
Advanced Windows security using EMET
Solid Defense
Using Microsoft's Enhanced Mitigation Experience Toolkit (EMET) [1], you can prevent attackers from exploiting security gaps in the software that you have installed on Windows computers. The security technologies used to limit damage cannot completely eliminate security risks, but instead, they meaningfully serve to complement other security measures.
Such measures include installing the latest security updates using Windows Firewall with Advanced Security and using User Account Control (UAC). Additionally, EMET provides a configurable function for determining the trustworthiness of SSL certificates. This function aims to detect and prevent man-in-the-middle attacks.
Installing EMET
You can download EMET for free from Microsoft's website [2]. For use in companies, you have the option of distributing EMET using the System Center Configuration Manager (SCCM) or the software distribution functions of Active Directory's group policies (more on that later). The configuration of EMET can be automated using group policies and administrative templates (ADMX files). EMET supports all current versions on Windows platforms. For clients, these are:
- Vista SP2
- 7 SP1
- 8
- 8.1
The tool supports the following versions on the Windows Server side:
- 2003 SP2
- 2008 SP2
- 2008 R2 SP1
- 2012
- 2012 R2
On Windows Server 2003, a few limitations are described in the release notes and the EMET user guide, which are part of the EMET downloads. Read the user guide before using EMET, because it expands on the important configuration steps and provides an overview of the EMET protection technologies.
Centralized Rollout
You can use software distribution such as SCCM, group policies, or any other method that is capable of distributing MSI packages for large-scale distribution of EMET. The steps for distributing the EMET application using SCCM are:
