
Smartphone management with Microsoft products
On a Leash
Companies that want to integrate their users' smartphones into their existing infrastructure can do so with various Microsoft products. One example is System Center Configuration Manager (SCCM) 2012. However, this product only does a reasonably good job of managing Apple iPhones and Android devices [1] as of Service Pack 1 (SP1). For Windows Phone and Windows 8 RT, too, the use of SCCM 2012 SP1 is required. Companies that use Exchange Server 2010 can specify settings for smartphones without this management software.
Parallel to or as a substitute for SCCM and Exchange ActiveSync policies, administrators can also use Windows Intune for cloud-based management of mobile devices and smartphones. As of SP1 for SCCM 2012, Windows Intune and SCCM 2012 work together. Microsoft updated the cloud application to do this. To manage smartphones optimally, parallel use of both products makes sense – preferably in combination with Exchange Server 2010/2013.
System Center Configuration Manager 2012 is the most important product in the new System Center. Microsoft fully integrates the functions of the System Center Mobile Device Manager 2008 in SCCM. However, this offering was not very comprehensive without the service pack, and it only gave admins the possibility of managing devices with Windows Phone 7 and other systems.
Teamwork
As an integrated solution, Windows Intune and System Center Configuration Manager improve the ability to secure and manage Windows 8 PCs, Windows RT tablets, and Windows Phone 8 smartphones. Even devices from Apple and Android-based platforms can be integrated into the management setup. If you use Windows Intune and System Center Configuration Manager 2012 SP1, you can apply the settings from Windows Intune via the management console of System Center Configuration Manager 2012.
Windows Intune lets admins centrally monitor not only computers and laptops, but also smartphones and tablets (Figure 1). In particular, businesses who rely on Windows Server 2012, Windows 8 and Windows Phone 8, or Windows RT, can thus consistently ensure that all devices that use business data are hardened against attacks.
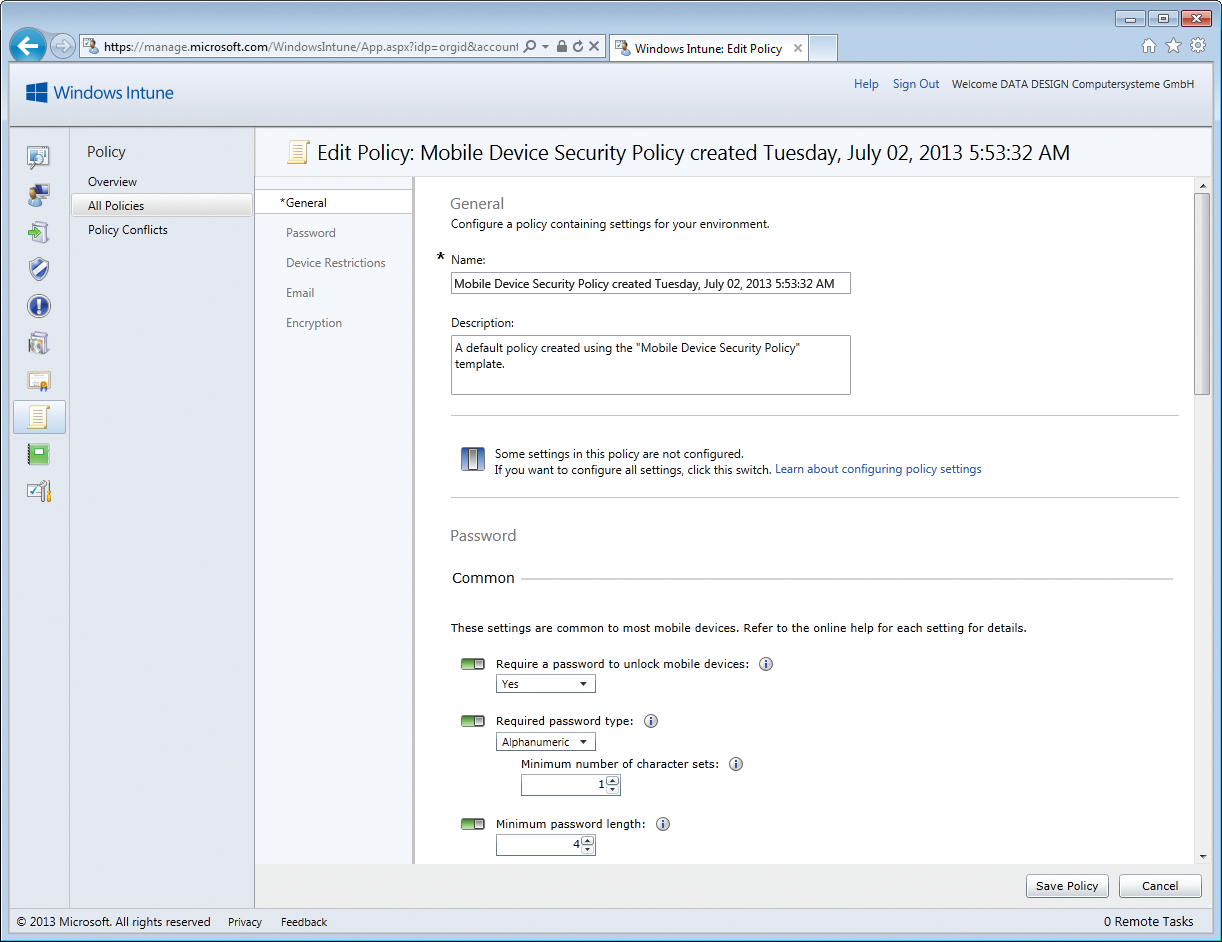
Another mainstay in the integration of mobile devices is compliance with security settings in the operating system. With Windows Intune, you can centrally define policies, for example, to manage password security. Administrators can define central settings, thus ensuring that all connected devices are configured as securely as possible.
Settings on the Web
If you use Windows Intune, you can define specific settings for Windows RT smartphones, as well as for iOS devices (e.g., iPhones and iPads) and Android devices, in the web-based management console. The web interface has special subsections for all types of smartphones (Figure 2). The Management | Mobile Device Management link takes you to the administration section where you can integrate various devices.
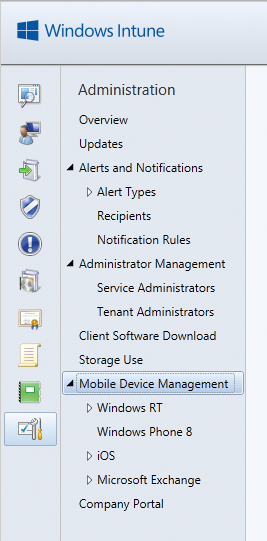
