
New versions of the Endian and Sophos UTM solutions
Warhorses
Unified Threat Management (UTM) stands for complete protection. UTM systems filter incoming and outgoing network traffic, detect and prevent attacks, and block and quarantine viruses. If an appliance takes care of all these tasks, it needs to meet the customer's individual requirements precisely.
The UTM Firewall by Endian, a company founded in 2003, is one of the few open source firewalls available in both free and commercial versions. According to the manufacturer, more than 4,000 customers deploy Endian Firewall Enterprise, and more than 1.2 million users have downloaded the community edition. Both are based on the IPCop Linux distribution.
Although the free community variant is available for unrestricted free use in the enterprise, it lacks many of the features of the Enterprise Edition. Only the commercial version offers hardware appliances, virtual network drivers, professional support, a hotspot feature, and commercial-grade spam and content filtering. However, the community edition does provide the basic UTM functions, including antivirus, anti-spam, URL filtering, IPsec, and OpenVPN. It even protects larger networks easily. The ISO image of the community edition is available online [1]. If you want to test the Enterprise version, you can request a test key and the download link from the website [2].
Sophos UTM – first introduced in 2000 as Astaro Security Linux – has consistently focused on the needs of customers; it accordingly bills itself as "the market leader for Unified Threat Management in Europe." Although Sophos does not offer a community version, it does offer a home-use license for personal and noncommercial use. This license protects networks with up to 50 IP addresses and includes almost all features of the commercial version. The Sophos UTM Home Edition is available from the company's website [3].
For companies, Sophos also offers the Essential Firewall, a free version which, however, again only provides basic security functions. Except for the DNS proxy, it lacks all proxy-based features such as HTTP(S), SMTP, and POP3 and thus antivirus scanning, URL filtering, and application control. In terms of VPN protocols, however, IPsec and OpenVPN are missing; only L2TP over IPsec and the obsolete PPTP protocol are on board. At least, the former lets mobile devices such as smartphones connect via VPN. The installation medium for the Essential Firewall is available from Sophos [4].
Dosage Forms
Both Endian and Sophos offer their firewalls as hardware and software appliances. The latter both run on physical hardware and as virtual appliances. Sophos supports VMware, Xen, KVM, and Hyper-V.
Endian lacks official support for Microsoft's Hyper-V hypervisor. Although it can also be installed in a Hyper-V environment, it lacks drivers for the native Hyper-V network adapter, which limits the network bandwidth to a miserly 10Mbps. Additionally, full support for VMware and Xen is only available in the Enterprise version. Endian provides optimized images or virtual machines for the various hypervisors. Safety considerations for operating virtualized firewalls are discussed in the "Virtualized Firewalls?" box.
The hardware appliances have the advantage that manufacturers tune their equipment exactly to the requirements of the software. Sophos uses only Intel hardware, Endian also offers Endian Mini, an ARM SoC (System on Chip) variant. The use of appliances normally leads to a leaner kernel than with software appliances, which also potentially need to support exotic hardware. The hardware solutions do not envisage upgrading, for example, the memory or hard disk capacity; hence, a small appliance only effectively supports small networks.
Licensing for software and virtual appliances is by protected IP addresses and users (see the "Pricing Models" box). The reason is that the admin can expand the (virtual) hardware practically arbitrarily and thus significantly improve firewall performance.
Tabelle 1: Sophos Pricing
|
Model |
Price |
Maintenance |
Price (1 year) |
Total price (1 year) |
|---|---|---|---|---|
|
Mini |
US$ 995 |
Advanced |
US$ 385 |
US$ 1,380 |
|
Mercury 50 |
US$ 1,510 |
Advanced |
US$ 715 |
US$ 2,225 |
|
Mercury |
US$ 2,794 |
Advanced |
US$ 850 |
US$ 3,644 |
Tabelle 2: Endian Pricing
|
Model |
Price |
Subscription |
Price (1 year) |
Total price (1 year) |
|---|---|---|---|---|
|
UTM 110 |
– |
BasicGuard Bundle |
– |
US$ 695 |
|
UTM 110 |
US$ 595 |
Hardware Only |
– |
– |
|
UTM 220 |
US$ 1,275 |
Hardware Only |
– |
– |
|
UTM 220 |
– |
FullGuard Bundle |
– |
US$ 2,870 |
Endian 3.0
Endian released the new version of its firewall in January. The version jump from 2.5.2 to 3.0 already shows that this is a major release. With the latest version, the developers have visually modernized the user interface and extended it to include other languages. In addition to English, Italian, and German, it now supports Japanese, Spanish, Portuguese, Russian, Chinese, and Turkish.
