
VM and cloud management with openQRM
Everything Under Control
Heterogeneous IT infrastructure in the data center has been on the rise for years. But, as the combinations of various technologies and platforms increase, ensuring the assured service levels for the deployed services is becoming increasingly difficult. Cloud management systems provide sophisticated tools to handle these tasks and are available as both free and enterprise variants.
In addition to classic IT infrastructure based on networks, servers, storage, virtualization, and clients, many enterprises today also rely on cloud services. In the simplest case, this just means that the web server with the enterprise website has been outsourced to a hosting service provider, or that external IT services such as spam and anti-virus have been rented as managed services. However, the pressure is increasing to provide increasing numbers of services to users with a high level of availability.
This means that internal services such as email, SharePoint, or file services are being run in external data centers, or even in Amazon, Google, Microsoft, and other clouds. It is practically inevitable that different technologies like virtualization, are then used. For example, many companies use vSphere or Hyper-V internally, whereas virtualization at Amazon is based on Xen. In other words, the more services that are outsourced, the faster administrative staff need to familiarize themselves with new technologies and the corresponding management tools.
It is precisely at this point that cloud management systems such as openQRM enter the game. OpenQRM provides a web-based, open source data center management and cloud platform with the help of which various internal and external technologies can be abstracted and grouped within a common management tool. This management system also takes care of provisioning, high availability, and monitoring of services that are offered. OpenQRM sees itself as a framework and implements an open plugin architecture. For example, an existing hypervisor such as KVM or Xen can be easily integrated as one of many possible resource providers.
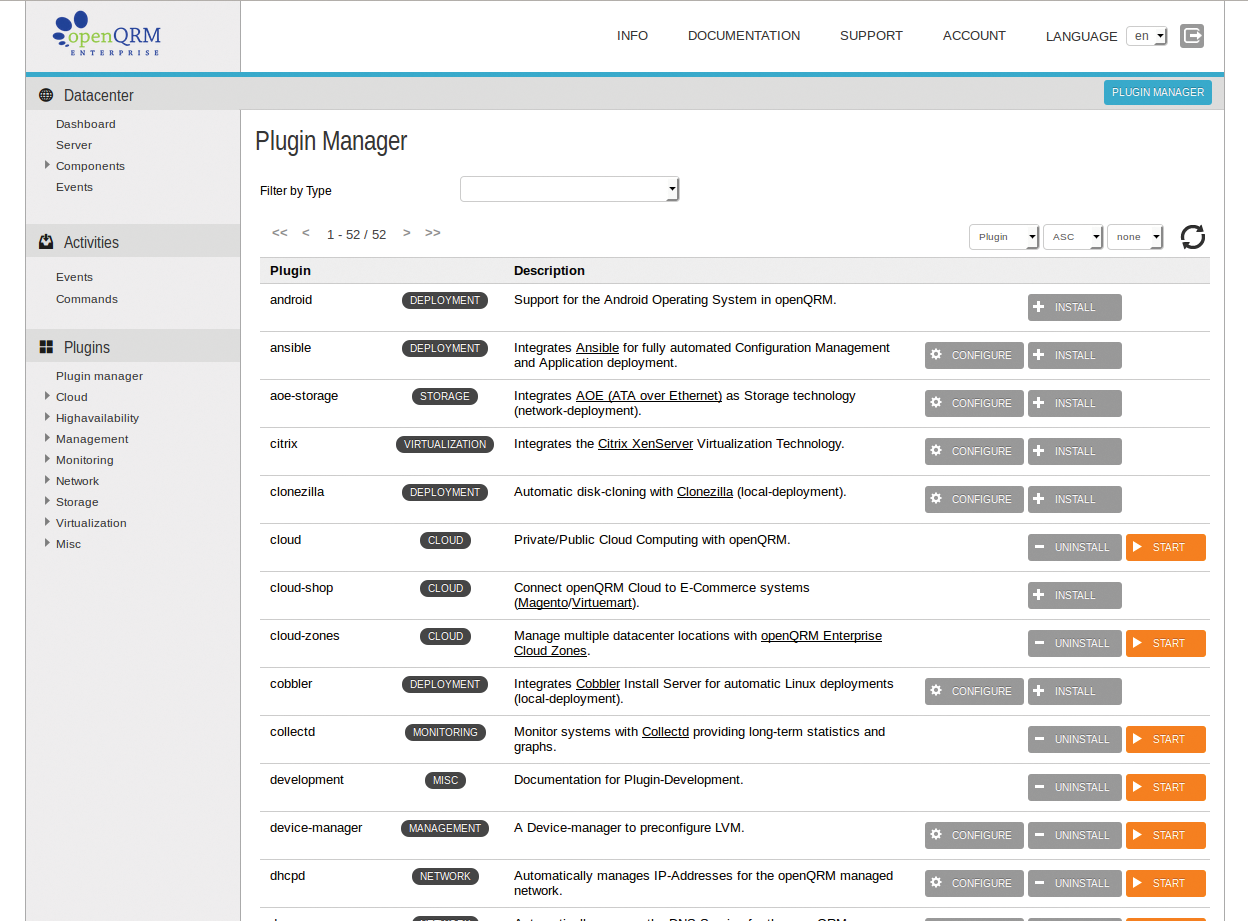
Instead of providing individual tools for individual tasks, such as configuration management and system monitoring, openQRM integrates proven open source management tools such as Nagios, Zabbix, and collectd as plugins. Thanks to this plugin architecture, the system remains open to future technologies and can even be customized by users if the need arises. The openQRM Enterprise includes some 50 plugins (Figure 1). In this article, I will be looking at the basic installation, configuration, and functionality of the openQRM Enterprise Edition.