It is not surprising that Windows Phone 8 and Windows RT work best with Windows Intune and explains why there is also an enterprise app for Windows Phone [2] that gives you the best option for integrating the smartphones with Windows Intune and System Center Configuration Manager 2012 SP1. Unlike Android or Apple devices, you can use this approach to install applications on smartphones with Windows Phone 8.
At least you can register iOS devices with a certificate in the Windows Intune/SCCM portal and manage them in this way, but for Android, the only management option is via Exchange ActiveSync policies, which I describe below.
Although SCCM 2012 can also configure settings for smartphones, again, integration with Windows Intune is better suited for managing mobile devices as of SP1 for SCCM 2012. Both systems are best used in parallel. However, this does not give you the options provided by third-party products. Basically, the server mainly distributes policies, for example, if you use Exchange.
Exchange ActiveSync Mailbox Policies
In Exchange Server 2010 or in Office 365, you can use policies to define which devices are allowed to synchronize with the server and which settings must be set for the devices. Smartphones and tablets can be protected and configured here. Once a device connects to the mailbox, the server transmits the settings. Users are only allowed to synchronize their mailboxes if they have accepted the policies. That is, when using their own devices, users can decide whether they want to connect.
Exchange ActiveSync mailbox policies control the security settings on the devices. This does not help you with inventory work, but it does give a secure configuration of the endpoints. The function is integrated into all Exchange ActiveSync-compatible devices, that is, besides Windows Phone, also iPhone, Android, and Blackberry.
iPhone
To configure iPhones – currently the most widely used smartphones in the enterprise – you can use the free iPhone Configuration Utility [3]. However, you cannot transfer the settings read via a wireless connection. This means you need to transfer the policies locally or mail the files with the settings. Additionally, you cannot distribute the settings via Exchange or System Center products.
Devices that support Exchange ActiveSync implement the policies. This means not only Windows Phone 7/7.5/8, but also Blackberry, Android, and iPhones. However, policies can very easily be worked around on Android devices. The iPhone does not support all Exchange ActiveSync policy options; it only supports:
- Remote wipe
- Enforcing a code to block the device
- Minimum password length
- Minimum/maximum number of incorrect entries before the device wipes or locks itself
- Mandatory letters and numbers in passwords
- Inactivity time
- Allowing simple passwords
- Password expiration and password history
- Policy refresh interval
- Minimum number of complex characters in passwords
- Enabling or disabling the camera
You can download a PDF file from Apple that shows all the options the iPhone supports for Exchange ActiveSync [4].
