
Detecting intruders with Suricata
Finder
In the past, network attackers were much like purse grabbers or "smash and grab" muggers: They would find something they wanted, grab the goods, and run. Today's Advance Persistent Threats (APT) are much more insidious and dangerous. Instead of smashing and grabbing, attackers can find a way to steal your identity and hang around for a long period of time (see the box titled "Dwell Time." To thwart this type of long-term attacker, you need a different, more methodical approach.
For many admins, the Snort Intrusion Detection and Prevention System (IDS/IPS) [1] is the first line of defense, but alternative tools also exist – and some of those alternatives offer advantages in certain situations. This article describes Suricata [2], an open source IDS/IPS sponsored by the Open Information Security Foundation (OISF) [3]. Suricata can read Snort rulesets, which makes it easy to support both systems or even migrate if you decide that one of the tools is better suited to your environment.
Why Suricata?
The homepage of the Suricata website begins with the developers' own list of "Top 3 Reasons You Should Try Suricata":
- Highly Scalable – Suricata is multi-threaded, which maximizes the efficiency of a system configured to work as a Suricata sensor. According to the developers, you can achieve 10-Gbit speeds on real traffic without sacrificing ruleset coverage.
- Protocol Identification – The most common protocols are automatically recognized by Suricata as the stream starts, thus allowing rule writers to write a rule to the protocol, not the expected port.
- File Identification, MD5 Checksums, and File Extraction – Suricata can identify thousands of file types. Suricata also calculates MD5 checksums on the fly, so you can monitor changes to system files or search for malware files with known checksum values.
A quick comparison with the popular, and also powerful, Snort is perhaps the best way to begin. Suricata has a completely different code base, even though it supports Snort-based rules. Figure 1 shows how Snort operates when it is detecting traffic. The packet sniffing, pre-processor, and detection engines are completely separate.
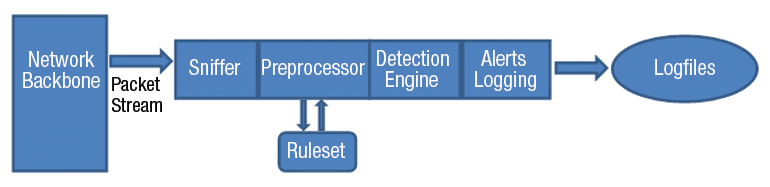
Notice especially how Snort separates the sniffer and preprocessor functions. These functions allow Snort to quickly grab network data, then process it quickly before applying rules. The ruleset function is separate.
Snort's creators have a good reason for separating these functions: The preprocessor function allows Snort to quickly identify certain traffic streams. Otherwise, applying rules to certain traffic streams would take considerable time and very quickly result in a situation where even moderate amounts of network traffic would overwhelm Snort.
Figure 2 shows the Suricata packet processing system. Notice the difference: Whereas Snort typically has a separate sniffer and preprocessor function, Suricata unifies this process when acquiring packets. Also notice that Suricata has a separate decoding function that allows it to inspect the data stream at the application layer. Then, Suricata is able to apply a chain of detection strings. The result is then sent to the network screen, or to a database to save for a later time. The result of this process is that Suricata seems to take a more layered approach to reading and sifting through information.

Both Snort and Suricata have advantages, but for some situations, Suricata might be a better option.
Installing Suricata
Like Snort, Suricata is an open source intrusion detection system that is also capable of intrusion prevention. In other words, Suricata won't just identify attacks; it can also reach out onto the network and disrupt traffic it marks as suspicious. Suricata has a stable code base, and it is used throughout the industry. Although hardly as widely adopted as Snort, Suricata has the ability to monitor both IPv4 and IPv6 traffic, as well as identify security issues. Suricata is quite flexible, and it runs on all flavors of Linux. As of this writing, the latest stable version of Suricata is 2.07.
To install Suricata with both intrusion detection and intrusion prevention capabilities, you will want to install the Libp supporting libraries:
$ sudo apt-get -y install libpcre3 \
libpcre3-dbg libpcre3-dev \ build-essential autoconf \
automake libtool libpcap-dev \
libnet1-dev \ libyaml-0-2 libyaml-dev \
zlib1g zlib1g-dev libcap-ng-dev \
libcap-ng0 \ make libmagic-dev
Once finished with these support packages, you can grab Suricata from the web site:
$ wget \
http://www.openinfosecfoundation.org/\
download/suricata-2.0.7.tar.gz
tar -xvzf suricata-2.0.7.tar.gz
cd suricata-2.0.7
Then, take the typical steps to compile the source files into a binary:
./configure --prefix=/usr \
--sysconfdir=/etc --localstatedir=/var
make
sudo make install
sudo ldconfig
I've found that it's sometimes necessary to manually create a log folder, as follows:
$ sudo mkdir /var/log/suricata $ sudo mkdir /etc/suricata
Make sure these folders are owned by the Suricata process, as well as by root. Then, copy the files into the proper directories:
$ sudo cp classification.config /etc/suricata $ sudo cp reference.config /etc/suricata $ sudo cp suricata.yaml /etc/suricata
Congratulations! You now have a working version of Suricata. Understand, though, that Suricata currently doesn't have any rules installed. If you wish, you can download rules from Snort or obtain them from co-workers or third-party sources. You can also download default rule files from the Emerging Threats project. I don't find that these rules are all that special, but they make for a good foundation that you can build on and customize. To obtain the default rules, do:
$ wget \
http://rules.emergingthreats.net/\
open/suricata/emerging.rules.tar.gz
tar zxvf emerging.rules.tar.gz
cp -r rules /etc/suricata/
Once you have downloaded and copied some rules, it's time to start Suricata to make sure it works. If, for example, you have a typical eth0 interface, you would issue the following command to start the application:
$ sudo suricata -c \
/etc/suricata/suricata.yaml -i eth0
Once Suricata has started, you can use the suricatasc command to verify that Suricata is working. Figure 3 shows how it is possible to verify the version simply by using suricatasc with the -c version switch.
