
Handy Windows tools for sniffing network traffic
Sniff Kit
Sometimes you just need a quick answer and don't want to slow down to spin up a big, complicated monitoring application. If you work on a Windows network, three useful tools for sniffing traffic and analyzing network packets are SmartSniff [1], SniffPass [2], and Open Visual Traceroute [3]. In this article, I introduce these three handy utilities and also take a look at Microsoft Message Analyzer, which you can call in for more advanced analysis.
Whereas SmartSniff records networks and packets much like Wireshark, SniffPass investigates the transmission of unencrypted passwords. Open Visual Traceroute in turn brings the individual hops from network packets onto the screen, including their targets on the Internet. The tool does not just intercept packets, it also visualizes their path on a globe.
Network Analysis Using SmartSniff
You can use SmartSniff (Figure 1) on almost all Windows systems, including Windows 8.1 and Windows Server 2012 R2. Download, unpack, and start the tool to analyze your network. You won't need to install. The sniffer process will start when you click the green triangle. However, you first need to choose the network adapter on which the tool will be sniffing for network packets. SmartSniff collects TCP/IP packets and displays their contents without the need to install additional drivers. As with most Windows scan programs, you need to install the WinPcap extension [4] for advanced options.
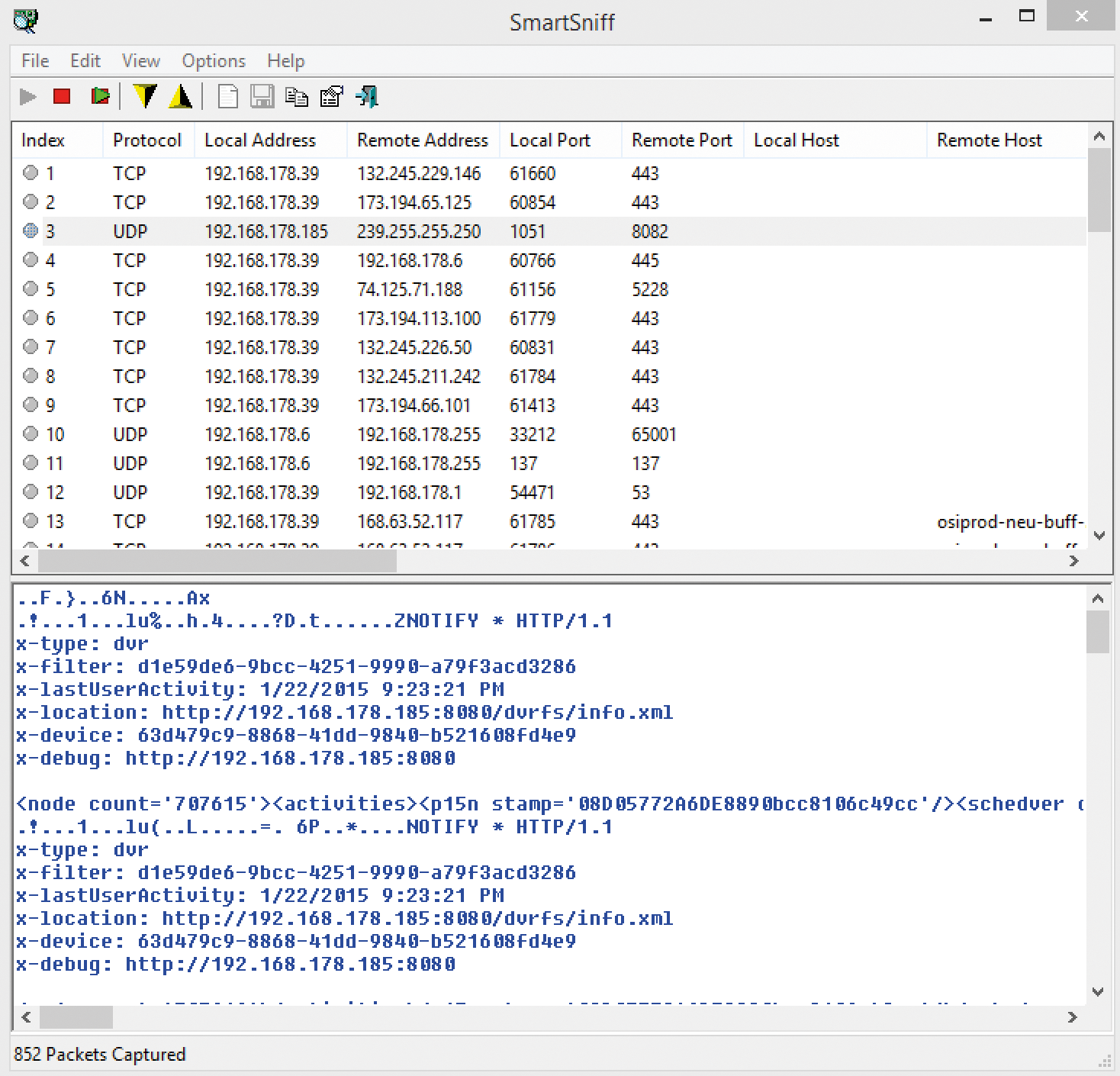
You will see the local IP address, the packet's remote address, the ports used, and possibly also the DNS name, the size of the packet, and the exact times of transmission in the results window. Click on Options | Capture Options to change the network card later. You can also specify whether to use the restricted RAW mode or the superior WinPcap driver mode.
