
SUSE Linux Enterprise 11 SP3 tested
The Chameleon's New Clothes
Corporations need long-term stability from the software they use. When they purchase a subscription for an enterprise distribution, corporations are actually buying a promise that the provider will support, maintain, and carefully develop the distribution for as long as possible. Such stability saves the stressed admin from unpleasant tasks like replacing a kernel or some other essential system component.
An enterprise distribution implies that major renovations are needed as infrequently as possible, but without denying the distribution essential new technologies. These usually find their way into the distribution via patches and kernel backports. SUSE and Red Hat offer customers a seven-year and, optionally, a 10-year product life cycle. During this time, both companies keep essential system components such as the kernel, glibc, important system libraries, and development tools as constant as possible. Nevertheless, they regularly provide customers with the latest security patches. This approach also explains the Service Pack or Service Patch designation in the SUSE product name.
SUSE Manager
Companies that use a large number of enterprise distributions must distribute them to and maintain them on a large number of servers. This setup takes a powerful management tool. In contrast to Red Hat – with its Red Hat Customer Portal (RHCP) – SUSE does not offer a cross-site system management via a hosted service but instead offers a virtual appliance that needs to be installed locally: the SUSE Manager [1]. In terms of management, SUSE Manager delivers something similar to the Red Hat tool, but it costs extra. If you register a licensed SUSE Linux Enterprise (SLE) system with SUSE Manager, you have access to extensive management features, including monitoring and a scheduler for scheduling automatic updates.
Live Updates
Even without SUSE Manager, you are required to register with the Novell Customer Center to install SLE. Customers can use the center to request product updates and support and to manage their subscriptions (Figure 1).
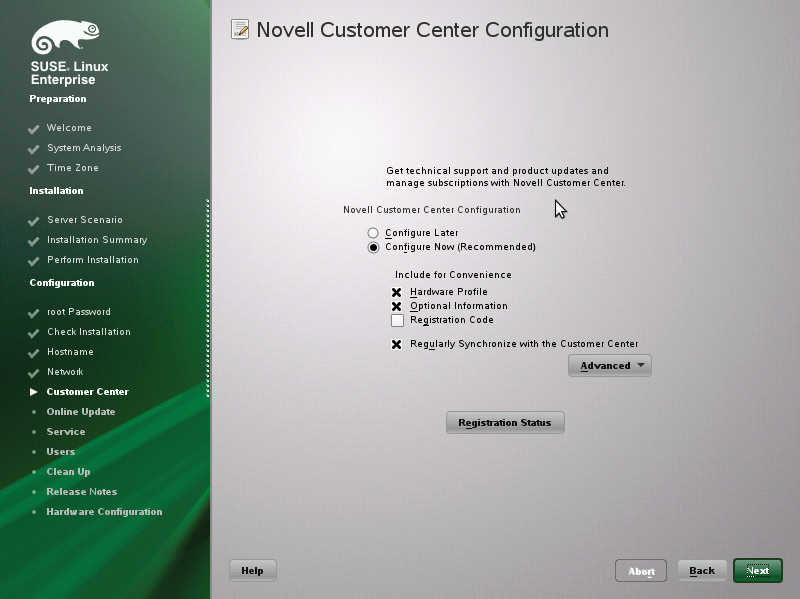
You need registration data to configure the Customer Center. Although you can skip registration during installation, this means you cannot access live updates. Users of the trial version can enter a valid email address, the computer name, or an arbitrary description when they register instead of an activation code. An initial online update can be launched directly from the installation.
