
Controlling virtual machines with VNC and Spice
Well Seasoned
For graphical output to work on KVM-based virtual machines, several pieces of a puzzle need to fit. For one thing, KVM needs to provide a graphics adapter to the underlying QEMU system on the virtual machine. By default, a (legacy) Cirrus graphics card is emulated. If you need a resolution above 1024x768 pixels, other virtual graphics cards are available; however, on Linux guests, this setup often means a manual X configuration.
Additionally, you must consider which protocol you should use to transfer the graphical data from the virtual machine to the client. VNC is the standard choice for a remote desktop protocol; it is widespread beyond the world of Linux and causes the least problems in production use. One alternative to VNC, however, is the new Spice protocol, which promises superior speed and a number of additional features.
The Virtual Graphics Adapter
For the virtual machine to see a graphics system, QEMU emulates a graphics card. In combination with KVM, you have a choice of four models:
-
cirrus: This graphics card is correctly detected by just about any guest system and offers acceptable speed with no configuration overhead. However, the maximum resolution is 1024x768 pixels. -
vga: The benefit of this virtual graphics card is that it supports far higher resolutions (tested up to 2560x1600 pixels). The graphics card is correctly detected on Windows, but some manual configuration work is necessary on Linux. You need to set up the Vesa driver explicitly inxorg.conf(Listing 1).
Listing 1: Vesa Configuration
01 Section "Device" 02 Identifier "device0" 03 Driver "vesa" 04 EndSection
-
vmvga: This graphics card has been used for many years by various VMware products. The matching open source graphics drivers are available out of the box with some Linux distributions. If this is the case with your distribution, the VMware graphics card is a good choice. It supports high resolutions on the virtual machine without any major configuration overhead. -
qxl: This graphics card can only be used in combination with Spice.
In the Virtual Machine Manager, you can set the desired graphics adapter in the virtual machine's detailed view Video section. The xen graphics adapter cannot be used with KVM. (The Virtual Machine Manager is only suitable for managing virtual Xen machines that support this graphics adapter.) The qxl graphics adapter is available only if you select the Spice protocol in the Display tab.
VNC Desktop
VNC stands for Virtual Network Computing and gives users the ability to display the screen content of another machine, including virtual machines, in a window (the VNC Viewer or VNC Client). At the same time, VNC passes local keyboard and mouse input through to the virtual machine.
To be able to use VNC to control a virtual machine, qemu-kvm runs a VNC server, thus making the content of the virtual graphics adapter available on the network. The VNC server can only be addressed on 127.0.0.1 by default for security reasons. The Virtual Machine Manager takes the settings of the Libvirt configuration file into consideration; you can also set a VNC password here. However, VNC is a relatively insecure protocol, and using a VNC password will not do much to change this.
# File /etc/libvirt/qemu.conf ... vnc_listen = "127.0.0.1" vnc_password = "topSecret"
To control the virtual machine, you need to run a VNC client on the local machine. You will typically want to use the console window of the Virtual Machine Manager for this. Alternatively, you could use the vncviewer, vinagre, or virt-viewer programs.
By default, the first virtual machine to launch uses port 5900, the second port 5901, and so on. If you do not work with Virtual Machine Manager, you can determined the display number with the vncdisplay Virsh command. To find the right port number, just add 5900:
root# virsh list Id Name Status ---------------------------------- 7 centos running 8 fedora running root# virsh vncdisplay 8 :1
The VNC client integrated into Virtual Machine Manager, or virt-viewer, transfers keyboard input in the form of RAW code. If the host and guest system use the same keyboard layout, you will not experience any mapping problems.
Other VNC clients always transfer keyboard input to reflect the US layout. If this is a problem for you, you need to go to the Virtual Machine Manager's detailed view (Display tab) and select the keyboard layout that you need. It is stored in the XML file on the virtual machine:
# in /etc/libvirt/qemu/vmname.xml ... <graphics type='vnc' port='-1' autoport='yes' keymap='de'/>
using the keymap attribute as shown.
VNC on the Network
By default, the VNC server in qemu-kvm is only accessible on the KVM host. To control a virtual machine on a different machine, you have various options. One variant is to bind the VNC server to the 0.0.0.0 address (vnc_listen=0.0.0.0 in /etc/libvirt/qemu.conf). You should only use this simple solution in a secure lab environment. On Fedora and RHEL, the firewall, which is enabled by default, will also prevent any external VNC connections.
Port Forwarding
A far superior solution is to leave the default VNC configuration. But, to be able to use VNC to access the virtual machine from an external machine, you need to use SSH port forwarding. This approach removes the need to modify the firewall on the host computer. The only prerequisite is that an SSH server must be running on the KVM host. This is the default for Virtual Machine Manager if you are controlling virtual machines running on a different host.
On Fedora (but strangely not on RHEL), SSH port forwarding is blocked by an SELinux rule. If you use Fedora as your KVM host and want to use SSH and VNC to control your virtual machines on some other machine, you need to explicitly allow port forwarding on the KVM host. To do so, you can run this command:
root# setsebool -P sshd_forward_ports 1
A third variant is to encrypt VNC communication with TSL via the /etc/libvirt/qemu.conf configuration file. This assumes a TSL-compatible VNC viewer. Tips for configuring this correctly are available online [1].
