
Tested: Tenable Nessus v6
SecurityX-Ray
Nessus is a network and vulnerability scanner for Windows, Linux, Unix, and Mac OS X computers. The software relies on the client/server principle; one Nessus server on the network runs nessusd, and the clients either connect locally or via a remote computer to this service. Security is ensured by SSL certificates and passwords.
When the server launches, the software automatically loads additional plugins if they are installed. With the help of these plugins, Nessus analyzes the operating systems, interfaces, services, and daemons on the network and returns the results to the server. Programmers develop these modules with Nessus' own Nessus Attack Scripting Language (NASL). The result of the check is a list of identified vulnerabilities and open ports, which Nessus discovers with the help of Nmap.
Although this arrangement sounds very much like open source, Nessus became a proprietary product by Tenable Network Security 10 years ago. Up to version 3.0, the product was released under the GPL, but this stopped in October 2005. To continue providing a free scanner, the open source project OpenVAS was formed; it builds on the last free version (2.2) of the scanner and has been developed independently ever since the fork.
Focus on Mobile Devices and Virtual Environments
At the end of November 2014, Tenable presented the current version 6 of the Vulnerability Management Platform and extended the software to include security features for mobile devices, virtualized environments, and cloud environments [1]. Nessus thus now offers more than 100 different policies for system hardening. The idea is for the scanner to find more vulnerabilities and malware out of the box than other scanning products and services currently on the market. Thanks to these immediately deployable templates, administrators can implement best practices without delay and proceed to test for compliance.
The other Nessus v6 features include the new Scan Policy Editor, which allows IT professionals to adapt policies more easily that match their internal compliance standards, a brand-new History tab for storing and managing older scans, and a RESTful API that facilitates the task of integrating Nessus v6 in into various other dynamic IT landscapes.
Rapid Installation
The installation of Nessus 6.2.1 was a pleasingly uncomplicated experience [2]. This is a major advantage when you need to work with such a complex construct as a vulnerability scanner. After downloading the trial version from the vendor website [3], you need to select your target platform: Windows, Mac OS X, Linux, or FreeBSD. We decided to download and install on Windows Server 2008 R2 and thus selected the MSI installation package for x64. Table 1 lists the system requirements for the supported operating systems.
Tabelle 1: System Requirements
|
Operating System |
Versions |
|---|---|
|
Windows |
Windows Server 2008, 2008 R2, 2012, 2012 R2 (x86, 64), Windows 7 and 8 |
|
Linux |
Debian 6/7, Kali Linux, Fedora 20/21, Red Hat ES 5, CentOS 5/6/7, Oracle Linux 5/6/7, Red Hat ES 6/7, SUSE 10/11, Ubuntu 10.04 (9.10 package) through 14.04 |
|
Mac OS; FreeBSD |
Mac OS X 10.8/10.9/10.10 (x86-64); FreeBSD 10 (x86-64) |
The Windows download was manageable, weighing in at just under 23MB and was available within a couple of seconds on the test server. After double-clicking, it was the standard procedure with an InstallShield wizard, accepting the licensing conditions and selecting a path for saving the results in the filesystem.
A few seconds later, we had the WinPcap 4.1.3 installation window on our screen; Nessus relies on the technical underpinnings of the free program library. From a practical point of view, the WinPcap driver supports low-level access to the network interface card. The program library is based on the popular Unix libpcap library, which implements the pcap interface. The packets transported over the network are grabbed by the WinPcap modules, working around the protocol stack, and then processed. Installing the program library in our lab took less time than typing this paragraph.
Web Interface-Based Management
After the install, the web browser automatically launched on the server showing us the content of the page on port 8834. This showed us a note to the effect that we needed a secure HTTPS connection. Only the developers know why the installer doesn't automatically switch to HTTPS. Clicking on the link triggered the next error message, saying that our ancient Internet Explorer 8 was not fit for the purpose, which is bad news for administrators who want to install the program on Windows Server 2003. Armed with a freshly downloaded Mozilla Firefox, we pressed on.
A wizard popped up to say hello and prompted us to create a password-protected account for accessing Nessus. This was followed by a slightly longer phase in which the software downloaded the required plugins before proceeding to initialize them. After completing the plugin installation, the login dialog for the recently defined administrative user, and access to the very clear-cut web interface were then released. In the top right-hand corner was an orange-colored alert symbol with a text message drawing our attention to the fact that the evaluation version would stop working in seven days.