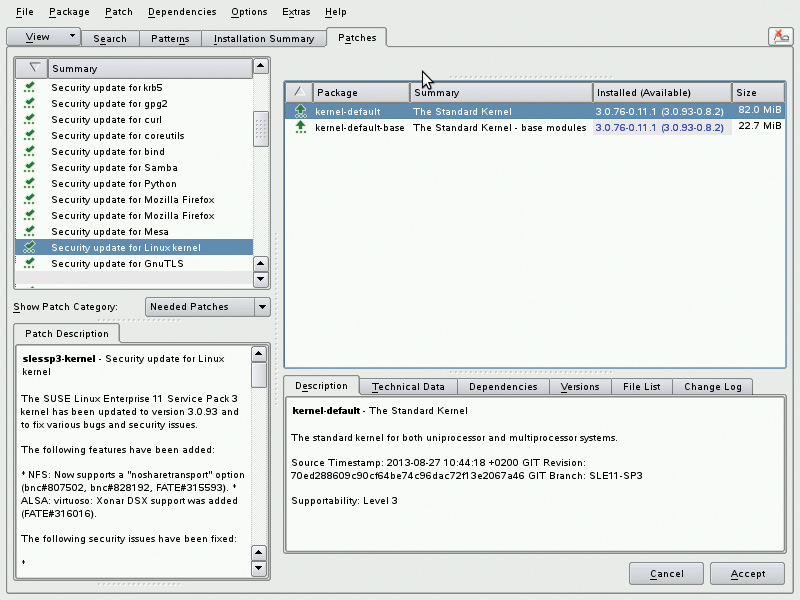
When updating, you will want to import all the patches from the Needed Patches category. This includes an update of the SLE kernel to version 3.0.82. You will also find a patch for the Firefox ESR version with extended support from 17.04 to 17.07. The patch may not fix the vulnerability in Firefox ESR 17.06, which became known while I was writing this article, because it only seems to affect the Windows version. However, it does demonstrate the timely response of the SLE maintainers (Figure 2).
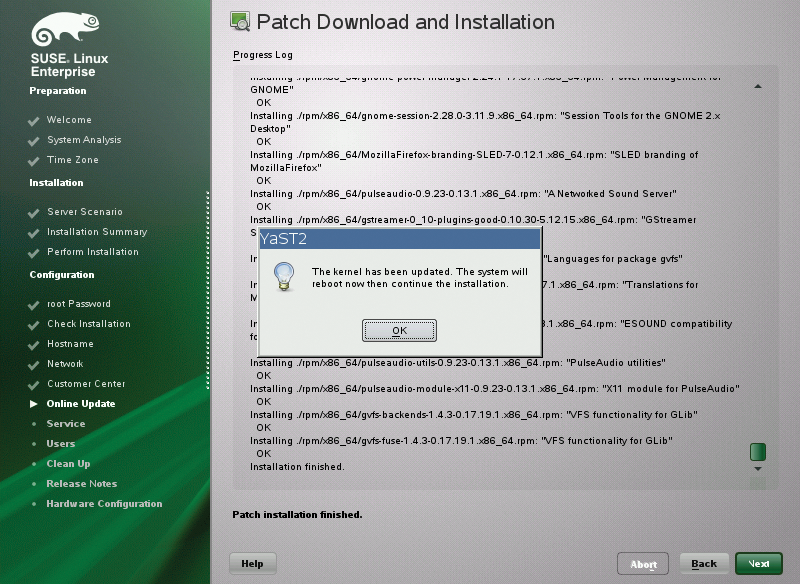
Because SUSE usually offers patches for SLE in the form of delta RPMs, an online update is fairly quickly done, ideally without rebooting – unless you have updated the kernel (Figure 3).
About Kernels
The main difference between the current SUSE and Red Hat enterprise distributions is the kernel maintenance strategy. From the customer's point of view, it is desirable to avoid changing the major kernel version if possible. To this end, Red Hat maintains a hardened RHEL 2.6.32 kernel in version 6, providing the latest development results in the form of backports. A similar strategy was pursued by SUSE until version SP1, which had the 2.6.32 kernel at the time. SUSE switched to a 3.0 SLE kernel for SP2, which caused the company a few problems. For example, some of the drivers built for SP1 no longer worked with SP2, and SUSE needed to make some adjustments to fix this problem.