The policies are configured in the Exchange Management Console via Organization Configuration | Client Access. Switch to the Exchange ActiveSync Mailbox Policies tab and select the policy you want to configure. You can assign different policies to different users (Figure 3). Once the user has confirmed the policies, the endpoint implements the settings.
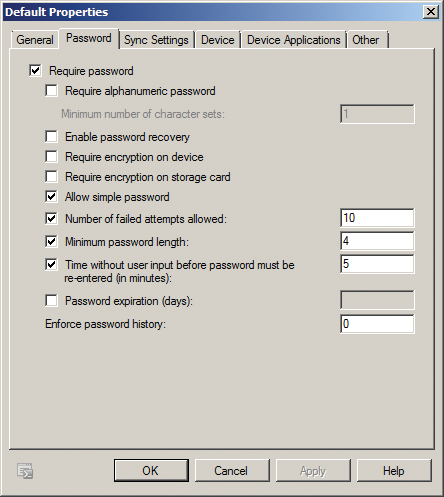
For each endpoint connect event with Exchange ActiveSync, the endpoint and the server check that the policies still match. If an administrator changes the security policy, the endpoints adopt the changes during the next sync.
Off Camera
In the Device tab, you can control smartphone features such as infrared, Bluetooth, or the camera. If you want to disable individual functions, uncheck the appropriate options:
- Allow removable storage – If disabled, the smartphone cannot access its memory card.
- Allow camera – If disabled, the built-in digital camera in the device cannot be used.
- Allow Wi-Fi – If disabled, the device cannot connect to a wireless LAN.
- Allow infrared – If disabled, the device cannot use infrared to connect to a computer or other devices.
- Allow Internet sharing from device – Internet connections are often shared if the device acts as a modem for a notebook. Uncheck this option to disable the function.
- Allow remote desktop from device – If disabled, the endpoint cannot open an RDP connection to another computer.
- Allow desktop synchronization – If disabled, the endpoint cannot synchronize with locally installed applications.
- Allow Bluetooth – By default, Bluetooth is enabled on the devices. You can either disable Bluetooth completely or set an option that only allows Bluetooth to connect to a car kit.
Besides controlling the device's hardware, you can also use policies to determine which applications are available on the device. To do this, go to the Device Applications and Other tabs. You can also use policies to specify that users need to enter a password before using the endpoint. By default, this option is not enabled, and users are allowed to use smartphones without passwords.
ActiveSync Device Access Rules
Exchange Server 2010 and Office 365 let you specify policies that determine which smartphones can synchronize with their own mailboxes off the Internet and which are blocked by Exchange. Besides the option of forwarding policies for security settings on the endpoints, you can also set policies that determine which smartphones and endpoints are allowed to connect to Exchange Server 2010 in the enterprise. These settings can be configured using ActiveSync device access rules.
The easiest way to define these settings is in the Exchange Control Panel, which you can access on https://<servername>/ecp. The settings can be found in the Exchange ActiveSync Access Settings via Phone & Voice | ActiveSync Access (Figure 4).
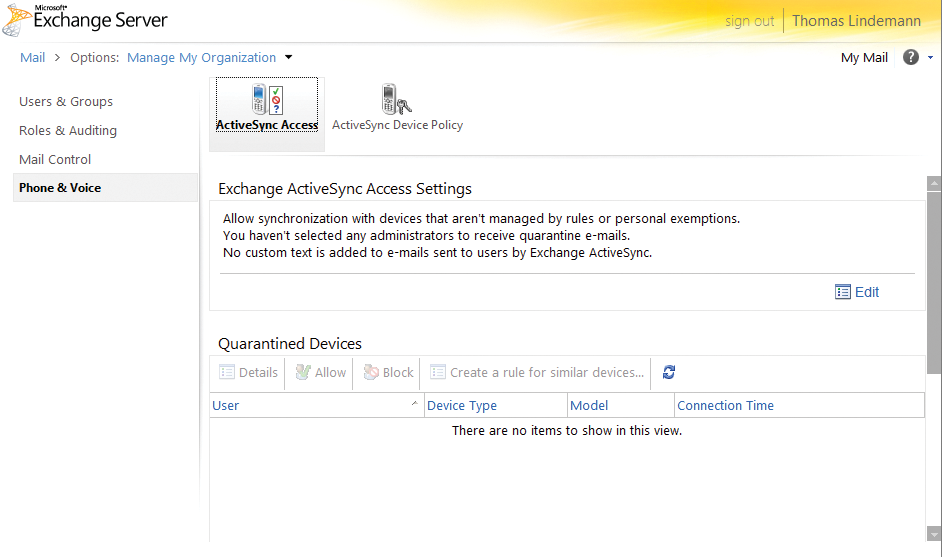
Device access rules in the ActiveSync Access section let you determine which devices you want to block or isolate. To do this, select New at the bottom of the page to create a new policy. Then, go to Device family or Only this model to determine the endpoint type you want to manage. You can press the Block Access button to block the respective devices. If Exchange blocks a new device, or quarantines it in Outlook Web App, you can enter an email text at this point. Users see this message in their mailbox when they attempt to synchronize with a blocked device.
