Email sender verification with DMARC
Traffic Control
Faking email senders is easy. Because email was not originally intended as a global communication tool, the system offers no convenient means for checking email addresses. Developers and large corporations have thus bolted additional functions onto the mail log, thus retrofitting sender verification. DMARC (Domain-based Message Authentication, Reporting, and Conformance) [1], which is the result of cooperation between Google, Yahoo, and other major corporations, seeks to reduce spam and tackle the problem of sender verification at the root.
Based on SPF and DKIM
DMARC checks the domain used by an address, thus discovering whether the sender is legitimate. To check the domain, DMARC relies on two established technologies: DKIM (Domain Keys Identified Mail) and SPF (Sender Policy Framework).
DKIM is a technology developed by Yahoo, which practically makes the DNS servers a CA and supports mail verification within the scope of asymmetric encryption. When the receiving mail server receives an email message, the message is signed with a digital key. DMARC uses the public key provided by the DNS server in the sender's domain to verify or refute the origin of the mail. SPF uses TXT entries in domain zones to determine which servers are allowed to email from this domain.
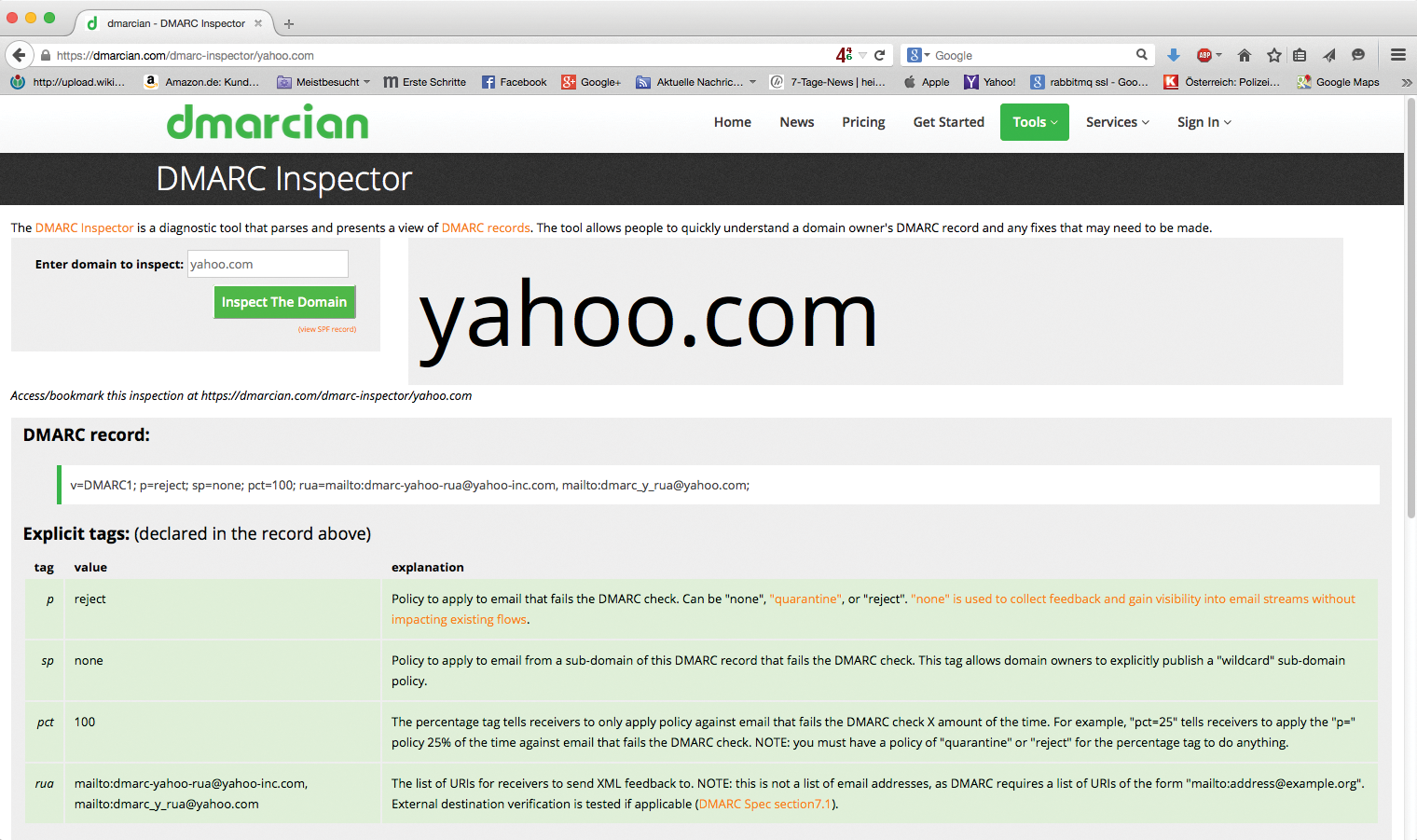
DMARC combines these two features and adds a new feature on top: Admins can create a set of rules to decide whether or not incoming email has successfully negotiated SPF or DKIM. In addition to the existing TXT records for DKIM and SPF, admins simply create a third TXT record for DMARC that describes what to do with messages that fail SPF or DKIM. The record for Yahoo, one of the co-inventors of DMARC, is merciless:
v=DMARC1; p=reject; sp=none; pct=100; rua=mailto:dmarc-yahoo-rua@yahoo-inc.com, mailto:dmarc_y_rua@yahoo.com;
The entry ensures that incoming email for http://yahoo.com is always rejected if DKIM or SPF fails (p=reject). However, the rule does not apply for subdomains of http://yahoo.com (sp=none). The pct value states (as a percentage) the maximum proportion of rejected emails (Figure 1). Using the ruaparameter, Yahoo also stipulates that a report is sent to the provided email addresses for each message that is rejected.
Software Support Needed
DMARC has established itself with many providers, and it has already been submitted to the IETF for standardization. Nevertheless, not all the problems have been solved, as Yahoo painfully learned in April 2014. The strict DMARC policy made it virtually impossible to reach Yahoo.com without SPF and DKIM, but older mailing list managers, in particular, do not support DKIM and SPF.
Older systems sometimes pick up incoming emails and forward them to all list participants, without customizing the from field in the mail – which equates to a DKIM and SPF fail. If you have your mail account with Yahoo and participate in mailing lists, and your software is not up to date, you can expect problems.