Cleaning up the GUI has also had a positive effect, especially in the VPN configuration dialogs. The dialogs in the past were not very intuitive, and the system lacked its own certification authority (CA) for certificate management. Additionally, several new features have been introduced, including the previously missing HTTPS proxy.
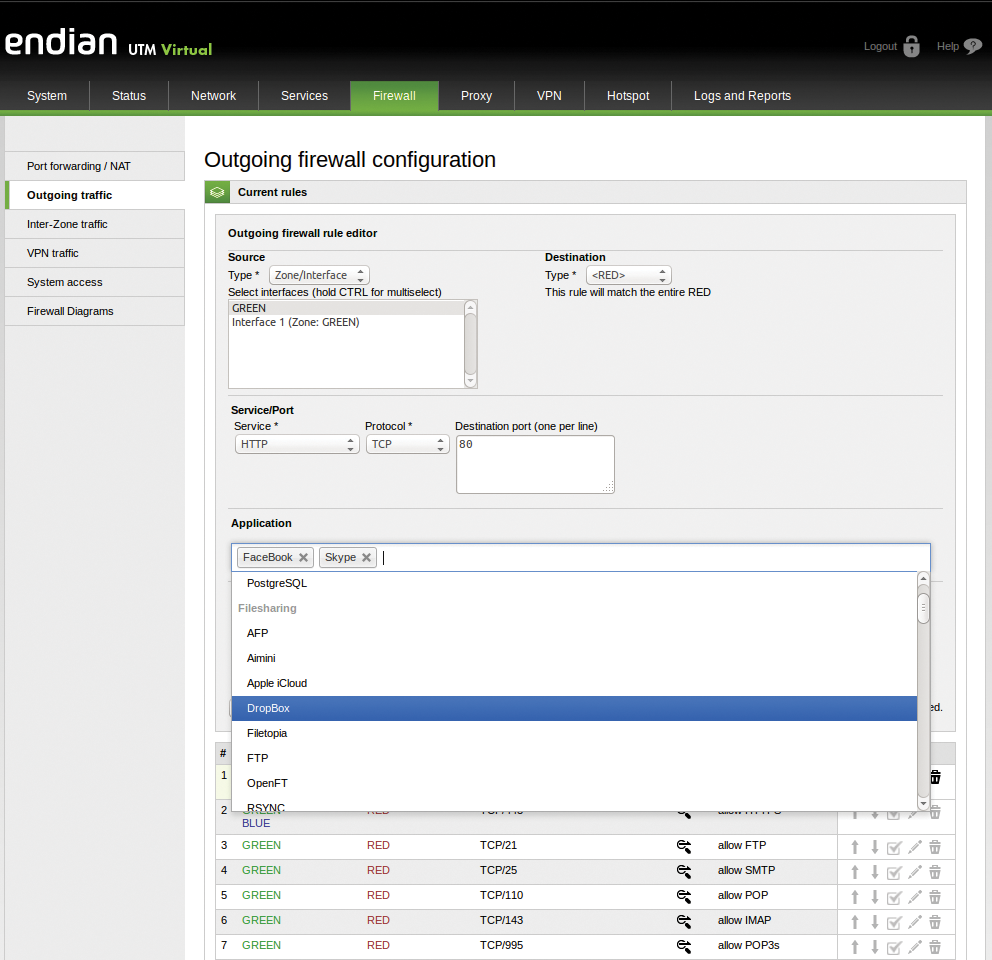
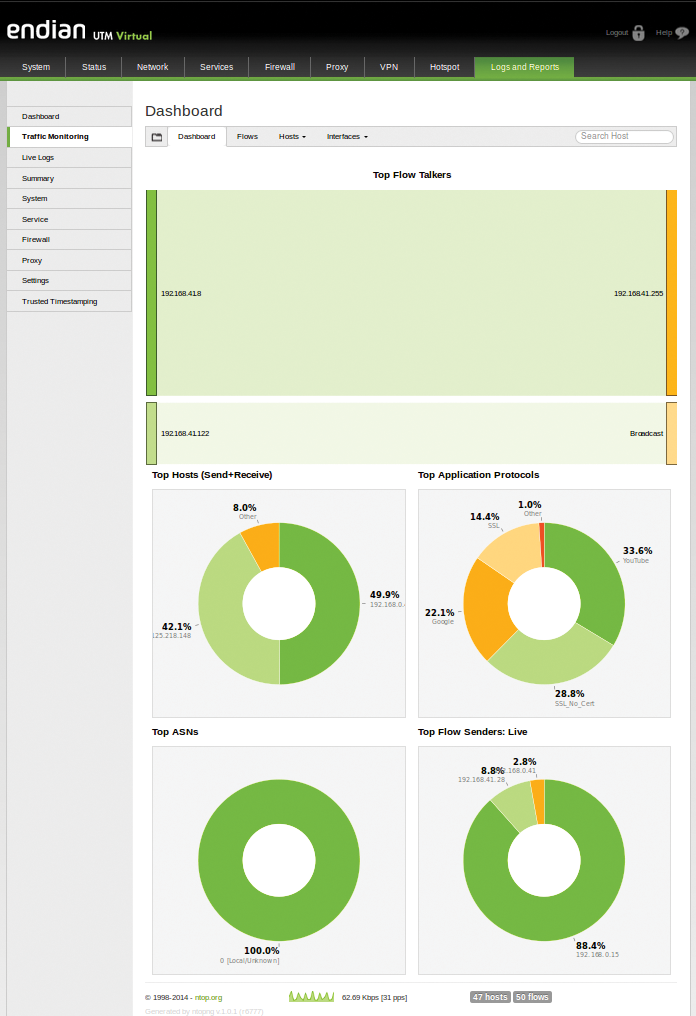
The outgoing firewall is now familiar with applications like Dropbox, Facebook, Twitter, and Skype and thus allows more finely tuned firewall rules (Figure 1). In version 3.0, the Endian Firewall also replaces the ntop tool for visualizing network traffic with its successor ntopng [8] (Figure 2). It also uses the new Application Control Module (ntop Deep Packet Inspection library).