- Create an application in the SCCM management console based on the MSI file from the EMET download (Figure 1).
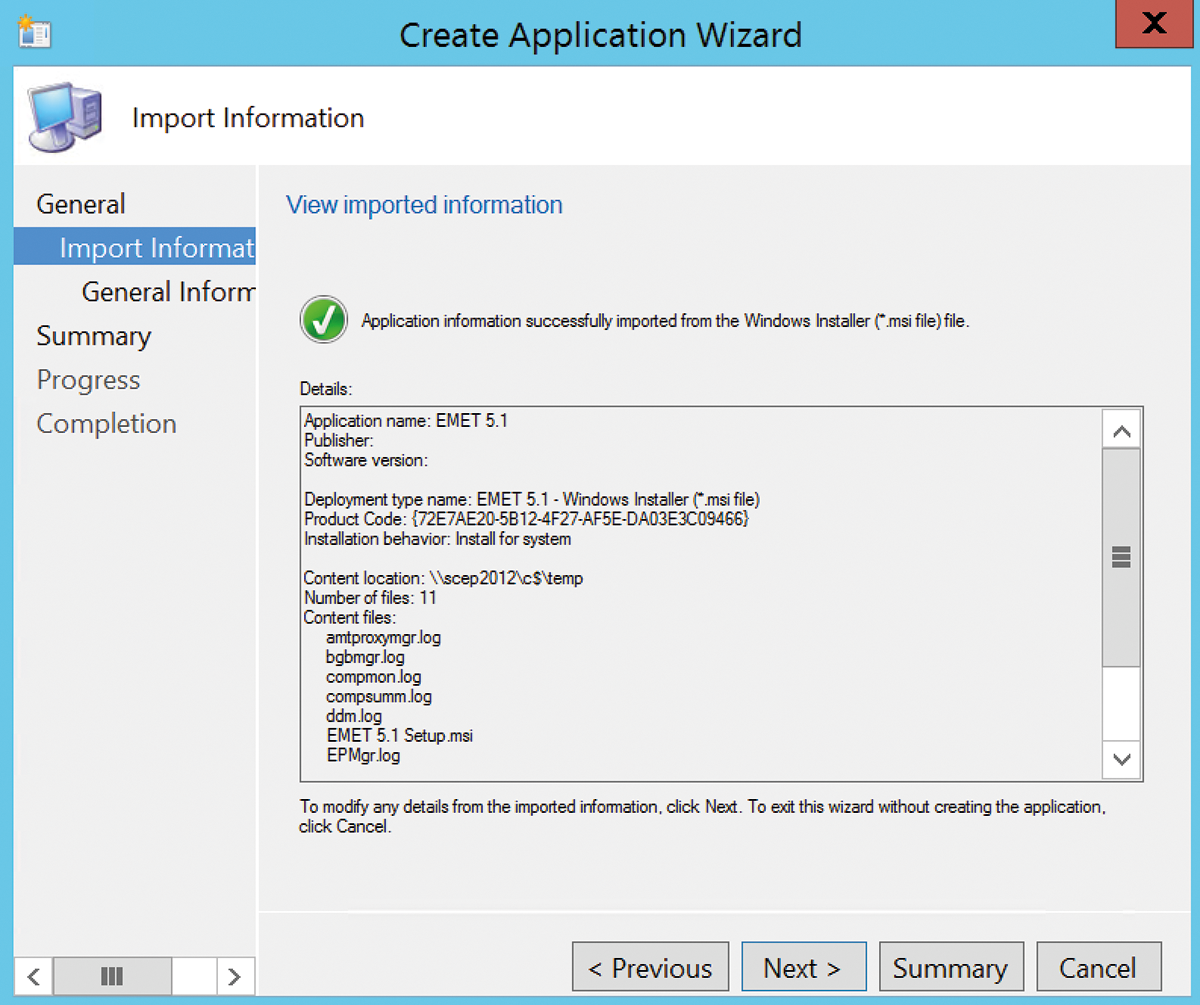
- Create an SCCM package and program.
- Assign the package to an SCCM device collection or create a new device collection.
The EMET user guide and the TechNet websites provide detailed information about distributing EMET using SCCM. Microsoft KB article 816102 [3] provides further information if you want to distribute EMET using group policies.
You can centralize configuration using group policies and administrative template files if you have successfully distributed EMET in your network. Copy the files EMET.ADMX and EMET.ADML from the installation directory into the PolicyDefinitions directory on a domain controller or a workstation with the Remote Server Administration Tools (RSAT) installed. Then, use the central group policies' memory and copy the ADMX and ADML file into the PolicyDefinitions directory of the Active Directory domain's SYSVOL share.
EMET on the Command Line
The EMET_Conf.exe tool is available to administrators wanting to configure EMET on the command line. This approach does not, however, offer the full scope of the EMET GUI. Running EMET_Conf.exe without specifying configuration switches lists all available command-line options. You can determine which protection function should be active for an application in the application settings (Figure 2).
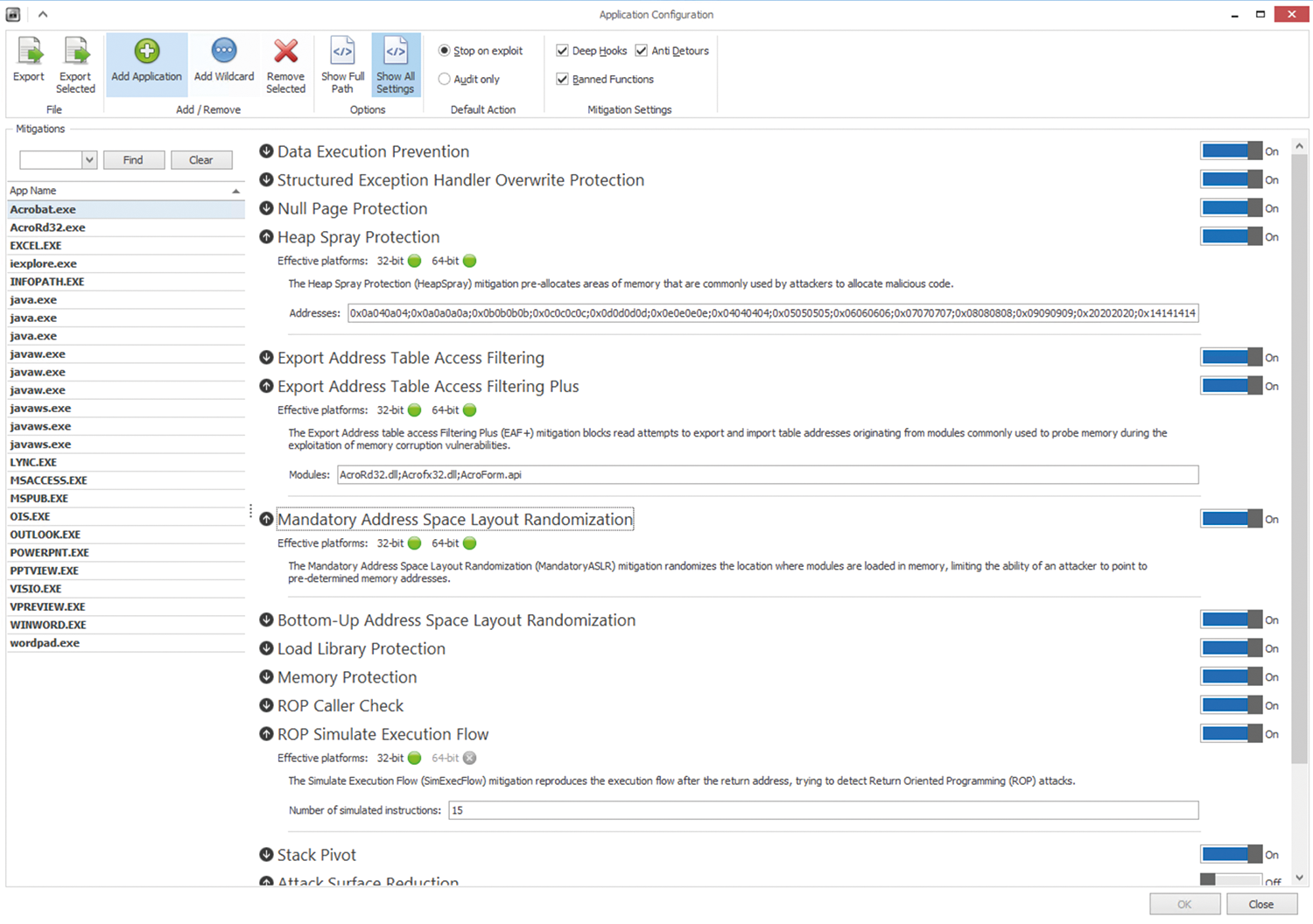
Protection Techniques
EMET can protect against a range of attacks and well-known exploits in Windows. When you look into EMET, you will encounter many abbreviations, such as DEP, SEHOP, Null Page, Heap Spray, EAF, EAF+, ASR, Mandatory ASLR, and Bottom-up ASLR. Do not be confused: The EMET user guide provides a good explanation for many of the terms.
Before using EMET on a large scale on a variety of Windows computers, you should at least have a basic idea of how these technologies work, because activating protections can cause problems for a small number of applications. It is therefore advisable to try EMET in advance in a test environment with the applications used in the company. The standard EMET functions include:
- Data Execution Prevention (DEP)
- Structured Exception Handler Overwrite Protection (SEHOP)
- Address Space Layout Randomization (ASLR)
These functions work system-wide, whereas the other technologies mentioned are used for specific applications. Below, I will explain the three most common mechanisms.
Data Execution Prevention
DEP prevents defective program code from being executed in system memory areas that are reserved for Windows and other authorized programs. DEP has been available as a hardware and software function since Windows XP and can be configured rudimentarily using the Windows Control Panel. EMET expands the DEP functionality and allows applications that were not intended to use DEP and that have problems with the mechanism to take advantage of the DEP function.
Structured Exception Handler Overwrite Protection
SEHOP [4] is a Windows function from Vista SP1 onward that attempts to fend off attacks that are based on overwriting the structured exception handler (SEH). This protection mechanism is available for the run time of an application. SEHOP is enabled by default in Windows 7 and higher. EMET does not then detect whether SEHOP is in use. Windows instead writes the related information in the event viewer's application log.