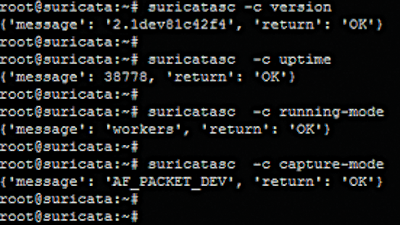
The result of the command in Figure 3 is information about the mode in which Suricata is running. Pay special attention to the runningmode option, which informs you that it is working properly. The capture-mode switch is useful, because it will tell you whether or not Suricata is capturing packets. The AF-PACKET_DEV value lets you know that Suricata is working. The iface-stat switch reports the status of the interfaces used by Suricata:
$ sudo suricatasc -iface-stat eth0 "drop" 280000404 "invalid checksum": 0, "pkts: 80595950"
The preceding output shows that 280000404 packets have been dropped out of 80595950, and that no packets have had invalid checksums.
Troubleshooting the Implementation
When I've had problems installing Suricata, I've often run into dependency issues in regard to libpcre3. To avoid dependency issues, you might want to start with a flavor of Linux that already has Suricata installed, or is at least primed for a Suricata implementation. I've found that Debian-based systems, including Ubuntu, are quite suited for Suricata.
You might also need to make sure that all of the relevant services are running:
$ sudo service barnyard2 start $ sudo service snortd start $ sudo service httpd start
Creating a Custom Framework
To customize Suricata, edit the /etc/suricata/suricata.yaml file. Once you are editing the file, it is possible to use a fairly simple syntax:
alert icmp any any -> \
any any (msg:"PING detected"; \
sid:2; rev:1;)
The preceding syntax defines an alert for ICMP traffic, similar to iptables. This line tells Suricata to look for any ICMP traffic from any interface. Once Suricata discovers this traffic, it will issue an alert to the log files saying PING detected.
When learning about the traffic gaps, it's important to first understand the nature of your organization. Focus on the goal of your business. If you are working for a retail business, you will need to make sure your e-commerce servers and databases are properly protected.
Assume you are working for a company that has a web server that processes credit card information. Suppose you wish to create some rules in Suricata that detect unencrypted credit card transactions. You would want to do this to make sure that your developers are properly encrypting information. You would also want to see if a long-lurking hacker has somehow obtained access to your e-commerce server and is sending unencrypted data to a server outside of your network. To create such a rule, you could insert the following into the /etc/suricata/suricata.yaml file. Use any text editor and enter a rule such as:
alert tcp any any <> \
any any (pcre:"/5\d{3}(\s|-)?\
\d{4}(\s|-)?\d{4}(\s|-)?\d{4}/"; \
msg:"MasterCard number \
detected in clear text";content:\
"mastercard";nocase;sid:9000001;rev:1;)
The preceding rule has Suricata look for MasterCard information. You can also enter information for American Express cards:
alert tcp any any <> \
any any (pcre:"/3\d{3}\
(\s|-)?\d{6}(\s|-)?\d{5}/";\
msg:"American Express card number \
detected in clear text";content: \
"amex";nocase;sid: 9000003;rev:1;)
You might have noticed that the preceding rules are Snort rulesets. You've already begun to create an intrusion detection system based on a flexible, custom framework. But, you don't have to stop here.
Using Suricata
Once Suricata is up and running, you can log in and view traffic alerts. Figure 4 shows Suricata in traditional IDS mode.

In Figure 4, Suricata is showing the results of its activities, which include identifying issues with web and DNS traffic. The useful part of this report is that it lets you identify traffic types and where they originated. Yes, attackers are capable of spoofing IP addresses, but it is still useful to try and find the origin of the traffic.
Figure 5 shows another view that is particularly useful. The panel in Figure 5 shows security events over time. Viewing events makes it possible to use Suricata to identify when an attacker has been stealthily mapping your network or a particular network resource.