Installing Endian Firewall
If you want to test the Enterprise Edition before buying, you will find an online demo on the Endian site. Alternatively, Endian provides test licenses for the commercial version but only with registration [2]. The activation code required for the installation and a download link for the ISO image are sent to you by email. Also, the community edition is available for free downloading.
Whether you use a physical system or a virtual machine for the test, you need a dual-core processor clocked at 2GHz, 1GB of RAM, and 20GB of free hard disk space. After completing the installation, you can initially access the web interface on the default IP address of http://192.168.0.15:10443. You need to use the passwords for the root user for shell access and admin for the web interface and register your account with the Endian Network for the Enterprise version. This cloud-based management center for Endian Enterprise installations lets you monitor the remaining maintenance period, as well as the hardware resources and your licenses – for example, for the commercial antivirus and URL filters.
The Endian Network also handles the installation of updates and the remote management of Endian Enterprise installations. Access for this purpose is via a reverse HTTPS or SSH tunnel. Additionally, the Endian Network provides a free OpenVPN client for Windows, Mac, and Linux as well as disaster recovery keys (USB images) for restoring Endian hardware appliances.
The Endian Firewall enables the most important services in the direction of the Internet following a default installation: HTTP(S), FTP, SMTP, POP3(S), IMAP(S), DNS, and ping. You can configure this under Firewall | Outgoing traffic. New firewall rules need to specify the source and target networks or the interface and the desired protocol.
Endian uses the same color coding as IPCop for the network interface (Figure 3). Green refers to the internal network (LAN), red to the external WAN interface, orange the DMZ, and blue the WiFi network. The new Endian version has an Application field that also lets you ban individual protocols or applications. For example, it prevents the use of Facebook and Skype:
Source: Interface Green/Blue Target: Interface Red Service: HTTP Application: Facebook, Skype Guideline: Reject
This rule must come first in the outgoing firewall configuration. It is followed by a rule that allows HTTP to the outside and with no restrictions for applications.
The integrated open source ClamAV antivirus scanner can be supplemented in the commercial version of Endian UTM by a license for the Panda antivirus scanner. IT works with HTTP, SMTP, FTP, and POP3 proxies; the configuration is found below Services | Antivirus Engine.