In SP3, SUSE returned to its conservative kernel strategy. The distribution keeps the series 3 kernel, version 3.0.76, and integrates any necessary updates, such as current hardware drivers, via backports. They add a number of improvements to memory management and increased I/O throughput for CPU-intensive tasks to SLE SP3. Following the update of the kernel code for KVM and Xen, the current SLE kernel 3.0.82 also influenced the supported virtualization capabilities of SLE 11 SP3.
Virtualization
SP3 supports KVM virtualization with up to 2TB of RAM and 160 CPU cores per guest, thus catching up with RHEL 6.4. Moreover, it can use the Nested Paging function supported by the latest Intel processors to start a VM from within a VM. However, the function still has a status of Technology Preview and is not officially supported in any way by SUSE. Incidentally, the Xen kernel code was updated to version 4.2. In the context of other updates, SUSE also includes virt-manager version 0.9.4 and version 1.2.1 of the virt-utils.
Red Hat's virt-manager can be launched directly in SLE as a YaST module (Figure 4). In the Server Base Scenario dialog, the SLE installer asks whether you want to set up SLE as a virtualization host (hypervisor) for Xen or KVM as a normal system on physical hardware or as a Xen/KVM guest system on paravirtualized hardware. Full virtualization without paravirtualized or virtio drivers (KVM), however, is identical to installation on physical hardware. The full virtualization option is not available if you run the setup program on a virtual machine, or if the installer has found no CPU virtualization features (Figure 5).
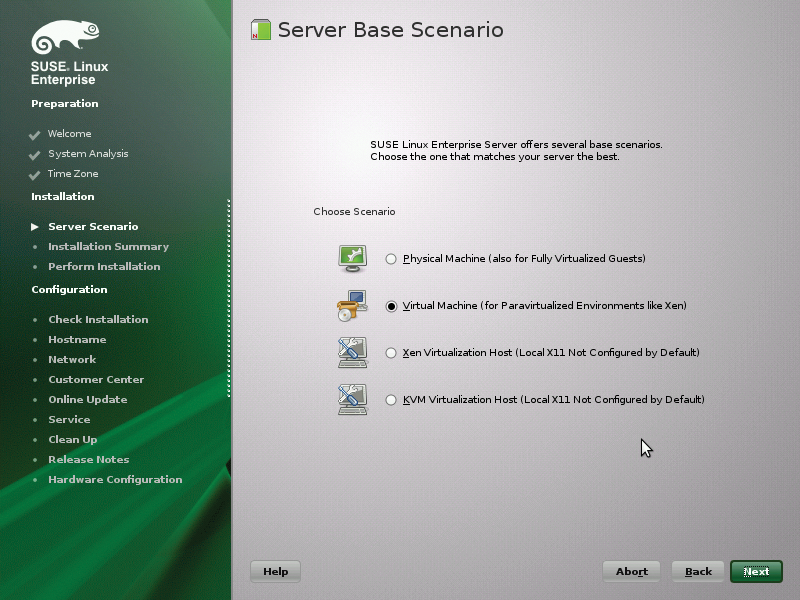
By the way, SUSE stopped providing the Xen hypervisor in the 32-bit SLE variant in SP2; 32-bit SLE can thus only be used as a Xen guest system. Xen paravirtualized drivers are available after installing the xen-kmp-default or xen-kmp-pae packages. In the scope of the SLE SP3 release, the SUSE developers have also updated their separately downloadable driver pack for SLE guest systems [2] to version 2.1. This includes the virtio drivers (disk, network, and memory/ballooning) for all Microsoft operating systems from XP on – in the event that one of the Microsoft operating systems is used as a guest system on a KVM-powered SLE 11 hypervisor.