If you still have Microsoft Network Monitor installed on the computer, you can use this driver for advanced scanning options. However, SmartSniff is not yet compatible with Microsoft Message Analyzer, the successor to Microsoft Network Monitor.
If so desired, you can display the country to which the packet was sent in the IP Country column. Download the current, and free, country file IpToCountry.csv [5] (link in the lower-right corner of the website). Unpack the archive in the same directory from which you started SmartSniff. If you now restart the tool and start a new scan, you will see the packet destination country in the column on the far right.
Analyzing Packets in Real Time
When you click on a packet, you see its contents in the field below. You can assess the data according to various criteria. If you click on Options | Display Mode, you switch between different types of display, including Automatic, ASCII, Hex Dump, and URL List. Depending on the mode, SmartSniff displays different information in the packet information window. If set to Automatic, which is the default, the tool checks the first bytes of the data stream. If the bytes contain characters lower than 0x20 (excluding CR, LF, or Tab characters), the tool automatically shows the information in Hex mode; otherwise, SmartSniff uses ASCII mode.
You can also manually enable the mode. Hex Dump mode is slower than ASCII mode. Which to use depends on what data you need and how quickly the measurement needs to take place. The URL List mode filters the display by URL and hides all data except URLs. URL List mode lets you quickly identify which of the packet are sent to various websites on the Internet.
Exporting Packets
You can also export, save, or copy SmartSniff data to other programs, such as Excel, via the clipboard. Simply select the columns whose data you want to analyze later at the top of the window and copy them to the clipboard using the context menu (Figure 2). You can then insert the columns directly into Excel. The Save Packet Summaries option lets you create a text file containing the most important information from the selected packets. Use Export TCP/IP Streams to save the basic packet data and the contents in a text file. If you want to save the whole thing graphically as a report, use the HTML Report – TCP/IP Streams command. The command creates an HTML file with a table and the contents of the packets. At the bottom, you can select the contents of individual packets and copy them to the clipboard using the context menu.