Address Space Layout Randomization
ASLR is a technique from Vista onward that assigns programs memory address ranges on a random basis. The storage areas are thus no longer predictable, and attacks by buffer overflows can be prevented. The primary function of ASLR is to protect DLLs (Dynamic Link Libraries) and plugins.
Core functions and static dependencies, however, are not protected by ASLR. EMET is also unable to detect the state if you use new operating systems such as Windows 8 or applications such as Internet Explorer 11 or Microsoft Office 2013, where ASLR is enabled by definition. The operating system also writes a corresponding entry in the Windows Event Viewer.
Depending on the operating system you use, it is possible that not all security functions supported by EMET will be available. This is especially true for older versions of Windows, such as Server 2003. Administrators should therefore get to know the operating system-specific functions and limitations before using EMET.
Recommended Settings
The configuration wizard starts after installing EMET. It makes a number of choices when you select the recommended settings and also sets standard applications such as Microsoft Office, Internet Explorer, and certificate settings for well-known sites such as Facebook. You can make changes at any time. After starting EMET you will receive an overview of the system status. This provides information about the DEP, SEHOP, ASLR, and Certificate Trust functions.
The main menu also provides an overview of the local machine's processes running on the system. First, set the level of security that EMET should apply to the system in the ribbon bar in the EMET management console. Click in the drop-down box below Quick Profile Name and select the desired level of safety:
- Recommended security settings
- Maximum security settings
- Custom security settings
The pre-selection Recommended security settings is recommended to start, in order to gain initial experience using EMET; this can be adjusted later if necessary changes arise during operation.
Also set where EMET should log its events in the ribbon bar. You should definitely leave the option for logging in the Windows Event Viewer enabled. You can use this option to collect and evaluate all events relevant to EMET centrally when using the corresponding add-on software, such as the Windows Event Collector service or the Audit Collection Services (ACS). Whether you want the option for displaying EMET events in the Windows computer's tray icon to remain active is a matter of taste and depends on whether you want to bother normal users with the task of viewing EMET events.
Next, click the Apps icon in the ribbon bar. This will open a new window for application configuration and lists all protection functions for individual processes. This way you will receive more interesting information about the protection possibilities for individual applications. At this point you can add additional applications, either by specifying the absolute name and the installation path of the application or by using a wildcard function and the corresponding application wildcards.
Next, set the default action in the ribbon bar – this is the action EMET responds with if an exploit is detected. The default is Stop on exploit and should be set to Audit only during the test phase to determine whether or not the EMET settings cause any impairments to the system and the installed applications. Once the test phase is over, change the default action back to Stop on exploit.
Protection Against Counterfeit Certificates
Another interesting function is the configuration of trusted certificates in the EMET management console. The tool checks the certification authorities used when accessing websites that are set as protected. Attackers often obtain valid certificates from another certification authority under false pretenses. These are recognized as valid by the browsers even though they do not belong to the actual site operators. An allegedly valid certificate appears if they perform a man-in-the-middle attack and redirect users to their fake site. EMET can therefore warn users if a certification body other than the one that is usually or previously defined is suddenly used.
Apart from a number of preinstalled websites such as Facebook, Yahoo, and Twitter, you can store websites by clicking the Trust icon in the Certificate Trust configuration ribbon bar in the EMET management console and entering additional websites in the Protected Websites tab.
Then, specify the Trusted Certification Authorities in the Pinning Rules tab. Click Add rule, enter a name for the new rule, and import the trusted certification authority. Generally, you should enable the PublicKey Match checkbox after the import. Certificates issued by the internal certification authority are now classified as trustworthy based on the list of Protected Websites and are thus protected against man-in-the-middle attacks.
Conclusion
The Enhanced Mitigation Experience Toolkit complements the numerous Windows security technologies for reducing the attack surface using a simple interface. It can be rolled out centrally and configured via software distribution; thus, it provides a flexible way to increase your network security. Administrators should take a close look at EMET and consider using it in their own corporate environment.