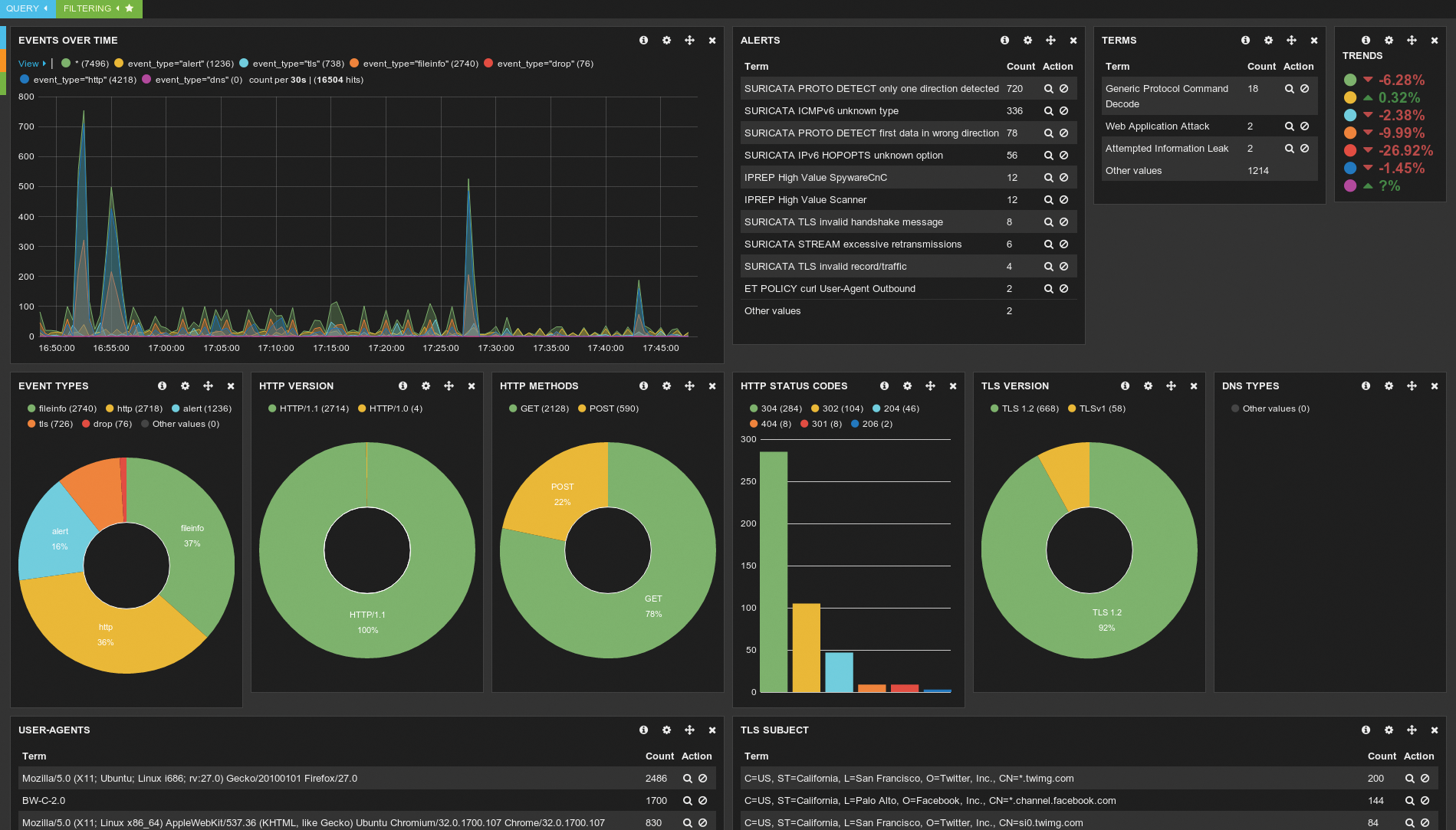
The view in Figure 5 is particularly useful in helping reduce dwell time, because it tracks scanning attacks and other activities over time. If stealth is the key to long-term, persistent hacking, long-term, diligent recording of network activity is one of the ways to stop persistent attacks.
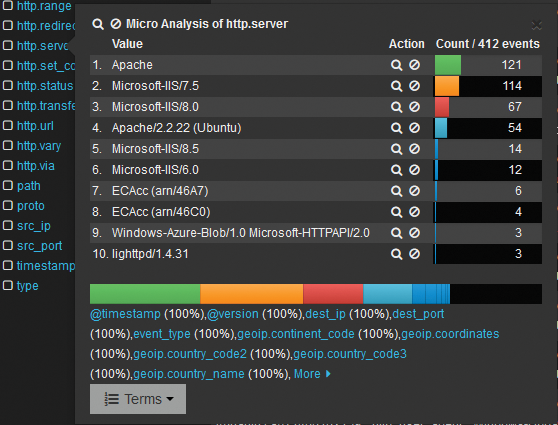
Finally, Figure 6 provides a report of the types of web services available on the network. I have found reports such as the report in Figure 6 useful for identifying older web servers, which are often targets for attack. Attackers often use off-the-shelf software, such as IIS and Apache Server, to exfiltrate information. The ability to detect web servers makes it easy to identify this type of traffic.
Conclusion
Suricata is a useful alternative to Snort and other intrusion detection and prevention systems. If you're looking for a highly scalable intrusion detection alternative that is easily customizable and automatically recognizes many protocols and file types, you might want to consider Suricata for your own network.
