the Active Directory recycle bin, as well as to complete other tasks that had to be done with PowerShell in Windows Server 2008 R2.
The new group policies for passwords can also be configured in the new console and assigned to organizational units. In the lower area of the Active Directory Administrative Center, the new Windows PowerShell history logs the PowerShell commands that have been executed. Thus, administrators only need to click the link to see all tasks executed as PowerShell commands are displayed on the graphical interface, ready to be copied as needed.
To install Active Directory, administrators select Active Directory Domain Services as the server role. After the necessary system files have been installed, the setup wizard, which Microsoft has thoroughly revised, can be started via a link in the final window. Dcpromo, the installation wizard in previous versions, no longer exists.
Easier Replication
The Active Directory Administrative Center, introduced in Windows Server 2008 R2, which Microsoft has thoroughly revised in Windows Server 2012, is the command room for all routine tasks in Active Directory (Figure 2). The structure of the console is very task oriented. In contrast to the other management tools, the tasks in the Administrative Center are based on PowerShell commands.
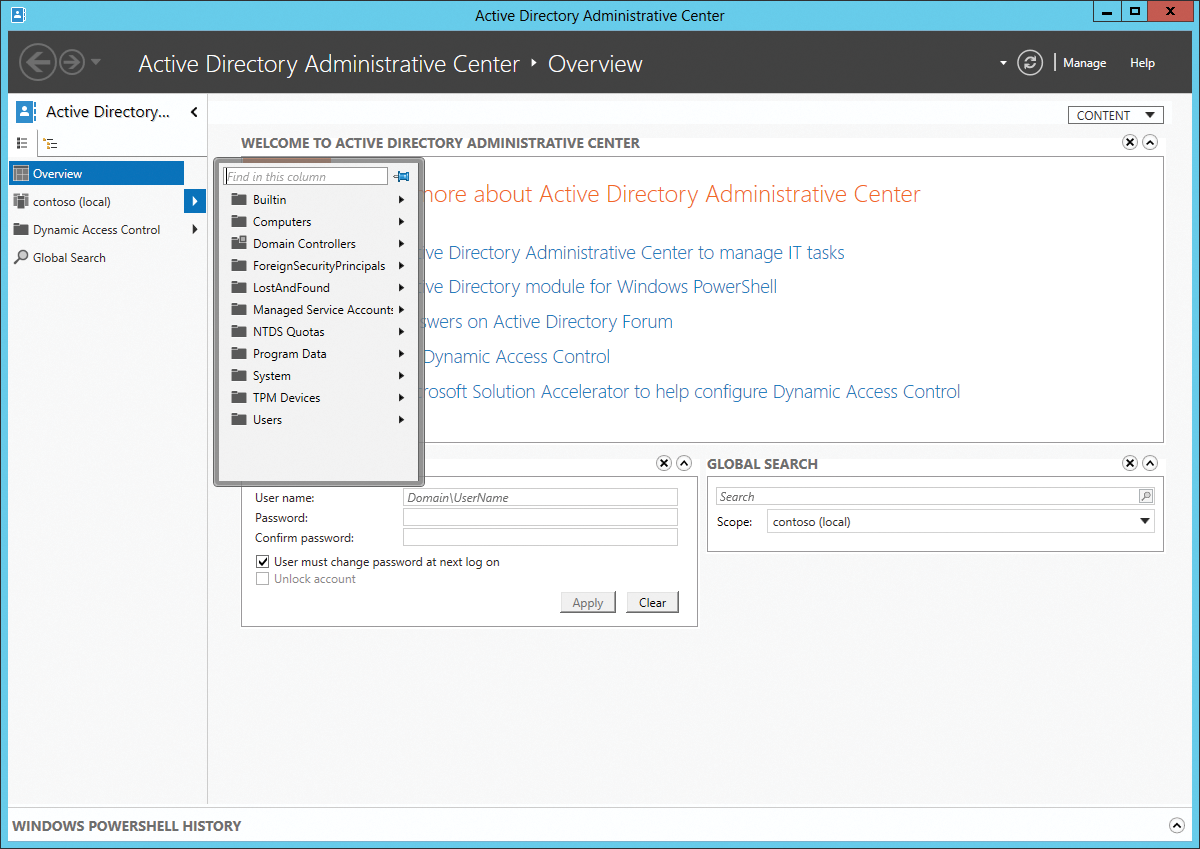
The standard management consoles for Active Directory (e.g., Active Directory Users and Computers) are still available. Compared with Windows Server 2008 R2, no large changes have been made here or to the Active Directory Sites and Services and Active Directory Domains and Trusts snap-ins.