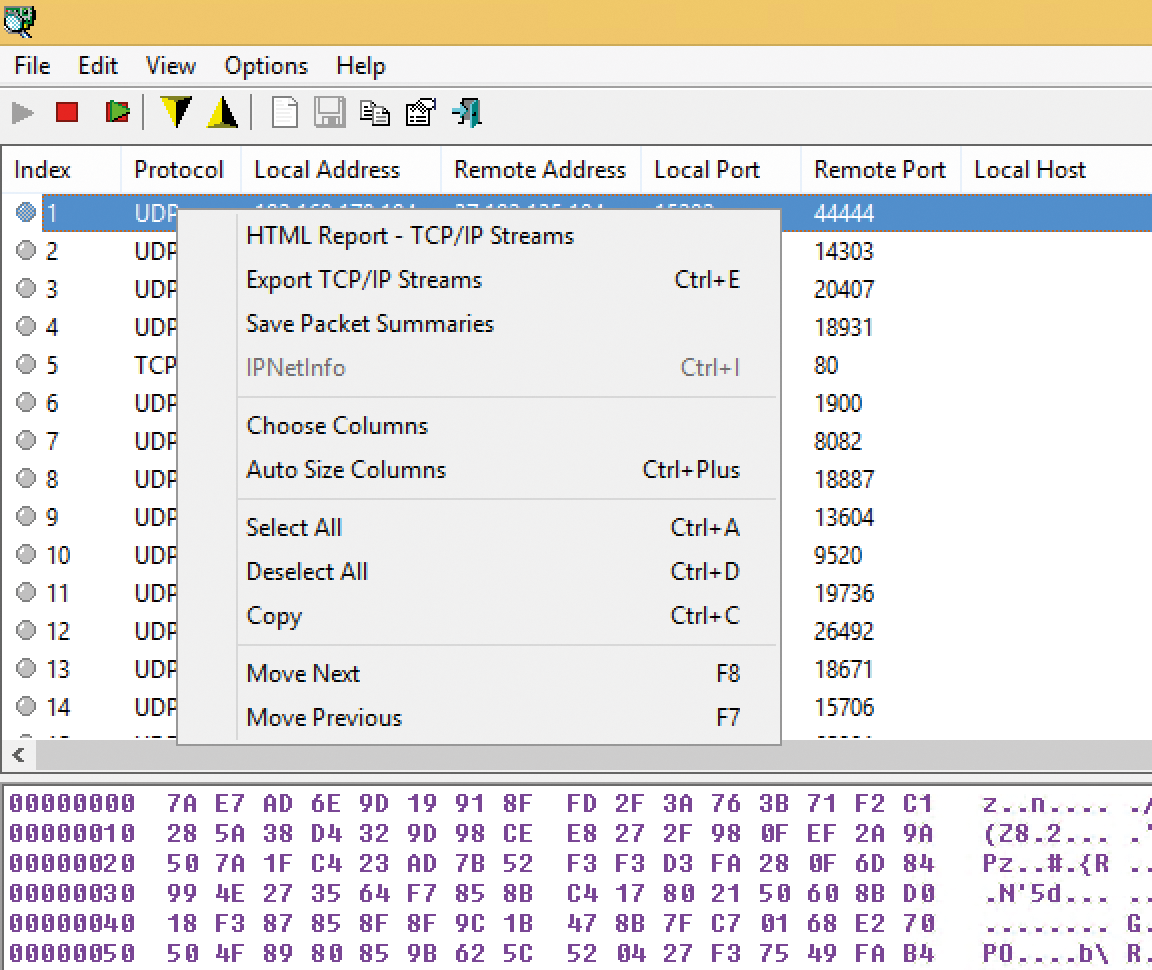
In addition to the option to save individual packets, you can also back up the data from a complete capture process and load it in SmartSniff at any point. To back up the data, stop the capture process and select File | Save Packets Data to File. Then save the process in an SSP file. You can load this file again in SmartSniff at any time and examine it more closely.
Efficiently Filtering Packets
SmartSniff quickly collects a confusingly large volume of data, particularly in large networks with many computers. SmartSniff will help you sort through the mass of packet data. Click Options | Display Filter. Then insert a filter in the window to remove the packets you don't want to see. Make sure you don't use any spaces. See Table 1 for a summary of some SmartSniff filter options.
Tabelle 1: Filter Options in SmartSniff
|
Filter Effect |
Filter Syntax |
|---|---|
|
Only packets with a specific remote port e.g., HTTP (80) |
|
|
Only packets with several specific remote ports e.g., HTTP (80) and NDS (53) |
|
|
All packets in a certain IP range (e.g., 192.168.178.1 to 192.168.178.125) |
|
|
All TCP/UDP packets in a specific port range |
|
Monitoring Processes
SmartSniff can also monitor the processes that send the network packets. Click Options | Advanced Options and enable Retrieve process information while capturing packets. If the tool detects the process, you will see its process ID and the name of the exporting file in the two columns ProcessID and Process Filename. However, this procedure only works if the connection remains open and continues to capture data. Be mindful that this option burdens the computer. You can only analyze this data in real time.
Reading Passwords Using SniffPass
If you forget the password for your FTP access or another program connects via the network, you can use SniffPass to filter out the password in the network traffic on the local machine if it is stored in a program. A security audit is another scenario. If you also want to check whether passwords are sent in plain text on a computer, (e.g., for POP3/IMAP access), you can read passwords from local computers without much background knowledge.
You do not need to install SniffPass; rather, you can simply start it and begin the Sniff process. SniffPass (Figure 3) then eavesdrops in the network or on the local computer until it detects an unencrypted password sent through SMTP, POP3, IMAP4, FTP, or other common protocols.
