
Multifactor authentication from FIDO
Watchdog
The recent discovery of a 1 billion+ password treasure trove in the hands of Russian cybercriminals brings home a far too common occurrence. Almost daily, you hear of a new breach and a new set of stolen credentials, a new pastebin dump, and millions of frustrated admins and end users. Beyond security breaches, other reasons to replace this nearly 50-year-old technology include:
- Users reuse passwords
- Users create weak passwords
- Users want ease of use
- Passwords are centralized in databases
In short, passwords are painfully antiquated, insecure, and clearly in need of an overhaul.
Real Risks/Real Costs
The costs of single-factor authentication are hardly theoretical and without significance. These are just a few real-world facts about password risks and costs:
- Forrester Research notes the cost of password breaches reached more than US$ 200 billion in annual losses.
- According to the Verizon 2013 Data Breach Report, weak or stolen credentials account for 76 percent of network intrusions, and more than 50 percent use some form of hacking.
- A 2013 SplashData study on data from an Adobe breach showed the top five most used passwords are: 123456, password, 12345678, qwerty, abc123. (Yes, you make take a moment to scream or hurl a heavy object!)
- According to Intercede, 51 percent of users share usernames and passwords with friends, family, and colleagues.
Unfortunately, many large players in the marketplace would rather keep their heads in the sand than face reality.
What is MFA?
It's time to face the facts that this more than 50-year-old love affair with the password should end. Admins need to look for what is next. That next step can and should address some of the key weaknesses of single-factor authentication. Multifactor authentication is that vital step forward, offering improved security, greater simplicity, and more cost efficacy, among other things. Before I continue, I'll define multifactor authentication in greater detail.
Multifactor authentication, which is also known as MFA, two-factor authentication, two-step verification, TFA, T-FA, or 2FA, is an authentication approach that requires two or more core factors. It requires something you know (your password), something you have (physical authentication token or virtual MFA on a smartphone), and in the case of biometrics, a third physical factor such as a fingerprint, retinal pattern, and so on. For those looking for a better solution, the good news is that it's getting closer with the help of technology and open standards.
Enter the FIDO Alliance
From the mess of the failed, tired password comes a new promising development. The FIDO (Fast IDentity Online) Alliance is an industry consortium non-profit organization working on what's next for authentication while making web authentication easier, less expensive, and more secure. The FIDO Alliance describes its mission [1] as:
- Developing technical specifications that define an open, scalable, interoperable set of mechanisms that reduce the reliance on passwords to authenticate users.
- Operating industry programs to help ensure successful worldwide adoption of the specifications.
- Submitting mature technical specification(s) to recognized standards development organization(s) for formal standardization.
The standards body consists of industry titans such as ARM, Bank of America, BlackBerry, Google, Lenovo, MasterCard, Microsoft, PayPal, RSA, Samsung, Salesforce, Visa, and Yubico, among others. With more than 100 members, the group has a lot of momentum behind its efforts.
Open and Interoperable
Imagine, if you will, that the early Internet had been built on closed-source proprietary technologies that didn't interoperate. In nearly every case those closed non-standardized technologies would have failed and only gained meager adoption. Why? It's simple – open standards and technologies have economic benefits. The Internet is very much predicated on open technologies and standards. Anyone with an elemental understanding of the underpinnings of the Internet must acknowledge that the vast majority of it wouldn't exist without open standards and open source.
Brett McDowell, Executive Director of the FIDO Alliance, stated it succinctly in a recent interview: "There is simply no other plausible way to solve an Internet-scale problem other than open standards. It is entirely untenable to presume all the world's devices and Internet services are going to adopt a single authentication product from a single company."
He added: "Since FIDO itself doesn't define how to perform the device-side user identification, but rather performs the function to securely connect those devices to any Internet service or web site that can 'speak' the protocol, FIDO standards actually drive market demand for innovations and competition for the best products and methods in that arena, e.g. fingerprint or voice recognition, motion, gestures, etc."
FIDO is a natural expansion of this powerfully successful open model that will open up innovation in this much needed space. It changes the economics of authentication and focuses on interoperability and openness. FIDO also means real-world deployment and testing, which can only mean gradual improvement of this open technology standard.
Many Technologies/Many Options
The many players in the alliance are opening up multifactor authentication to innumerable options. Using technology ranging from biometrics (fingerprint, iris, voice, and facial recognition), tokens, Trusted Platform Modules (TPMs), embedded security elements (eSEs), smartcards, Bluetooth low energy (BLE), or even your smartphone, you can now deploy two-factor authentication.