The Active Directory Administrative Center does not offer all the possibilities of the other snap-ins; usually it is used for routine tasks such as resetting passwords or creating new objects. When admins create new objects such as organizational units or user accounts, the Administrative Center provides uncluttered and easy-to-understand forms. The tool connects to the Active Directory through Active Directory Web Services.
Administrators start the Active Directory Administrative Center either in the Tools program group in the Server Manager, or by entering dsac in PowerShell or on the command line. On the left side of the console, you can navigate through the domains and organizational units. In the upper left area, you can choose between a tree structure, as in Active Directory User Management, and a structure similar to the Start menu.
When you select an organizational unit (OU) in the list view, its content can be pinned to the launch window of the Administrative Center, so it will appear there permanently. You only need to click on the blue pushpin icon at the top right. Another click on the pin reverses the process.
The Global Search section allows searches for objects in all domains in the forest, independent of the domain to which the Administrative Center is currently connected. The navigation area of the AD Administrative Center can be customized at any time by taking different containers from any domain and adding them as separate nodes. The list of recently used objects is automatically displayed under a navigation node.
Management Tools
Because the Start menu is missing in Windows Server 2012, admins must start the management tools another way. The central management tool in Windows Server 2012 is the Server Manager. An overview of the various server groups is shown here, including the Active Directory Domain Services. A click on AD DS lists all domain controllers that can be managed here. A summary of all messages from all event logs is also shown.
To integrate a server into the Server Manager of Windows Server 2012, just click on Manage | Add Server. In that window, you can then search for servers to integrate them for management in the local Server Manager. To install remote roles or features on servers in the network with the Server Manager, it is not necessary to integrate them first. In the wizard for adding other roles, a new window will appear in which you can select the server on which a new role or feature is to be installed.
The wizards for adding roles and features have been merged into one wizard. From the context menu of a server, administrators can restart the server remotely over the network, start a PowerShell session on the server, or open an RDP connection. Installation of roles and features over the network is also possible via context menus. The Service Center symbol in the upper area of the Server Manager shows whether an error has occurred on a connected server or whether management measures are necessary. However, only machines with Windows Server 2012 can be managed centrally in this way. Windows Server 2008 R2 cannot be connected to the Server Manager of Windows Server 2012.
The most important management tools can now be found directly in the Server Manager without taking any detours. Just click on Tools at the top right. The Windows key calls up the Windows Server 2012 home screen view. With it, you can also start and search for administration tools. In Windows 8 and Windows Server 2012, the keyboard shortcut Windows+X also calls up important administration tools at the bottom left. Another new and interesting shortcut is Windows+Print, which automatically creates a screenshot and stores it in the image library. Administrators can start the desktop immediately with Windows+D.