If you check out the top right-hand corner of the window, you will find options for modifying your user profile, logging off, discovering new features, or modifying the software's basic settings. These settings include, for example, the path for the dump files, whether or not to install software updates automatically, or whether to perform network scans at reduced speed. The online help really is online and takes you directly to the Tenable website.
Fast Malware Scan
The most important commands are on the left-hand side of the window: New Scan and My Scans. We were a bit nervous about the outcome of the test – how would our Windows Server 2012 R2 domain controller with its Exchange 2013 installation fare in the security scan of our lab environment? Pressing New Scan told the software to open a menu with a total of 15 different scans from a library in our browser.
Some tests, including Audit Cloud Infrastructure, Mobile Device Scan, Offline Config Audit, Policy Compliance Auditing, and SCAP Compliance Audit, require you to have a subscription, so they were not available for the trial version. This just left us with Credentialed Patch Audit, GHOST (glibc) Detection, Web Application Tests, Bash Shellshock Detection, the free Advanced Scan, the Basic Network Scan, and the Windows Malware Scan. We went for the latter, defining our Windows test server as the target.
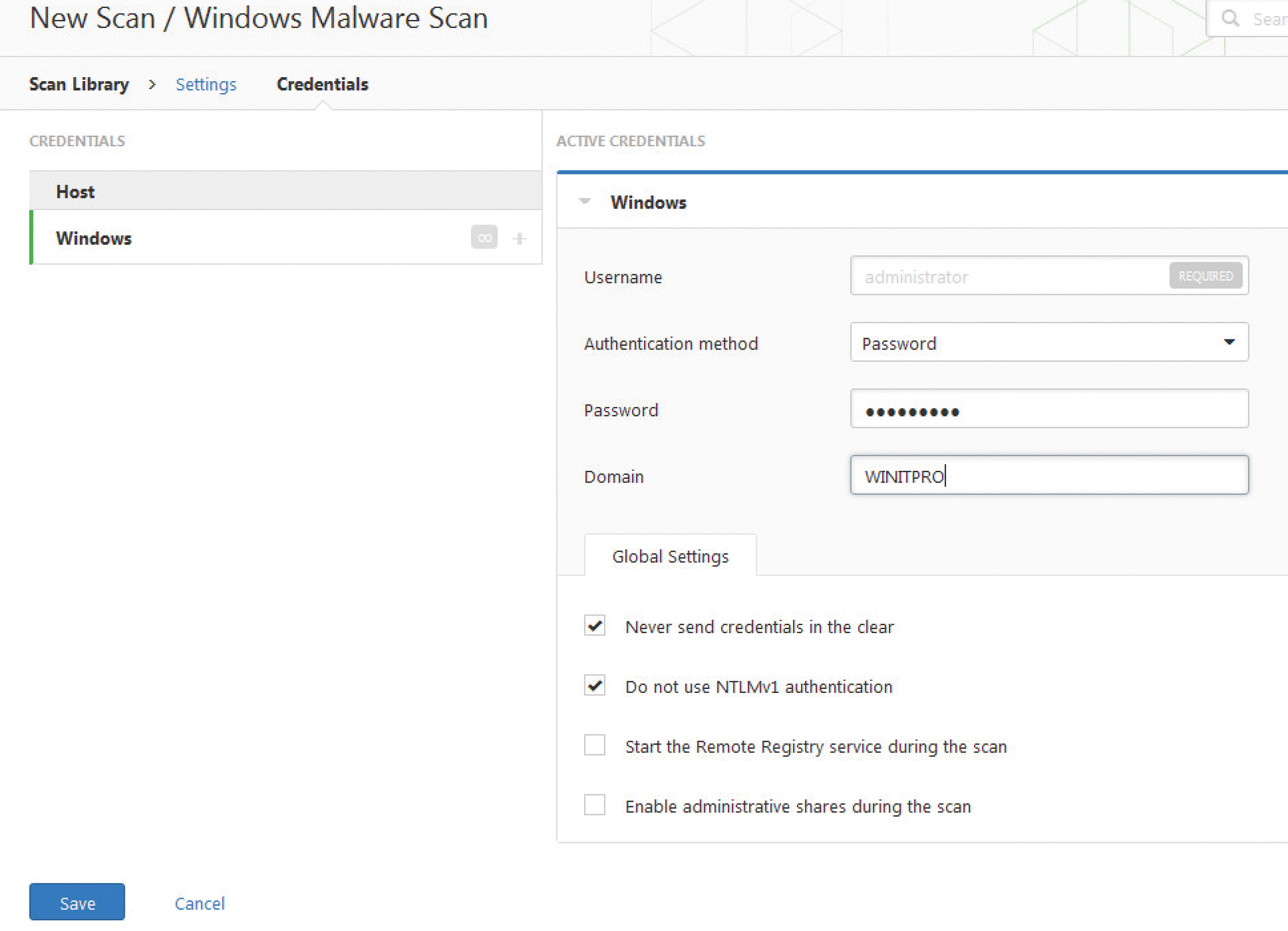
For the initial test, we had very little to fill out: define the name, enter a description, specify the folder (I chose My Scans), and define the target. As the targets we entered our server's IP address – at the time, the server was accessible on the local network with its Windows Firewall disabled. However, you can also enter IP address ranges or hostnames in this input box. Pressing Save threw an error message, because we needed to enter credentials for Windows. If that is going to boost our security, why not?