Support for Windows Server 2012 and Windows 8 [3] is new. For enhanced Hyper-V support for installing SLE as a guest under Microsoft's hypervisor, you need to install version 5.0.7 of the hyper-v package. Using a ballooning driver, Windows automatically adjusts the memory size available to an SLE guest. Beyond this, a framebuffer graphics driver supports resolutions up to 1920x1080 pixels running on Windows Server 2012/Hyper-V. Also, the Windows host and guest SLE automatically negotiate the best communication protocol for efficient operation. KVM support in the SLE version for IBM's System z (s390x) and the desktop variant, SLED, are still classified as Technical Preview.
New Drivers
SLE SP3 supports a number of new hardware components, including the Xeon E5 processor family, Intel Core CPUs, and fourth-generation AMD Opteron series 4000 and 6000 processors. The same goes for Intel's second generation Atom MicroServer and numerous newer network cards. Also new is support for the Transparent Inter-Process Communication Protocol (TIPC) and Micron P320 PCIe SSDs. SUSE also has updated the kernel code for generating an iSCSI or FCoE-addressable iSCSI target to the linux-iscsi.org version in the Linux 3.4 kernel.
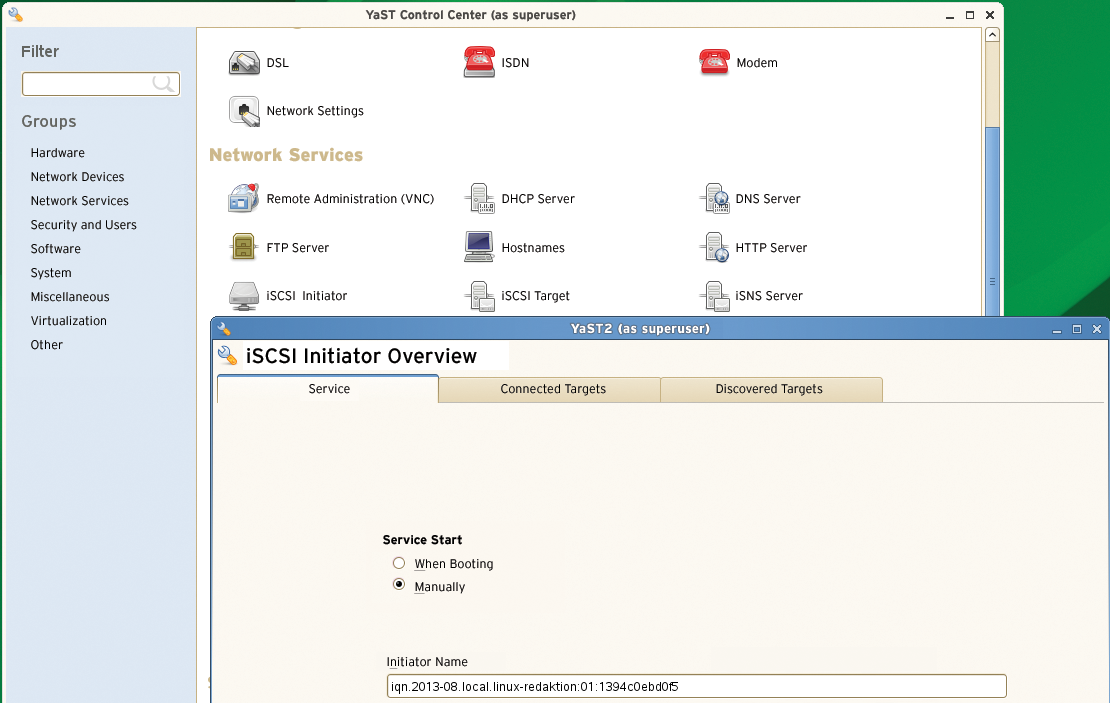
SLE traditionally includes graphical tools for configuring client access to an iSCSI device or an iSCSI server. The tools go by the names of iSCSI Initiator and iSCSI Target. The initiator is used to set the initiator IQN in the local /etc/iscsi/initiatorname.icsi configuration file of the similarly named service; iSCSI Target initializes the target configuration (Figure 6).
SUSE also has prepared its SLE kernel for the use of Intel AMT remote maintenance technology [4] (Active Management Technology). If you want to use AMT you need to install the associated Intel tools [5].