This full range of authentication technologies across multiple services and devices means an interoperable infrastructure that can apply the multifactor technology of today and tomorrow. FIDO can use existing industry standards such as OpenID and SAML. The FIDO Alliance offers opportunities for improving the security of end consumers and enterprise IT as well. Next, I'll explore the basic FIDO protocols U2F and UAF.
U2F vs. UAF
The FIDO protocols U2F and UAF offer a variety of use cases and configurations. Based in public key cryptography, these protocols take the cost and complexity out of traditional public key infrastructure deployment. These two protocols offer very different user experiences.
The UAF (Universal Authentication Framework) protocol is the passwordless experience, whereby the user registers a FIDO Ready device to an online service. This can be a fingerprint, facial recognition, voice, PIN, and so on. The passwordless UX (User Experience) is explained in Figure 1.
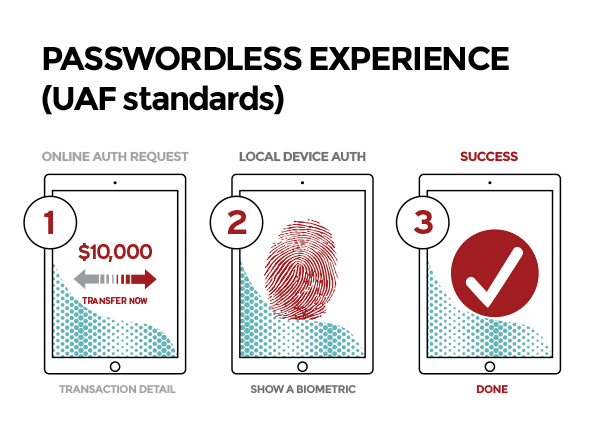
UAF allows online providers to configure the user experience they choose. This means any service provider can configure it to use the local biometric alone or biometric plus PIN combination. After a device is registered, a user can authenticate simply by using the registered authentication mechanism without any further complexity, which is quite a bit better than single-factor passwords.
The U2F (Universal Second Factor) protocol delivers strong multifactor authentication to online services. These services can still offer a user name and password but augment it with another factor, such as a USB or near-field communication (NFC)-capable USB device. Users simply register the second factor for the online service. When authenticating, they present this registered device by plugging in the USB device, NFC tap, or other FIDO Ready hardware. U2F is explained in Figure 2.
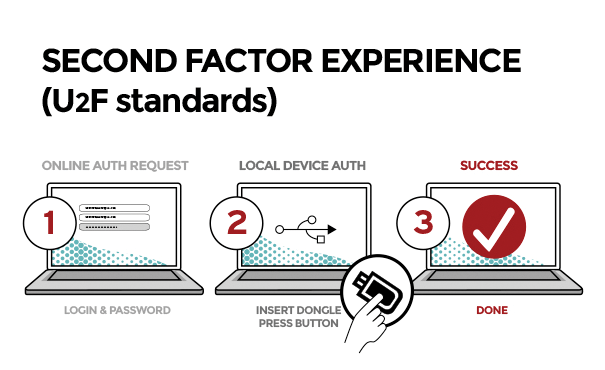
Browsers will build in support for the use of a variety of U2F options, enabling the protocol with a myriad of FIDO Ready MFA devices.
Public Key Cryptography
Standard public key cryptography is the basis of the FIDO protocols. When registering to a new service, the user creates a new key pair. This stronger authentication maintains the private key securely on the FIDO Ready device and registers the public key with the chosen online service. Only the user in possession of the FIDO Ready device itself can securely authenticate with it. This can be done in many ways, such as fingerprint, voice, PIN, or pressing a button, among other ways.
FIDO and Privacy
Mention the word biometrics or centralized authentication mechanism and many in the privacy community will show a furrowed brow. Note, however, that FIDO doesn't require the use of biometrics but supports a variety of technologies. These technologies are often assumed to be diametrically opposed to privacy. Not so with the FIDO Alliance. It is important to note that the FIDO protocol comes with privacy baked right in. FIDO protocols don't provide information that can be used to corroborate, uniquely identify, or track a user across multiple services.
With FIDO protocols, biometric information never leaves the device. As with any other standard or industry effort, the involvement of technologists can help drive its future direction. If privacy matters to you, as it does to me, you can work to ensure these standards maintain it.