More Control Over the Use of HTTP(S)
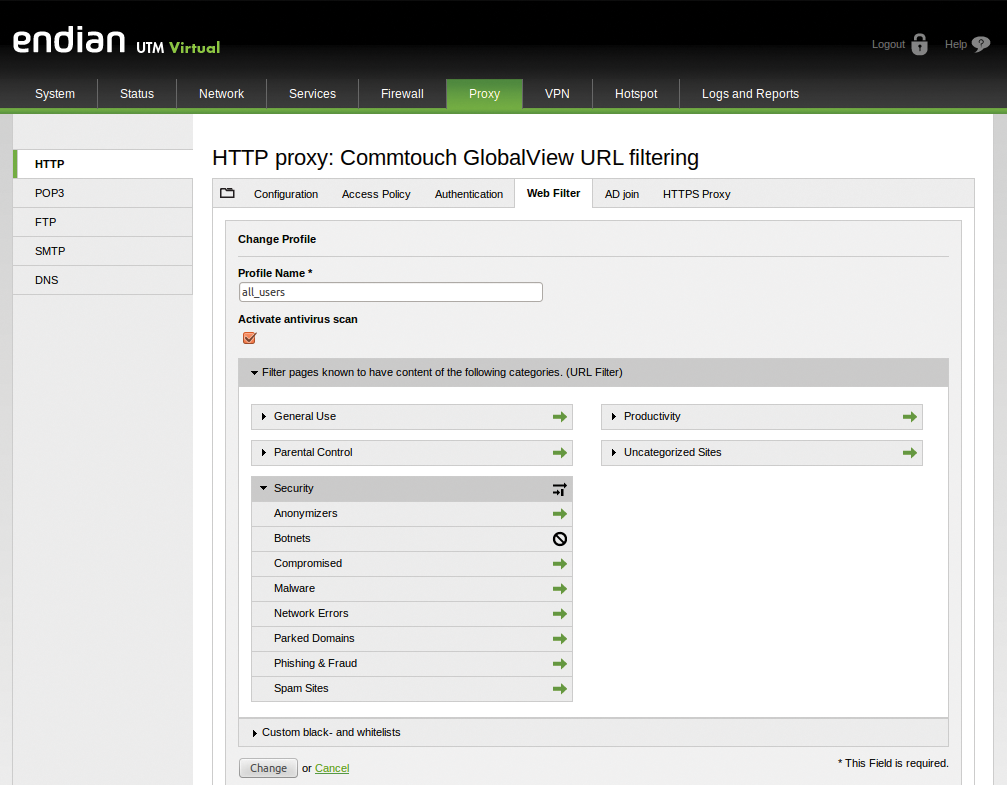
On the back end, Endian has revised the HTTP proxy with a solution based on Internet Content Adaptation Protocol (ICAP), thus improving performance. The HTTP proxy finally supports HTTPS connections so that the antivirus scanner now also checks encrypted traffic. An additional, commercial license extends the proxy with the Cyren URL filter (formerly Commtouch, Figure 4). In contrast to the standard web filters by DansGuardian, which the community edition also includes, the Cyren variant is familiar with more than 100 million websites organized in five main categories and 80 subcategories. Below Proxy | HTTP | Web filter, you can create profiles for different groups of users, for example, management, standard users, and trainees.
The SMTP proxy also has undergone changes. For example, the Endian Firewall now defines its own smart host with appropriate SMTP authentication data and outgoing IP address for each mail domain. In this way, email can be routed via different Internet mail servers depending on the domain used. Admins also can use a quarantine area below Services | Mail Quarantine to search for blocked messages and their content and to delete or forward as applicable. However, the tool lacks individual email quarantine areas for users.
VPN
If you look at the VPN configuration in the previous version of Endian Firewall, you'll see that a fair amount of catching up was needed. The interface of the new version has thus been revamped, and it comes with certificate management courtesy of its own CA, which generates X.509 certificates for the VPN modules. Alternatively, the CA can also generate a certificate signing request (CSR) for an external CA and thus also manage official certificates.
If you changed the IP address for the internal network interface of the firewall during the install – the default is 192.168.0.15 – you must first create a new root host certificate. Start by blocking the old root certificate in VPN | Certificates | Revoked Certificates and then generate a new one with Certificate Authority | Generate new root/host certificates.
The integrated OpenVPN server now also manages TUN interfaces, which is useful especially when you need to integrate smartphones and tablets. Endian has also updated the IPsec module to strongSwan 5.1 and – besides IKEv2 – includes integrated additional encryption algorithms such as Blowfish, Twofish, Serpent, SHA2, and AES-XCBC.
User management in the VPN module has also undergone a revamp: You can now also use the module to create external servers for authenticating VPN users in addition to local users. The module natively supports LDAP, Active Directory, and Novell eDirectory. Additionally, groups of users from directory services can be synchronized and local users organized into user groups (Figure 5). In this way, you can assign user groups popular VPN services or parameters, for example.
Hotspot
For a long time, Hotspot has been an established and frequently used feature of the Enterprise Firewall. The integrated captive portal sets up guest accounts, whereas the account generator lets the admin create user accounts manually. Alternatively, admins can use Endian SmartConnect, a self-service feature that automatically delivers access credentials to users by way of text message or email. The admin defines whether the tickets are free; if not, billing can be handled through PayPal or credit card.
In the new version, Endian Hotspot also integrates external authentication systems, including LDAP, Active Directory, Novell eDirectory, and RADIUS. It can also create time-limited tickets for Hotspot usage, for example, to allow users one hour of Internet access per day. Another new feature is Hotspot SmartLogin. If it is enabled, Hotspot reads the access credentials from a session cookie in the browser, so users do not need to continually re-enter their credentials.