In the dialog window (Figure 1), we could check a couple of additional parameters, such as Never send credentials in the clear and Do not use NTLMv1 authentication. Thank goodness. After all, it is definitely not a good idea to publish the domain password for any old scanner to sniff. After pressing Save again, the scan launched, and we saw the first results coming in just a minute later.
Surprisingly, the scan completed quickly. A (1) to the right of My Scans indicated some reading material waiting for us. One mouse click later, we were reading an overview of the scan, and the predominant color soon calmed our nerves: Everything was blue, which denotes informative, rather than critical, errors. Nessus v6 drew our attention to an overview of all the running processes on our Windows test server, with a tree structure of the subprocesses. The explanation said this report is simply an overview of the processes active at the time of the scan for forensic investigations.
A second piece of information is simply a CSV-formatted list of the loaded modules. In other words, Nessus v6 found that everything was okay, even though Windows Firewall was disabled on the server. That said, this is a "Malware Scan," and our machine is not infected according to the local antivirus program either. Somewhat farther down in the settings for the Windows Malware Scan, we found some really exciting extensions for the test. Administrators can add MD5 hash values for potentially dangerous files, but also hash values for files that are guaranteed to be harmless. Also, a "Host file whitelist" lets you exclude known files from a scan.
Old Is Not Always Bad