Filesystems
SUSE Enterprise Linux continues to use ext3 as the default filesystem. SUSE also supports the use of ReiserFS 3.6, XFS, and Btrfs, but not ext4. SLE 11 can by default only read ext4 filesystems. The admin must manually upgrade to and enable write support [6], if needed. In terms of Btrfs support, the SUSE developers have adapted the filesystem code so that Btrfs also supports quotas for subvolumes on SLE 11. In combination with the High Availability Extension, SP3 also supports OCFS2. The Snapper Snapshot tool first introduced with SP2 now works faster. It now also works with the LVM thin provisioning function.
Officially, the Device Mapper has only supported thin provisioning since kernel version 3.2. It provides a number of functions that were an integral part of LVM in previous kernel versions. These include the ability to generate and manage block-oriented devices, snapshots, and various RAID functions that can be used by other block-oriented devices (like hard disks). Thin provisioning is generally understood as a method of providing storage in virtualized environments (storage virtualization). The counterpart is hardware provisioning, in which the administrator performs the partitioning and formatting of disks manually and unchangeably. Another new feature in SLE 11 SP3 is that users can manage snapshots without root privileges. This task is even possible using a YaST module after installing the yast2-snapper package.
Software Updates
Of course, SLE 11 SP3 also comes with a large number of software updates. MySQL 5.5 is worthy of note; however, its database format is incompatible with that of MySQL 5.0. That said, SUSE provides a number of scripts [7] that allow admins to convert their MySQL 5.0 databases. Postfix also made a fairly large version jump from version 2.9.4 to 2.5.13. The new version behaves differently at various points [8]. As an alternative to the standard GCC compiler, SP3 also comes with GCC 4.7.2. This version provides extensive support of the standards ISO C 11 and ISO C++ 11. Furthermore, the service pack includes the OpenJDK 7 version [9] of the Java Runtime Environment and development kits, because OpenJDK 6 was abandoned by its developers.
UEFI Secure Boot
Other enhancements include support for UEFI secure boot at the same level as the current openSUSE version. Thus, SLE 11 SP3 now also launches on Windows 8 systems, which have secure boot enabled by default. The UEFI firmware classifies the SLE SP3 installation media for x86-64 systems as trustworthy, because SUSE provides them with a Microsoft-signed version of the Shim bootloader. However, the secure boot implementation of SLE (like others) entails a number of restrictions (e.g., software suspend and hibernation no longer work if secure boot is enabled). Additionally, users can only use a graphics driver with support for KMS (kernel-based mode setting) if secure boot is enabled.
The secure boot implementations in Ubuntu and Ubuntu Server do not involve these restrictions. On the other hand, they do not have a secure boot chain comprising a bootloader, kernel, and kernel modules; they only serve to facilitate installation on Windows 8 systems. SUSE has, however, developed its own machine owner key (MOK) process that lets users replace the SUSE signature used in an as-delivered state with their own key. Admins can thus load a self-compiled and unsigned kernel and kernel modules even though secure boot is enabled.
Conclusions
SUSE Linux Enterprise 11 SP3 is an important update, although it introduces only modest adjustments in line with the product philosophy. The new kernel backports in particular provide better hardware support and more virtualization features. Anyone using SUSE Linux Enterprise for the first time will need SP3, if only for UEFI support, and existing customers install SP3 anyway. (See "Trying Out SLE SP3" for more information.)
The responsibility for getting everything to work smoothly lies with the manufacturer, who covers this risk with the subscription fees. However, if you are used to state-of-the-art distributions in your daily work, some of the details may seem disconcerting from today's perspective, such as the lack of ext4 support, the preference for AppArmor instead of SELinux as the Mandatory Access Control Technology, and Upstart as the init system (instead of the usual systemd). Additionally, the default Gnome 2 desktop is not exactly fresh. This is probably the price you have to pay for a maximum 10 years of support.