Even the reporting section has had a facelift. The new dashboard now delivers a summary of the most important events, such as blocked viruses, incoming and outgoing email, attack attempts, and web traffic on a clear timeline. Live logs also helps you quickly compile the most important events in a convenient spreadsheet format. The additional filter function lets you home in on points of interest for troubleshooting, for example.
Conclusions: Endian 3.0
With the new release, the Endian developers have significantly shortened the gap to other UTM systems on the market – Endian Firewall Enterprise 3.0 is an impressive piece of work. However, much remains to be done. No uniform user database for VPN and web proxy use is available, and you will look for user-specific spam quarantine in vain. Endian also does not provide meaningful security enhancements such as a web application firewall (WAF) or email encryption, even in the new version of its firewall.
Sophos UTM 9.2
Sophos UTM (as the former Astaro Firewall has been called since the takeover by Sophos in the summer of 2011) is considered one of the most popular UTM systems. In Germany, this popularity is a result of the product targeting the market by means of local development resources. Also, customers and partners can use the feature request portal, introduced back in the Astaro era, to propose new features [9]. After registering, users receive 20 votes with which they can vote on feature requests. Proposals with the most supporters typically rapidly make their way onto the developers's roadmap, leading to a consistent focus on the needs of customers.
The newly released 9.2 version of Sophos UTM comes with several new features. In line with its update routine, Sophos has now completed the soft release phase, in which the new version is only available as a manual update. Automatic distribution by Up2Date was scheduled to start shortly before this issue went to press.
The various security functions of the Sophos UTM firewall are available either individually in the subscription model or en bloc as a full-guard license. Sophos now offers the following subscriptions:
- Network Protection: Firewall, intrusion prevention, VPN.
- Web Protection: URL filtering, application control (next-generation firewall), anti-virus, HTTP, and HTTPS proxy.
- Email Protection: Anti-spam, antivirus with SMTP and POP3 proxy.
- Web Protection: Web Application Firewall (WAF) for protection against attacks on web servers and applications.
- Wireless Protection: Use of the UTM system as a central WLAN controller for Sophos Access Points, including a captive portal.
- Endpoint Protection: Antivirus and device control for (Windows) clients on the network
Installing UTM 9.2
The Sophos UTM is available [10] as an ISO image and as an Up2Date Package for existing installations. The image can be installed either on a physical device with at least two network cards or on a virtual machine. Sophos supports Xen, KVM, and VMware, as well as Microsoft's Hyper-V hypervisor platform. To run version 9.2, the manufacturer recommends at least a 1.5GHz processor, 1GB of RAM, and 20GB of free hard disk space; a faster processor and more RAM will give you a noticeable performance boost.
Alternatively, you can test the new version in the Amazon cloud (AWS). Sophos provides Amazon Machine Images (AMIs) on Amazon Marketplace for the regions US East (Virginia), EU West (Ireland), and Asia-Pacific (Singapore).
Note that the installation routine completely overwrites the contents of the existing hard disk; parallel operation with existing operating systems is not intended. After installation using the default settings, the firewall's web interface is accessible on https://192.168.0.1:4444, where you specify the password and install licenses.
Highlights
In the form of Sophos Labs, the manufacturer maintains a worldwide big data analysis network that examines email, URLs, files, and IP addresses, in terms of reputation and potential malware, and identifies botnets and their control server (Command and Control sites) 24/7. The new version of Sophos UTM integrates Sophos Labs and detects data from botnets, even without extensive analysis of the data traffic. The dashboard has a new icon that alerts you if the firewall detects botnet traffic and outlaws the infected hosts into the bargain.
At the same time, performance of the Intrusion Prevention System (IPS) has improved noticeably. It now automatically adjusts the system settings to match the hardware appliance model, while also automatically disabling patterns that are no longer relevant for intrusion detection and prevention based on a pattern-aging system. Command-line enthusiasts will enjoy the new ipsctl tool, with which the IPS system can be easily managed in the shell.