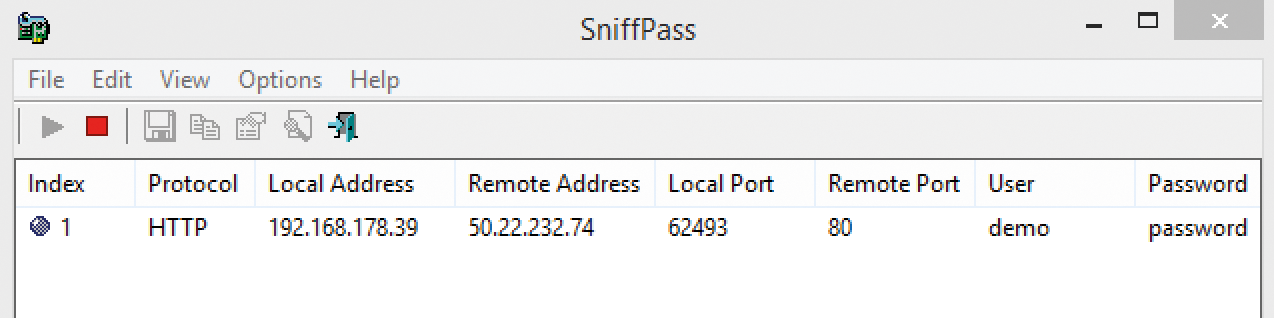
Many routers and switches do not allow such monitoring operations on networks, which means you can only see the data on the local computer. As with SmartSniff, you should therefore use WinPcap. To read passwords on the network, enable the WinPcap mode and the Promiscuous Mode function via Options | Capture Options. However, not all network cards support this mode. To test the function, go to the website [6] and enter demo as the username and password as the password. SniffPass will immediately show the username and password when the sniffer process is started.
Testing WiFi for Security Vulnerabilities
You can check insecure WiFi and read passwords in unencrypted WiFi networks if you use SmartSniff and SniffPass in parallel. This option requires that you have Microsoft Network Monitor 3.4 [7] running on the computer. SmartSniff and SniffPass use a driver from Network Monitor to read data from networks.
Start both programs and call up the settings for capture processes via Options | Capture Options. Enable the Network Monitor Driver 3.x options and click on the WiFi Monitor Mode button. (Some network adapters don't support these functions.) You have the option to select the WiFi card. Choose the Switch to Monitor Mode option and select the channels you want to examine. (Leave the window open while performing the scan or you'll stop the process.)
SmartSniff and SniffPass do not officially support Microsoft Message Analyzer. You can thoroughly test the tools together on computers running Windows 8.1 or Windows Server 2012 R2, but you cannot load the Microsoft Message Analyzer driver. Whether or not data can be read depends much more on the network adapters, the drivers installed, the operating system, and the network devices. Be sure you install WinPcap on the computer.
Tracking Packets Using Open Visual Traceroute
Open Visual Traceroute graphically displays the path of a packet on a map of the Earth (Figure 4), in addition to capturing and displaying packet data. First you need to install Open Visual Traceroute. For a first sniffing process, click Sniffer at the top of the program, enable the TCP, UDP, and ICMP options, then click on the Traceroute icon to start the scan. After a while, you will see the packets and the path they take across the globe.