For our next test, we chose the Basic Network Scan for the complete IP segment 192.168.1.0/24. After the scan started, it took far longer for Nessus to come back with its results this time. No fewer than 21 minutes later, the scanner presented the results after testing a total of eight devices on our lab network (Figure 2). We were fairly surprised about the total 109 vulnerabilities and four recommendations.
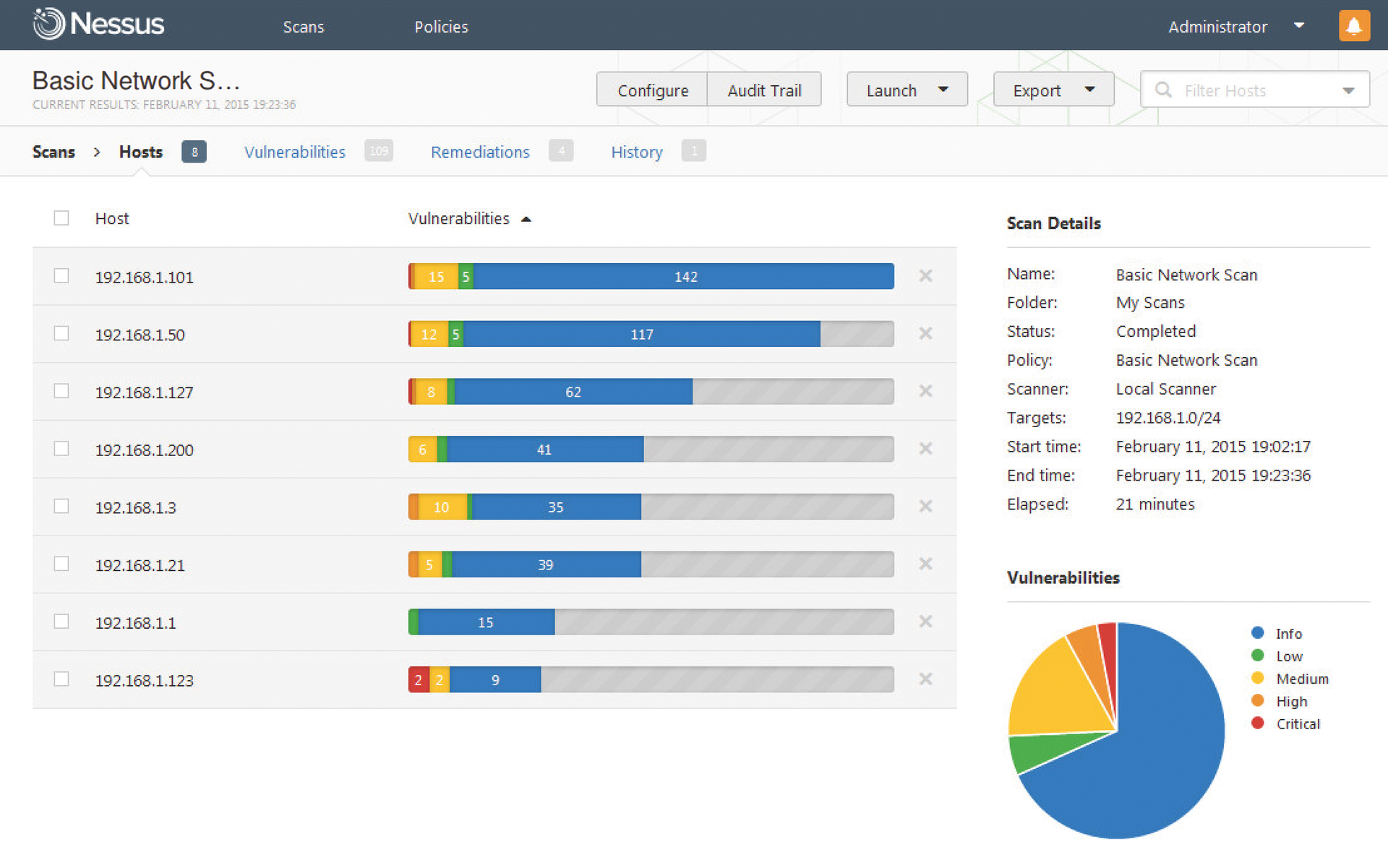
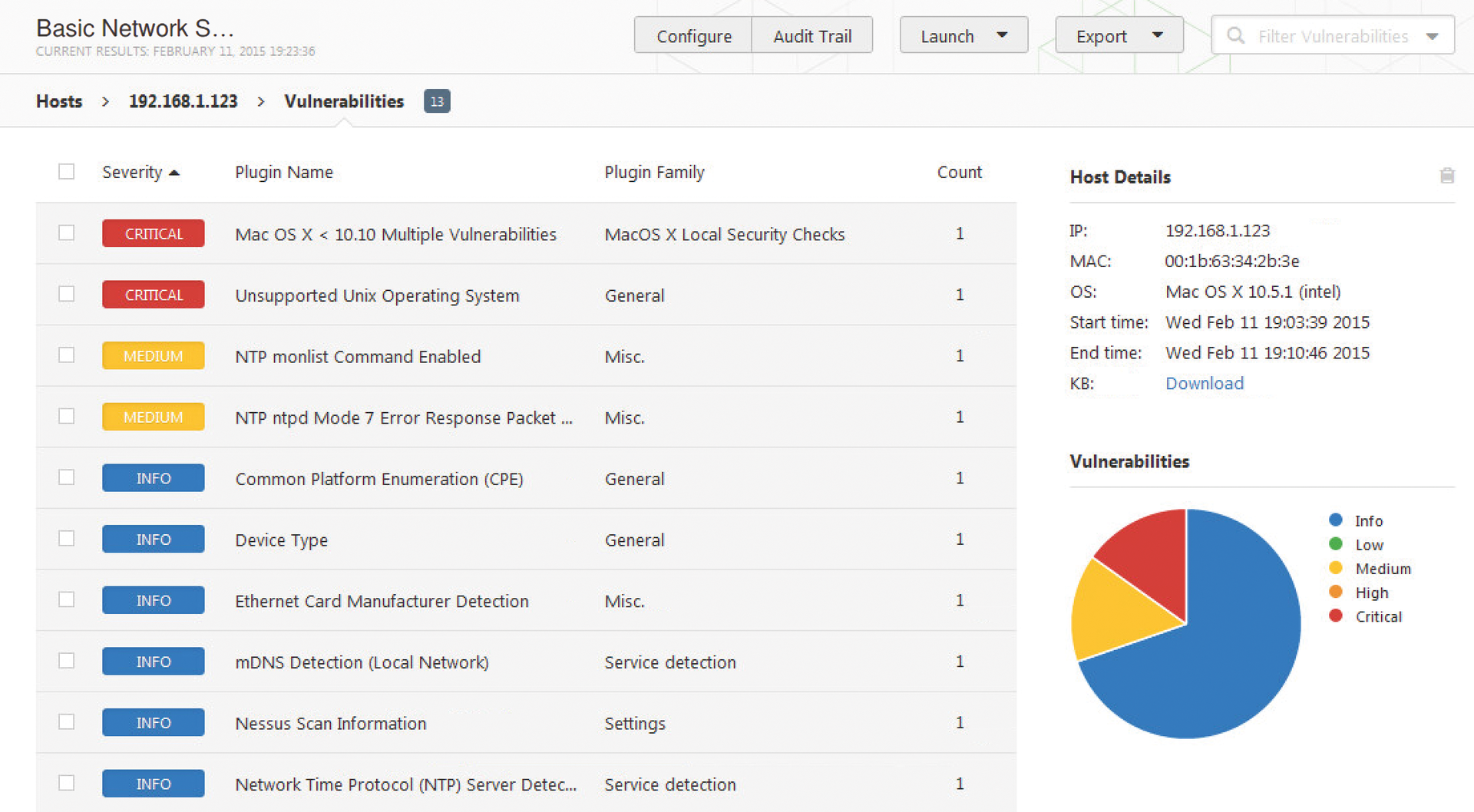
The large number of issues were related to an obsolete MacBook running OS X 10.5.1. But, instead of providing a detailed list of all the potentially endangered applications and Unix daemons on the MacBook, Nessus took the easy exit and simply reported that all versions below 10.10 are insecure (Figure 3). The CVSS (Common Vulnerability Scoring System) Base Score was 10.0 – that is, the maximum. In other words, it would be insufficient to update the device to the maximum 10.5.8 level, because it would still be considered insecure by Nessus. This made us wonder whether the results might be motivated by an Apple sales strategy.
Our ZyXEL switch on the network just about passed the test, with Nessus correctly complaining about the device responding to the default SNMP Community Strings public and private in its environment. The tests revealed a total of eight open ports on the switch; administrators would do well to consider whether they really need all of these. That said, Nessus classifies the open ports as a low risk. The previously malware-checked Windows Server 2012 R2 also showed a red card because Vulnerabilities in SChannel can lead to remote code execution (MS14-066). Our self-signed SSL certificate was classified as medium risk, and a total of 21 open ports were again only classified as low risks.