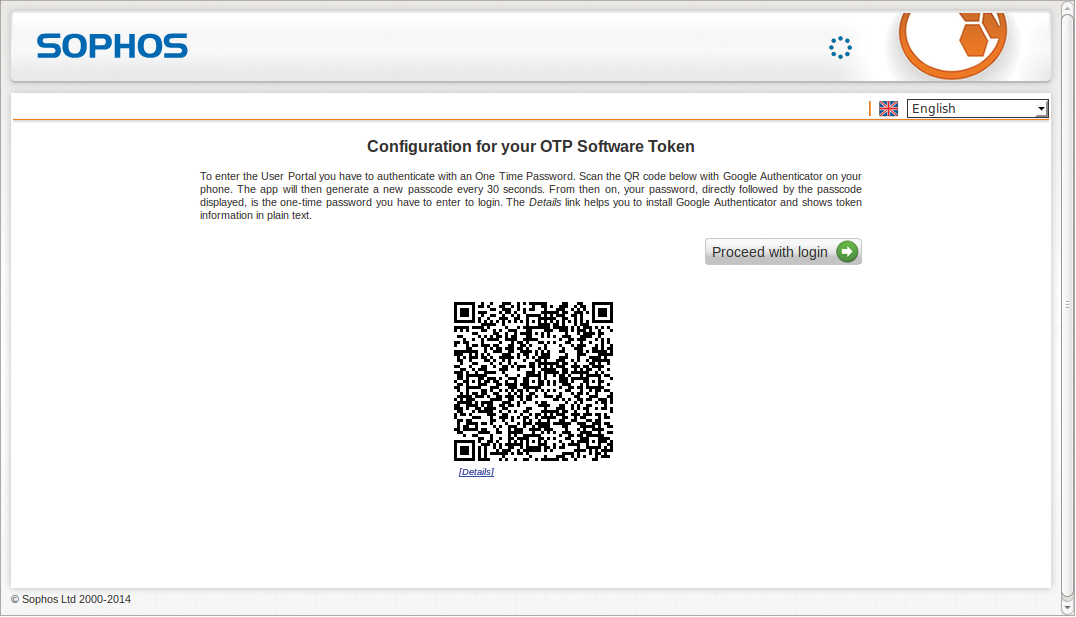
Another great achievement is new two-factor authentication with one-time password (OTP) tokens. It safeguards, for example, VPN connections and access to the User Portal or to the admin console with an additional one-time password, which is appended to the previously used static password. The Google Authenticator app is one potential one-time password generator (Figure 6), but you can also use hardware tokens and other applications that support the OATH/TOTP standard.
Integrated two-factor authentication, however, is used exclusively with the firewall's own services, but not with external applications such as Outlook Web Access.
The following steps illustrate an example using Google Authenticator:
1. If you have not already done so, enable the User Portal (Management | User Portal | Global | Enable User Portal). Under Approved networks add at least Internal (Network).
2. Enable the Definitions & Users | Authentication Services | One-Time Password function and uncheck the All users must use one-time passwords box.
3. Drag and drop all users you want to authenticate via OTP into Users & Groups to add them.
4. Enable Auto-create OTP tokens for users and check User Portal.
5. Install the Google Authenticator app following the instructions online [11].
6. Log on to the User Portal with the previously selected user and password on https://IP web interface. This displays a QR code for scanning by the Google Authenticator app.
7. In the Google Authenticator app, press the pencil icon, then click the plus sign at the very bottom and scan the QR code.
8. Sign in with the username and password and append the one-time code from the Google Authenticator to the password.
These steps enable two-factor authentication for a user of the user portal.
More Control for the Web
In version 9.2, Sophos has also fundamentally revamped the GUI of the Web Protection module. The Filtering Options submenu now combines several functions, such as the URL filter categories and the exception list. Another new addition is Policy Test, which allows admins to test the effect of a policy change in the context of a client (IP address), a user, and a defined period (Figure 7).
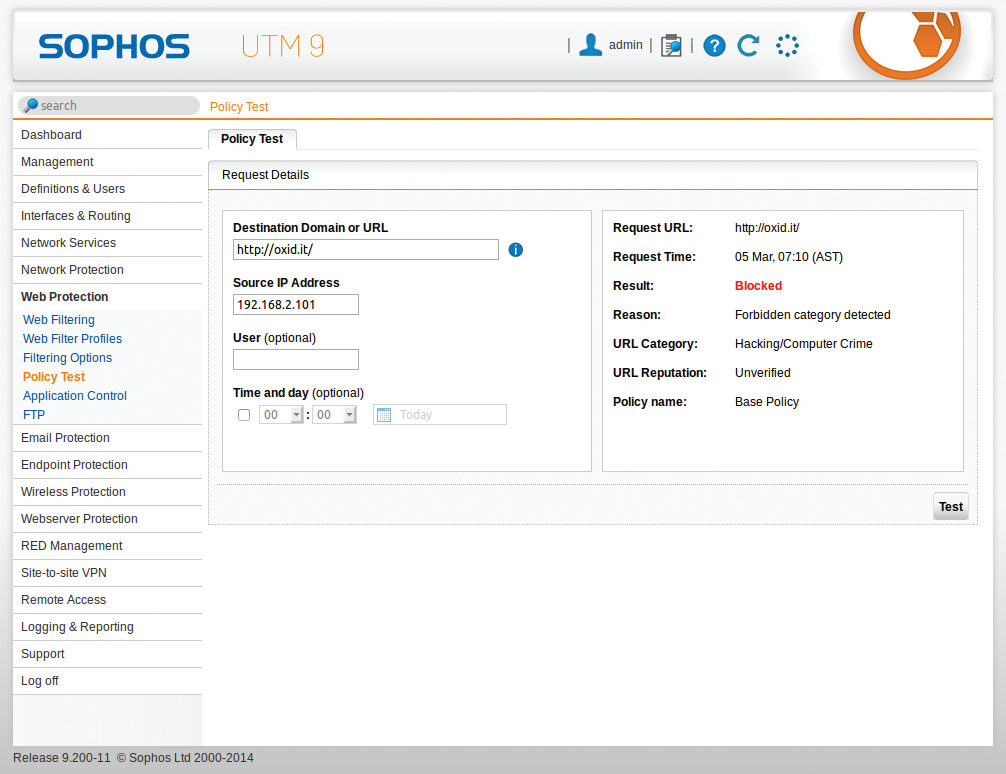
This feature lets you check, for example, whether a new rule allows a user access to a web address at a specific time of day. Additionally, the web filter in the Web Filtering | Policies | Additional Options section now also provides a Google Apps domain filter. It limits access to Google applications by domain and thus blocks, for example, access to Gmail and other services with private accounts.