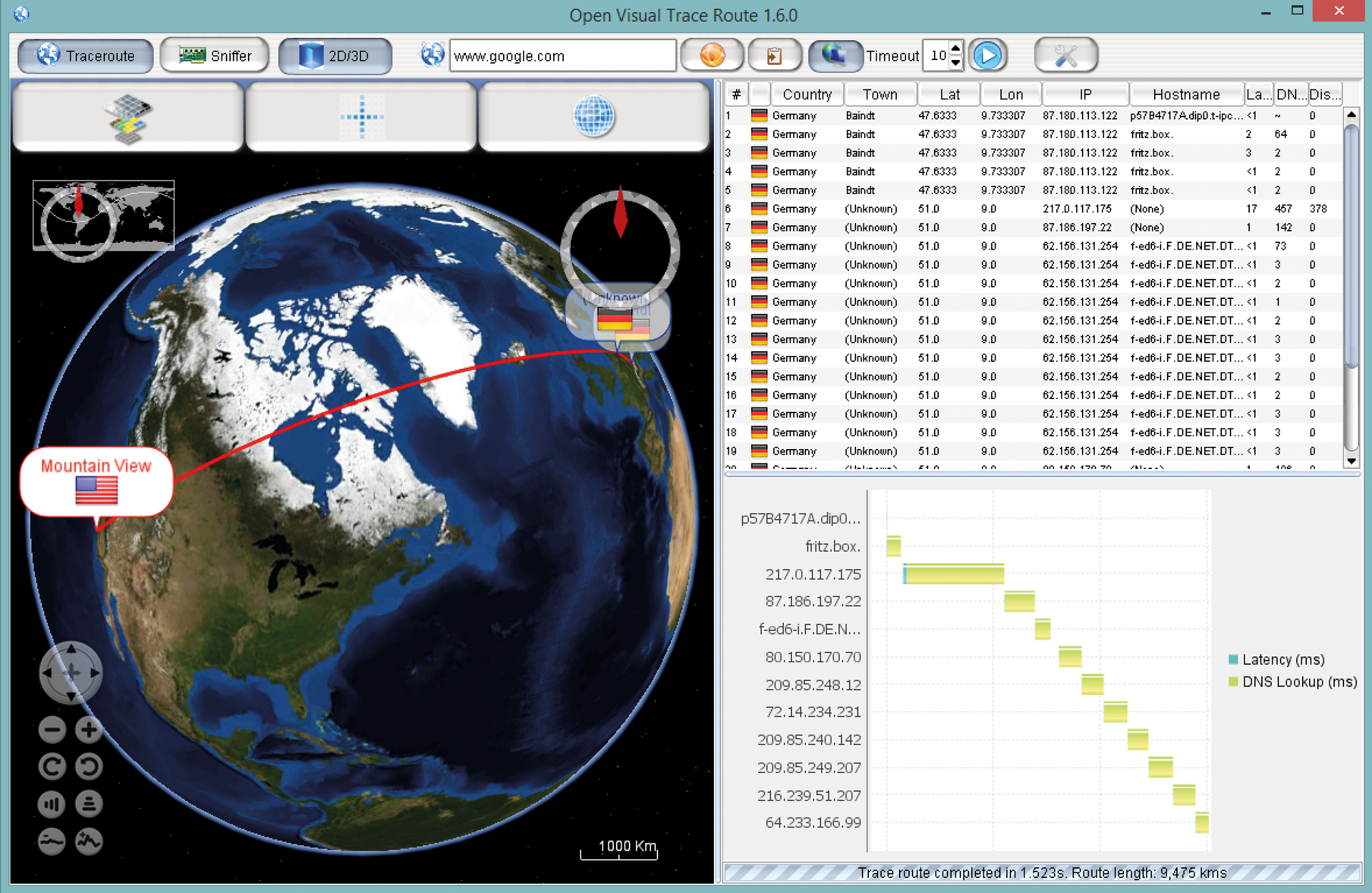
Alternatively, you can track the path of a packet to a specific server. Click on Traceroute and specify the IP address or the server name at the top of the window. When you start the process, you will see the path of the packet.
If you select the hop in the right-hand window, you receive further information and a graphical display for each step. You can zoom in and out of the window using the mouse wheel or the globe symbol. The software provides interesting information that ideally supplements the data from SmartSniff and SniffPass. If your graphics card supports it, you can switch the display to 3D at the top.
Microsoft Message Analyzer
Microsoft provides the Microsoft Message Analyzer [8] for IT professionals who want to perform further analysis. Message Analyzer runs on Windows 7/8/8.1 and Windows Server 2008 R2/2012/2012 R2. You also need .NET Framework 4.5 on the computer.
Unlike the other tools in this article, Microsoft Message Analyzer (Figure 5) is quite complicated and only really suitable for advanced analysis. The message analyzer is just as unsuitable as its predecessor, the Microsoft Network Monitor, for quick captures. You can start a first scan process with File | Quick Trace | Local Network Interfaces. You will need to start the tools with administrator rights in order to perform measuring operations on workstations.