Spice
The Simple Protocol for Independent Computing Environments (Spice, for short) is a new protocol for controlling virtual machines efficiently over a network. Spice supports image compression, video streaming, audio transmission, OpenSSL encryption, and much more. Communication between the host and guest systems relies on Virtual Device Interfaces (VDIs). Using Spice means access to nearly unlimited graphics resolutions on the virtual machine.
Spice with Sound
Compared with VNC, Spice is not just more efficient, it also offers the benefit of audio support. If you want to listen to the audio output from a virtual machine, Spice is currently your only option. Although VNC basically supports audio transmission, the VNC clients available on Linux are not capable of doing this.
Spice was originally developed by Qumranet, like KVM. After Red Hat acquired Qumranet in 2008, it released Spice as an open source project at the end of 2009. The Spice project is basically independent of KVM but is currently only used in combination with KVM or QEMU. From a technology point of view, Spice is similar to the Virtio drivers: Spice requires you to use paravirtualized drivers on the virtual machines.
Layer Cake
Spice comprises three components:
- The Spice server is indicated directly in QEMU/KVM. It is responsible for external communication – that is, for letting the user control the virtual machine across a network connection. For the virtual machine, the Spice server looks like a VGA graphics card.
- The Spice client (on current distributions, this is the
spicycommand from thespice-gtk-toolspackage; on older distributions, thespiceccommand from thespice-clientpackage) is comparable to a VNC viewer, which displays the graphics system from the virtual machine in a window. Current versions of the Virtual Machine Managers, fromvirt-viewerorvinagre, are also Spice compatible. The Spice client is also available as a Windows program. - The QXL driver is installed on the virtual machine and ensures that the virtual machine supports the graphics system efficiently and with high resolutions. The QXL driver is currently available both for X (Linux) and for Windows. Spice also works without the QXL driver; however, only with resolutions of up to 1024x768 pixels on the virtual machine. Additionally, Spice then offers no speed benefits compared with other graphics solutions.
With current versions of RHEL or Fedora, you can use Spice directly with Virtual Machine Manager: To do so, set Type = Spice in the Display tab of the detailed view. Additionally, you need to set Model = qxl in the Video tab. After starting, the graphics system is displayed in the normal way in the Virtual Machine Manager's console window. From a purely visual point of view, you will not notice any difference from VNC.
For optimum support of QXL by the guest, you need to install a QXL driver on the guest. On current Linux distributions, this is often the default. On some Linux distributions, you will need to install the QXL driver package yourself (i.e., xserver-xorg-video-qxl or xorg-x11-drv-qxl). If the driver is not automatically enabled the next time you start X, add the following lines to /etc/X11/xorg.conf or /etc/X11/xorg.conf.d/spice.conf on the guest:
Section "Device" Identifier "device0" Driver "qxl" EndSection
On the network, the same rules basically apply for Spice as for VNC: Libvirt assigns the Spice server on a newly launched virtual machine the first free port above 5900 and an IP address of 127.0.0.1 by default. You can change various global Spice settings for the Libvirt tools in /etc/libvirt/qemu.conf.
On Fedora and RHEL, the firewall, which is enabled by default, blocks external Spice connections. To change this, use SSH with port forwarding as for a VNC connection, or add an exception to your firewall ruleset. You will find predefined rules in the Other Ports tab of the firewall configuration program.
Spice up your Ubuntu
The best Spice support is available with the Fedora and RHEL Linux distributions. Ubuntu, as of Version 12.04 at least, provides a Spice-compatible version of QEMU/KVM. To use the Spice-ready version, you will need to install the required packages manually:
apt-get install qemu-kvm-spice spice-client-gtkpython-spice-client-gtk
On Ubuntu 12.04, use of Spice in the Virtual Machine Manager fails because the program does not call the Spice variant of qemu-kvm. On Ubuntu, the Spice support resides in a separate program (qemu-kvm-spice). Thus, the only way to use Spice in Ubuntu 12.04 is at the command line.
The Virt-manager version on Ubuntu 12.10 has a better configuration, so at least everything works on the host side. An attempt to run Ubuntu 12.10 Beta 2 as a guest on a virtual machine with Spice and QXL graphics failed because of an issue with the QXL driver (at least the driver is enabled). Whether this bug (Launchpad #1056381) will be fully addressed in Ubuntu 12.10 is still not clear at the time I am writing this article.