If the Sophos Engine is selected as the virus scanner under Management | System Settings, the UTM automatically transfers suspicious files to Sophos, where they are executed in a sandbox and analyzed. Also, only the Sophos virus scanner can now also block PUA (Potentially Unwanted Applications). What Sophos means by this is programs that are not really harmful but are undesirable – at least in a business context (e.g., hacking tools, adware, and remote maintenance tools). Moreover, you can now manually classify the URL filtering websites in different categories. In this way, for example, sites from the uncategorized category can be assigned to existing filter categories.
Transparent HTTP and HTTPS proxies were already available in previous Sophos UTM versions. Now, these connections can authenticate against Active Directory using single sign-on (SSO). The prerequisite is that the clients can resolve the local network domain name (FQDN) of the firewall. This feature only works reliably for the browser; programs that establish an HTTPS connection to the Internet – for example, to retrieve automatic updates – are not correctly identified.
Furthermore, thanks to multidomain Active Directory user support, users who log in via SSO can now use the same usernames in different Windows domains; thus far, usernames had to be unique. Admins can also choose from multiple HTTP authentication methods for different types of devices in the new UTM version. In this way, for example, smartphones, tablets, Kindles, and other devices that do not support SSE can be networked using an alternative authentication method.
Protection of Confidential Information
Sophos has two more new features that can help enterprises fight against the disclosure of confidential information, whether intentional or accidental. The Data Leakage Prevention (DLP) function investigates outgoing email messages and their attachments for data that should not leave the enterprise at all or that should be encrypted before doing so.
Depending on the industry and the country, this type of information includes credit card numbers, phone numbers, and other personal information that Sophos provides in a series of Content Control Lists, which you can enable to suit your individual needs. Custom strings complement the supplied lists, whereas the DLP feature also supports regular expressions. Thus, you can analyze outgoing email traffic for company-specific data and specific keywords, for example. If the Sophos UTM finds a matching email, it stops the delivery and notifies the sender, the administrator, or a third party.
Another option in the DLP settings supports automatic encryption of confidential data before sending email using the new SPX Encryption feature. SPX stands for Secure PDF Exchange, a symmetric encryption method for outgoing email. The recipient does not need an encryption program, just a PDF reader.
Sophos UTMs have supported gateway-to-gateway-based email encryption on the basis of OpenPGP and S/MIME for years, but this functionality does not help in the context of data leakage prevention. SPX closes the gap and only allows messages with content identified by the DLP module to be sent if encrypted. It bundles the contents of the email into a PDF file that the recipient can only open if they have the matching password (Figures 8 and 9).