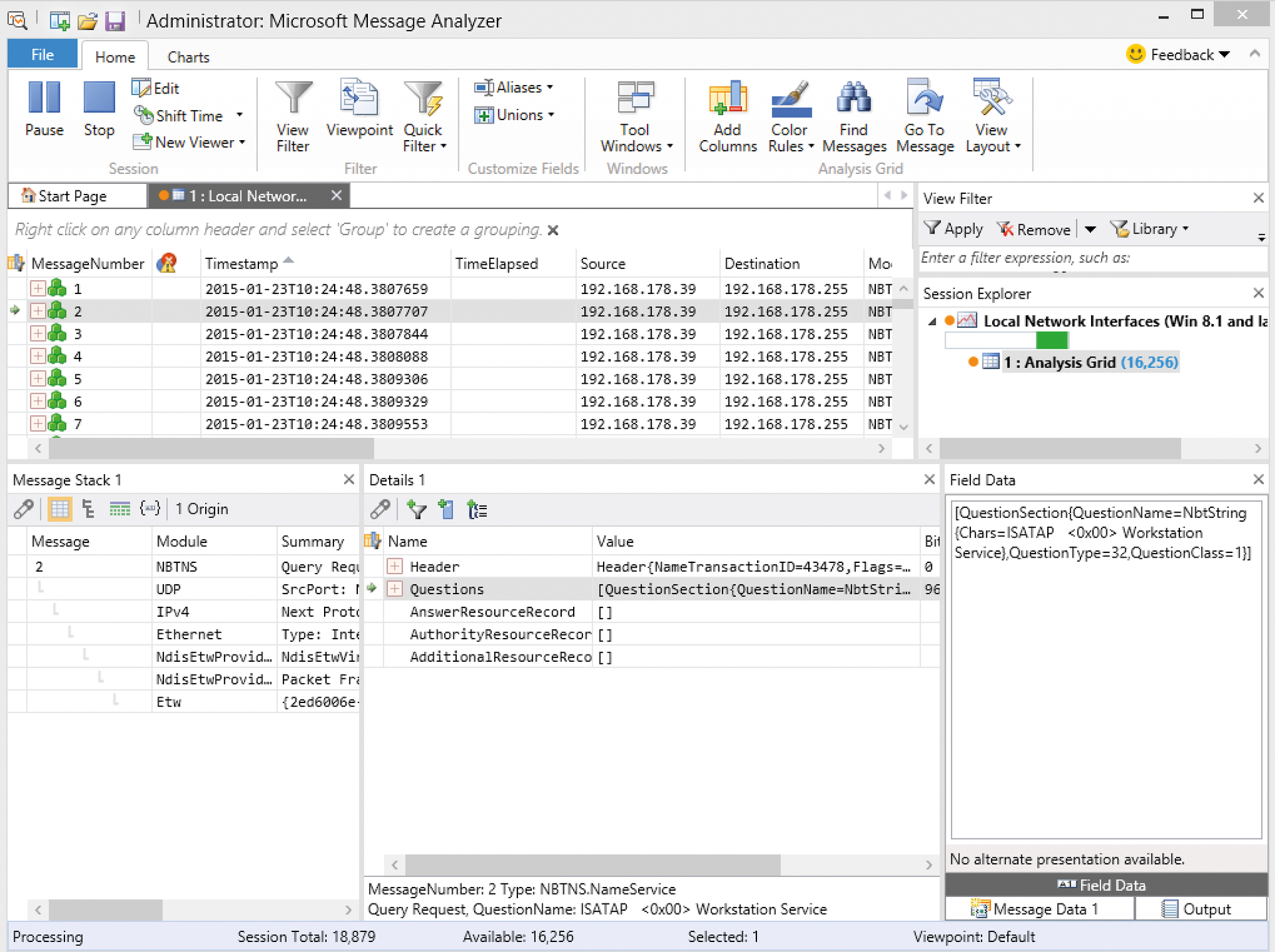
In addition to simple network capture and analysis, you can also carefully examine network overloads and other troubleshooting issues. The new version supports the current SMB protocol from Windows Server 2012 R2. The message analyzer can start sniffing processes on several computers at the same time (Multiple Remote Capture) and send them to a central client. The client collects the data, evaluates it, and displays the result.
Microsoft Message Analyzer can decrypt SSL data. However, you need to install the corresponding certificate for decryption. You will find a comprehensive guide to Message Analyzer in TechNet [9]. Microsoft also shows the capabilities of the new program in a video on YouTube [10]. For more information see the TechNet blog [11].
Conclusion
The free tools SmartSniff and SniffPass are good enough for an initial analysis if you need quick information. Open Visual Traceroute provides an interesting additional option by helping you visualize the path of packets on the Internet. If you need something more sophisticated, you can use the free Microsoft Message Analyzer. Administrators who check the network at regular intervals should become familiar with all of these tools and choose the best option for the task at hand.