PowerShell 3.0 and Active Directory
Windows Server 2012 can also be managed in PowerShell. Microsoft has integrated some new commandlets for this, which can be seen in Windows Server 2012 after the appropriate module has been loaded in PowerShell 3.0 with Import-Module ADDSDeployment. The commands can then be called up with
get-command *adds*
The Install-ADDSDomainController commandlet installs a new domain controller in an existing domain (Figure 3). Install-ADDSDomain installs a new domain and Install-ADDSForest a new forest. The commandlet Uninstall-ADDSDomainController can demote a domain controller. The commandlets ask for all necessary options and restart the server. Further configurations (e.g., for DNS or global catalog servers) then follow without the wizard. New commandlets for Active Directory include:
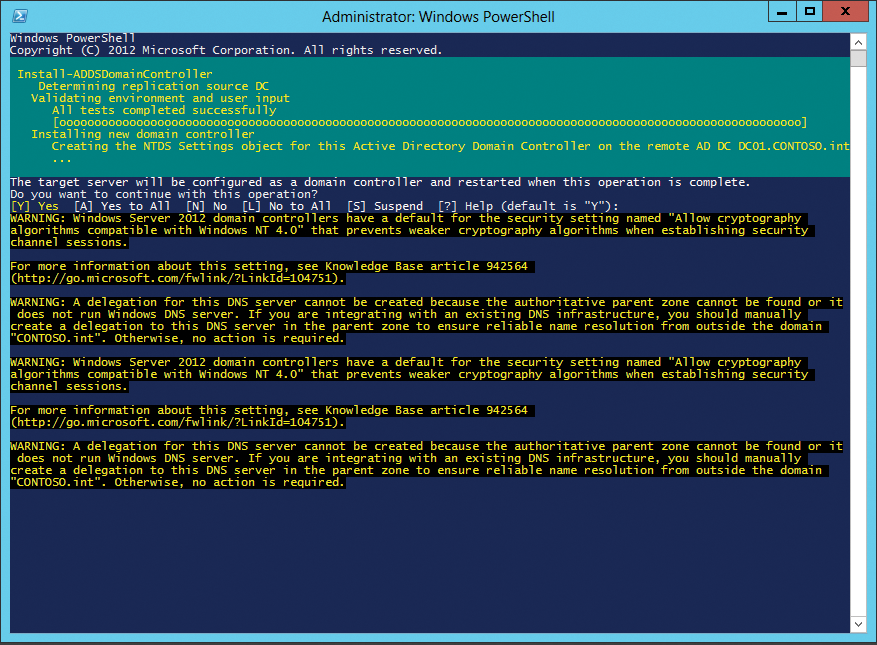
Test-ADDSDomainControllerInstallation Test-ADDSDomainControllerUnInstallation Test-ADDSDomainInstallation Test-ADDSForestInstallation Test-ADDSReadOnlyDomainControllerUnInstallation
Migration
If you want to update a domain controller to Windows Server 2012, you must first extend the schema of the forest. For this, execute the
adprep /forestprep
command on a domain controller. The tool is found in the support\adprep directory on the Windows Server 2012 DVD. To extend the schema, you must first confirm the extension with c. However, these measures should not be performed in production environments because the changes cannot be undone. After the schema has been updated, typing
adprep /domainprep
updates the individual domains.
Newly installed domain controllers can be added easily to the Active Directory. Member servers with Windows Server 2012 can also be added to existing domains, if domain controllers with Windows Server 2003/2003 R2/2008/2008 R2 are present. The operations master roles from migrations of previous versions can be transferred to the new domain controller with Windows Server 2012.
New DNS System
Because the servers are so closely dovetailed with each other, an improvement of the DNS system is also necessary (e.g., for security aspects). Microsoft had already introduced DNSSEC with Windows Server 2008 R2 to protect zones and entries. The grouping of DNS servers in the Server Manager of Windows Server 2012 makes managing them much more efficient.
In Windows Server 2012, zones can be signed digitally online. DNSSEC can be integrated completely into the Active Directory in the new version and includes the ability to activate dynamic updates for secured zones. Windows Server 2012 supports official standards, such as NSEC3 and RSA/SHA-2.
Support for DNSSEC on read-only domain controllers (RODCs) is also new. If an RODC with Windows Server 2012 finds a signed DNS zone, it automatically makes a secondary copy of the zone and transmits the data of the DNSSEC-secured zone. The advantage is that offices with RODCs can resolve secured data, but the signature and data of the zone are not endangered.
DNSSEC can be set up via the context menu of a zone. It is no longer necessary to complete a complicated configuration at the command line or take zones offline. Zone signing is done with the help of a wizard that allows manual signing, signature updates, and signature creation on the basis of automatic settings.
Windows Server 2012 also makes it possible to replicate signed zones on other DNS servers on the network. A further innovation is the IP Address Management (IPAM) server, which monitors and centrally manages the DHCP and DNS services. Installation is done as a server role.
Remote Management
Administrators can access servers for remote management of Active Directory domain controllers either via remote desktop or from their own workstation with PowerShell. In addition to PowerShell, other tools for managing Active Directory on workstations are also available and work with Windows 7 and Windows Server 2008 R2, as well as with Windows 8 and Windows Server 2012. If you want to manage Windows Server 2012 from workstations with Windows 8, you must first install the Remote Server Administration Tools for Windows 8 [1].