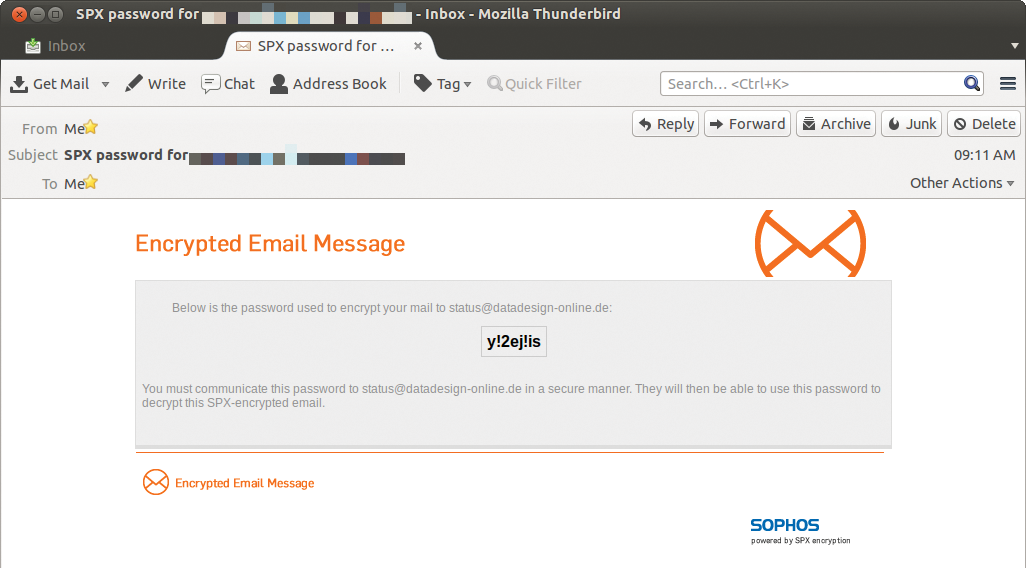
The password policies are configured up front by the administrator in Email Protection | SPX Encryption. In addition to password complexity, SPX templates also define whether the firewall generates a new password for each outgoing email or whether each recipient receives a static password that remains the same for all their email. With both methods, the sender of the message receives the password by email and then communicates it to the recipient in a secure way. If the sender wants to define a password, she must add it to the subject line of the message:
[secure:password]Subject
The UTM replaces the actual content of the email with PDF reader instructions for the receiver; these instructions can be customized in detail in terms of content and appearance.
The beta version, to which ADMIN magazine had access for this article, still had a bug that I hope will disappear in the final version: The brackets used in the schematic also needed to be specified for defining the password and automatically became part of the password, thereby forcing the recipient to enter them in order to open the encrypted message.
You can use SPX encryption without the DLP function, if so desired. Users then decide for themselves which messages they SPX-encrypt before sending. To this end, they add an additional header field to an outgoing email:
"X-Sophos-SPX-Encrypt: yes"
Sophos provides Outlook users with a plugin for this purpose. Thunderbird users need to add the header field manually in the configuration dialog Preferences | Advanced | General | Config Editor (about:config) until Sophos provides the announced plugin for this mail client.
If you enable the SPX reply portal, the receiver can also respond with SPX-encrypted, secure email. For this purpose, the PDF includes a Reply button that calls the URL of the portal response in the browser. This process also works with devices like the iPad. The SPX reply portal then provides the unencrypted reply to the original sender.
Web Application Firewall
The Web Application Firewall (WAF) in the Sophos UTM Firewall provides an Apache web server-based reverse proxy to protect its own web server against SQL injections, cross-site scripting attacks, and other web-based attacks. Furthermore, it scans connections to the web servers in both directions for viruses and blocks clients with a bad reputation. In version 9.2, WAF also gets a new engine and a new pattern recognition feature, which Sophos promises to update continuously via Up2Date.
The new version of Sophos additionally extends the maximum file size for uploads from 128MB to 1GB. Also new is a function for reverse authentication. The Web Application Firewall then handles authentication for web applications, to protect the latter. After successful authentication in basic or form mode, the firewall then passes on the results to the configured back-end servers. This function is clearly targeted at customers of the now-defunct Microsoft TMG (Threat Management Gateway) product, which offered similar functionality.
Conclusions: Sophos UTM 9.2
The new version of Sophos sets standards in the UTM landscape in terms of functionality and usability. New features, such as two-factor authentication and SPX encryption, have been at the top of customer and partner wishlists for some time. Botnet detection, advanced threat protection, and the new DLP functions help Sophos make life a little easier for security admins. These requirements are part of everyday life in medium-sized companies and can be quickly and easily implemented with version 9.2. It's a pity, however, that the DLP functions so far only protect email messages against accidental and deliberate information leakage. A function that also searches outgoing HTTP(S) connections for sensitive data and blocks messages where appropriate is still missing.
Something for Everyone
The new versions of the Endian and Sophos UTM firewalls provide much that is new. With the HTTPS proxy, the revised VPN GUI, application identification, and the new ntopng live network monitoring, Endian catches up to other providers. Sophos is again innovative in this price range with two-factor authentication, SPX email encryption, botnet detection, and optimized WAF.
Whether you prefer the feature-rich Sophos UTM or the leaner Endian firewall depends not only on your own individual security requirements, but also on the type of deployment – physical or virtual. Endian offers support for VMware, Xen and KVM; Sophos additionally supports Microsoft's hypervisor Hyper-V.