Windows
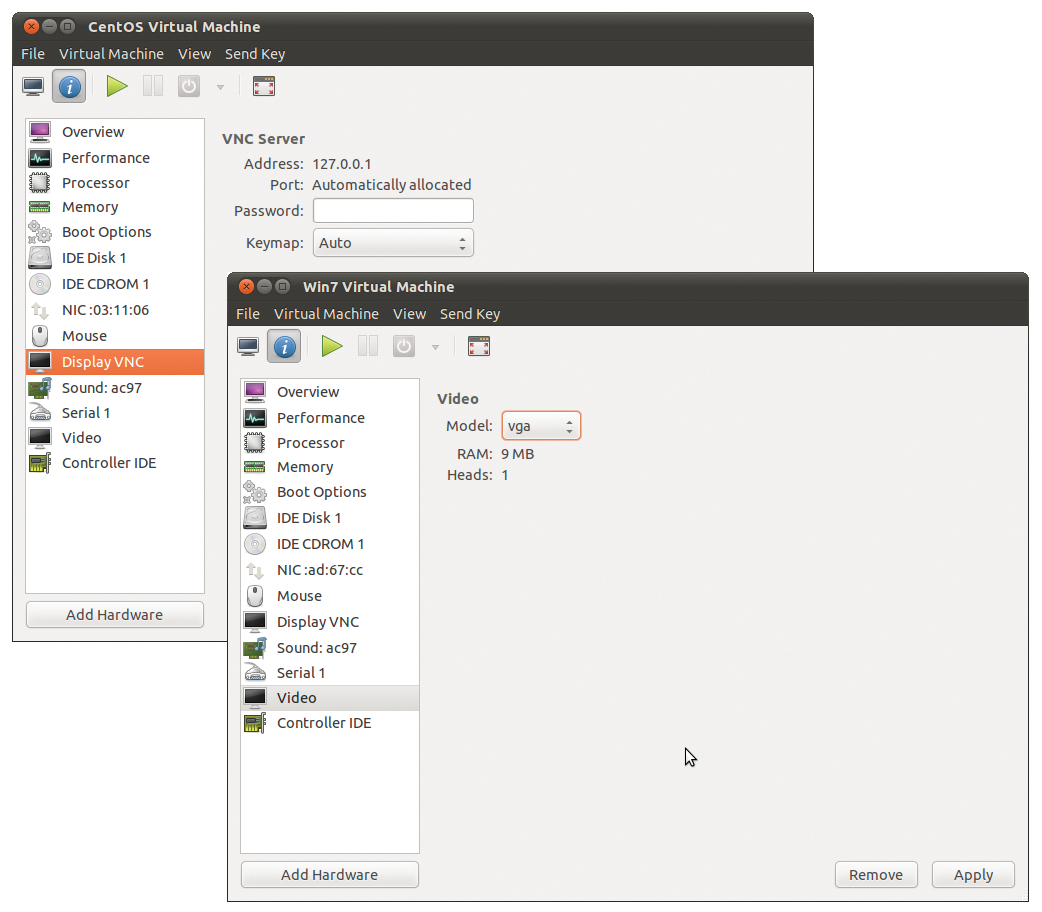
The previous examples all assumed that a Linux distribution was running on the virtual machines. However, KVM is also Windows compatible. Virtual Machine Manager automatically selects the vga graphics driver for Windows guests (Figure 1). This is a good choice: Both Windows XP and Windows 7 have no problems with the driver and support virtually unlimited resolutions (tested up to 2560x1600). On Windows 7, you will need to do without the Aero effects.
Theoretically, you could use Spice for Windows guests. QXL Windows drivers are available online [2] (search for "windows guest tools").
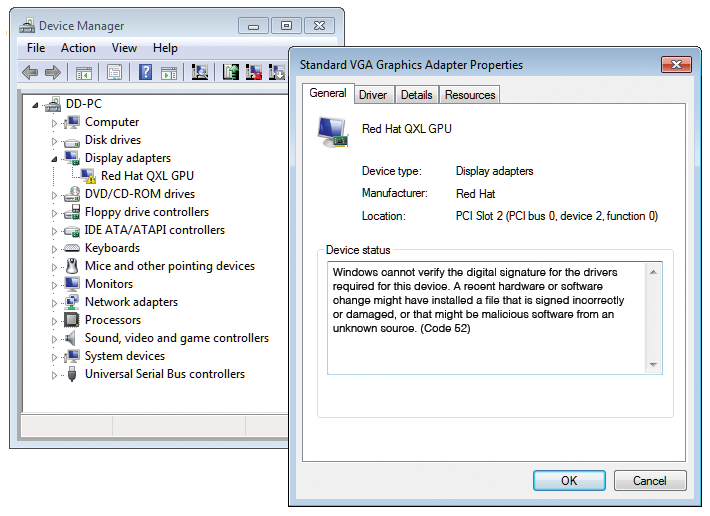
In practical terms, QXL driver 0.1 on Windows 7 fails because of signature issues (Figure 2). The Device Manager tells you that the driver is not correctly signed (Error 52).
Conclusions
The graphics system plays a subordinate role in server use scenarios; in fact, the GUI on a server system is primarily used for the installation. The situation is totally different when KVM is used for desktop virtualization, where the new Spice protocol has obvious benefits compared with VNC. Unfortunately, Spice does not work out of the box with all distributions. The use of Spice is well supported on Fedora and RHEL. But both VNC and Spice reach their limits if you need 3D graphics. In contrast to VMware or VirtualBox, KVM does not currently give users an option of outsourcing 3D functions to the virtual machine.