The management tools for Active Directory can be found under Role Management Tools | AD DS | AD LDS Tools. The commandlets for managing Active Directory are available here (e.g., the Active Directory module for Windows PowerShell). In Windows 8, the remote management tools are already activated. If these are not seen immediately on the start page, the "All Apps" view can be called up with the Ctrl+Tab keyboard shortcut. In Windows 7, the tools are found in the normal Start menu.
If you want to manage a server running Windows Server 2008 R2 or 2012 services that are not activated, you can also install the management tools there. No patches are necessary, and the corresponding tools can be activated directly in the Server Manager.
Installation is done in the Server Manager under Features | Add Features | Remote Server Management Tools | Role Management Tools.
In Windows Server 2012, they can be reached under Management | Add Roles and Features. Administrators can also perform the installation of the management tools on servers using PowerShell.
For this, you can download the appropriate commandlets for server management with Import-Module Server Manager. The command Get-WindowsFeature displays the available features. The installation of features is then completed with the Add-WindowsFeature <Features> command, for example:
Add-WindowsFeature RSAT-AD-PowerShell,RSAT-AD-AdminCenter
These commands work in PowerShell 2.0 of Windows Server 2008 R2 and in the new PowerShell 3.0 of Windows Server 2012.
PowerShell in the Network
To manage a server remotely via PowerShell, remote management must be activated on the server with the Enable-PSRemoting -force command, which also configures the Windows Firewall. Disable-PSRemoting -force will then deactivate remote management of a server on the PowerShell.
In remote PowerShell sessions, you can use same commandlets that are used on local servers. However, not all commandlets allow remote management, and this depends on whether the commandlet supports the -Computer Name option. You can use the
Get-Help * -Parameter ComputerName
command to call up a list of all these commandlets.
If the help commandlet is called up, PowerShell can update itself, as was possible in PowerShell 2.0 if the -online option was used with the get-help commandlet. PowerShell 3.0 offers the new update-help commandlet, which updates the help files. The command calls up help directly from the Internet.
Another new feature in PowerShell 3.0 is the show-command commandlet, which opens a new window with all the PowerShell commands that are available (Figure 4).
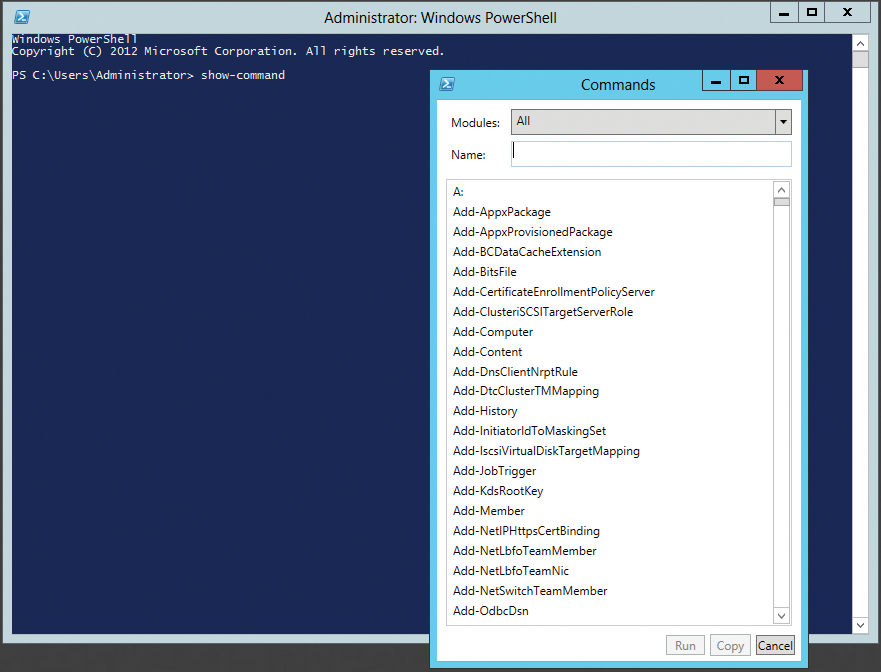
PowerShell can also start a remote session on a server. This works best with the PowerShell Integrated Script Engine (ISE), which is already activated in Windows 8. In Windows 7, it must be activated manually. Once started, a connection can be opened with File | New Remote PowerShell Tab; then, you can enter the name of the server and user with which you would like to connect.