For our next test, we pointed Nessus at what is guaranteed to be a vulnerable virtual machine. Metasploit, an open source project for computer security – which offers information on vulnerabilities and is used to develop IDS signatures for penetration tests – offers a virtual machine based on Linux with a number of misconfigurations and unprotected features. As you would expect, Nessus v6 again discovered a large number of vulnerabilities and listed them accordingly.
Conclusions
No administrator has the time or inclination always to trigger and evaluate security tests manually. As you might expect, Nessus v6 offers a scheduler for scans that you have defined, as well as email notification of the results. If you want to perform security audits automatically and regularly, this is the perfect choice of software.
If you want to know whether your devices and servers are secure and do not want to rely on an external IT security professional to do so, Nessus v6 will show you after just a couple of minutes which controls your IT staff need to tweak to boost security in the data center and on the network. Table 2 summarizes our evaluation of Tenable Nessus v6.
Tabelle 2: Tenable Nessus
|
Product |
Software-based vulnerability scanner |
|
Vendor |
Tenable Network Security http://www.tenable.com |
|
Price |
One-year subscription for Nessus Professional starts at $2,190 (EUR1,590). |
|
ADMIN rating (max. 10 points) |
Security checks 7Security recommendations 7Reporting and overview 7Installation and operation 9System requirements 8 |
|
This product is |
perfect for companies that want to check and permanently ensure the compliance of their servers and applications software in a complex landscape.useful, with some restrictions, for companies that are not too large and want to verify their security setup without having an internal IT security department.not useful for small businesses that just own one or two servers. |