Protocol
If you access a user's settings (e.g., in the Exchange Control Panel), you will find all the important ActiveSync settings in Phone & Voice Features. You can modify the Exchange ActiveSync policy and see the devices to which a user is already connected (Figure 5).
In this area, you can select Details to view the properties of the connected devices. Administrators see when the user synchronized for the first time and when the last sync occurred. Also, the current access status and the active policy can be seen at this point.
Devices can be enabled in this section using Allow or locked out of ActiveSync using Block. The effect is the same as the settings for ActiveSync access in the Exchange Control Panel. Create a rule for similar devices opens the same window for creating ActiveSync device policies as in the direct settings via ActiveSync Access. Finally, Wipe device deletes the data on the device.
Just as administrators can manage their users' iPhones and other smartphones, the users can do this for themselves as well. To do so, they launch the Outlook Web App (OWA), if this function is available on the Internet. Once users are logged on to OWA, they will find the Options menu for their mailbox at the top right. The management functions are in Phones | Mobile Phones, then select your device.
Selecting Display Recovery Password displays the password for which the phone prompts the user if it is locked by Exchange because of incorrect password entry attempts. However, this lock and the ability to display the password in OWA must first be activated in the Exchange ActiveSync mailbox policies and assigned to the user. Only then can the user view the recovery password.
Resetting Mobile Devices
In Exchange ActiveSync you can see all mobile devices that synchronize with the mailbox, as well as detailed information for the connection. The Wipe Device button lets the user wipe the smartphone the next time it connects to the Exchange server. Administrators can start the wipe action via the context menu of the user's mailbox by selecting Manage mobile phone.
iPhones or Android phones can connect with Exchange server using ActiveSync technology just as easily as the Windows Phone 8. Corresponding applications are preinstalled or can be easily installed. Older versions of Android do not support security policies or secure login and cannot synchronize with Exchange calendars. However, with most Android phones, you can easily synchronize the Inbox via Exchange ActiveSync. This approach also works in the standard version without any vendor changes.
Companies that use Exchange internally, would be wise to use only smartphones that support Exchange ActiveSync. For example, synchronization is much faster, more stable, and above all more reliable; no mail is lost, and users can also sync with multiple devices. From version 2.2 onward, users and administrators can also remotely wipe lost devices. Android phones need at least version 2.2 to sync Exchange calendars.
Conclusions
Companies that use smartphones from different vendors to connect to their own infrastructure and that want a Microsoft-friendly solution can either rely on the Windows Intune cloud service, the System Center Configuration Manager 2012 management solution, or Exchange. The three products also work well together. Although Microsoft has integrated the management interface of Windows Intune with System Center Configuration Manager, many different management tools are needed to connect smartphones to Exchange or Microsoft networks. Additionally, only Windows Phone devices and iPhones can be managed in a more or less meaningful way. Android devices in particular are currently not optimally supported.
Unfortunately, no useful Microsoft server solution can currently integrate and manage smartphones centrally. The functions of the now defunct System Center Mobile Device Manager 2008 may have been integrated into System Center Configuration Manager 2012, but this functionality does not add any real value for administrators. Moreover, neither SCCM nor Windows Intune actually focus on smartphones and tablets; rather, they manage notebooks, workstations, and other endpoints. Smartphone integration is just a bonus. Companies that want to manage smartphones securely will thus find the process difficult without products like MobileIron or Good for Enterprise, which must be licensed, set up, and managed separately.