Certification
In late 2013, the FIDO alliance began a certification program, FIDO Ready [2], for passing its standards testing. At the 2014 CES (Consumer Electronics Show), early implementation by vendors AGNITiO [3], FingerQ [4], Go-Trust [5], Nok Nok Labs [6], and Yubico [7] were highlighted. Note that this technology, various vendor offerings, and the core protocol are still evolving, and deployment isn't seen in as many live implementations today as will be seen in the future. My focus here will be on two current early implementations by Yubico and Nok Nok Labs. With the backing of these large vendors and open standards, the sky is the limit for this future of MFA authentication.
Yubico U2F Yubikey NEO
Yubico provides strong hardware-based multifactor authentication that is easy, affordable, and FIDO compliant. Driverless multiplatform USB and NFC devices give it a wide multiplatform and capable reach. Yubico makes a commitment to open source/open standards, which is helping spur the extension of their technology beyond the already long list of supported vendors and partners.
As of today, the Yubico U2F Yubikey NEO [8] is the main FIDO Ready product. It is not in public deployment but is scheduled to be released to the general public in late 2014. The CEO and Founder of Yubico, Stina Ehrensvard, agreed to answer some of my questions regarding Yubico's U2F-focused products. In describing the Yubico Yubikey NEO, she stated: "FIDO U2F is different: It is easy to use. Just a simple PIN and touch. Or for users who prefer biometrics instead of entering a PIN/password, they can swipe their finger on their device."
Furthermore, the Yubikey has attracted some interest from large players such as Google and others. Ehrensvard stated: "As of today Google has implemented YubiKey NEO with FIDO U2F across their enterprise. Several enterprises and online services are in the same process, but these are not yet official." Yubico expects more than 200,000 YubiKey NEOs will be deployed within Google and elsewhere for U2F authentication. This is quite promising for an evolving standard.
When I asked Ehrensvard why she thinks FIDO U2F will succeed where other standards and technologies have not, she said: "It is designed to be truly open and encourage innovation. Google and Yubico has already published U2F open source reference code, initially available for all FIDO members, and by end of the year it will be available for any organization who wants to build their own server back end and develop their own FIDO devices. FIDO U2F is designed to be a truly open standard, encouraging multiple authentication methods and chip/device/token/software vendors to innovate and compete."
With the massive backing of many very large providers and partners, you can rest assured that Yubico's FIDO Ready solutions will be a leader in multifactor solutions of the future.
Nok Nok Labs
Nok Nok Labs offers another stellar solution from one of the founding members of the FIDO alliance and inventor of the FIDO UAF protocol. Instead of authentication silos, Nok Nok developers envision a world embracing myriad technologies and the FIDO protocol for simple, secure, ubiquitous authentication. This includes biometric, non-biometric, hard token, and software – all providing easy secure authentication.
In an interview with Brendon Wilson, Director of Product Management at Nok Nok, he describes their efforts as not just another authentication vendor offering a point solution. Instead, the company aims to change the underlying framework on which current authentication solutions depend. The Unified Authentication Infrastructure leverages the Universal Authentication Protocol to provide a scalable, strong authentication protocol designed for modern computing requirements and the "Internet of Things."
Today, Nok Nok Labs' S3 Authentication Suite [9] powers fingerprint authentication for PayPal on several Samsung devices. Nok Nok also enables FIDO Ready authentication on many Lenovo laptops. In an email interview, McDowell of FIDO Alliance detailed this promising deployment: "The first deployment of FIDO Ready authentication was announced by Samsung and PayPal, utilizing implementations of FIDO specifications by Nok Nok Labs and the Synaptics fingerprint sensors embedded in the Samsung Galaxy S5. The same FIDO Ready payments technology is now shipping in the newer Samsung Galaxy S5 mini and the Samsung Galaxy Tab S devices."
With backing from these major players, the solutions from Nok Nok based upon FIDO standards look to be a major part of the future replacement of the hackneyed old password.
FIDO and the Future
McDowell put it best when he said of the future of the alliance: "As the famous adage goes, 'prediction is hard, especially when it is about the future.' But I'm a firm believer that FIDO protocols are in an almost unique position in the history of Internet technology with a solution that has been well vetted and prepared to meet the opportunity to serve this unprecedented pent-up demand for an open standard approach to addressing the password-centric vulnerabilities plaguing our ecosystem at an increasingly alarming rate." I hope he's right; the tired single-factor password needs to retire as soon as possible.
The momentum behind FIDO is strong. Its many players are trying to solve the age-old woes of single-factor authentication. Keep watching as this standards body continues to develop and refine its specification to be the unifying force in authentication. An extensive range of authentication technologies are all embracing this new promising opportunity. Device-independent, simple, and secure authentication is definitely something to look forward to.