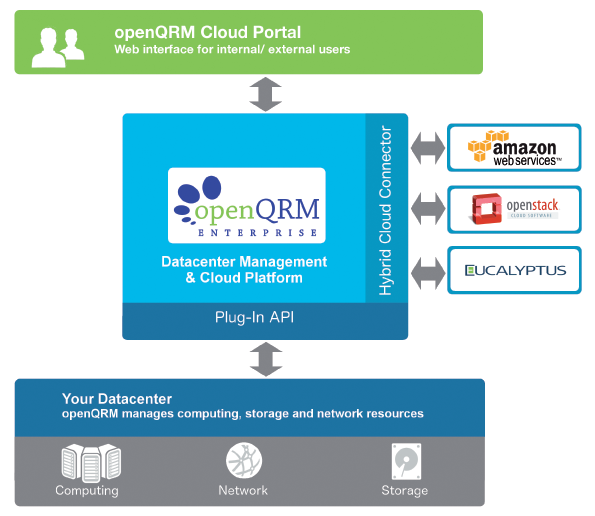
The openQRM system architecture comprises three components: the Data Center Management and Cloud Platform, the Plugin API, and the Hybrid Cloud Connector. The Data Center Management and Cloud Platform provides the basic functionality of openQRM and uses the Plugin API to communicate with the data center resources that are also installed on the local network (hypervisor, storage, and network). Fortunately, openQRM comes with support for five virtualization environments: VMware ESX, Citrix XenServer, KVM, LXC, and OpenVZ. The developers say that a plugin for VirtualBox already exists, but it is currently being modified to match the latest openQRM version.
In terms of storage, openQRM can handle LVM, iSCSI, NFS, ATA over Ethernet, SAN Boot, and Tmpfs storage. For the network configuration, openQRM integrates critical network services such as DNS, DHCP, TFTP, and Wake-on-Lan. The Network Manager included with the package helps administrators configure the network bridges required for these services.
The Hybrid Cloud Connector takes care of connecting with external data center resources, such as Amazon Web Services, Eucalyptus, or OpenStack cloud. To do so, it relies on APIs by individual manufacturers, which dock with openQRM via the plugin architecture. The openQRM cloud portal provides a web interface that internal or external users can use to compile IT resources as needed. Figure 2 shows an overview of the openQRM system architecture.
Installation and Deployment
OpenQRM's open architecture supports a variety of installation scenarios. In the simplest of all cases, openQRM only manages the local resources – that is, it takes care of managing a private cloud run on your own hardware. Thanks to the cloud connector, management can be easily extended to external resources if the need arises, thus offering management functions for public or hybrid clouds.
Via the cloud portal, openQRM can also provide these resources to end users within the context of a granular authorization system. Users can turn to the web interface to configure virtual machines and storage themselves, as needed. For billing of these resources, the cloud portal includes a simple accounting system with its own virtual cloud currency, CCU (Cloud Computing Unit). Using your connection to store systems by Magento and VirtueMart, this virtual currency can also be converted into hard cash as needed.
The system requirements depend greatly on intended use. If you only want to take a quick look at the system, you can easily install it on a virtual machine. Initial evaluations on the practical conditions are easily possible on a well-equipped PC with a quad-core CPU, 1GB of RAM, a network interface card, and 20GB of free hard disk storage. As a minimal configuration for a small production environment without high availability, openQRM says you need three physical systems: the openQRM server, a storage host, and a virtualization host.
The recommendation for a production environment with high availability would then include six (+n) physical servers (two openQRM servers, two storage hosts, and two virtualization hosts). Linux is used as the operating system for the openQRM server itself; admins can choose between Debian and Ubuntu. Both distributions come with all the required features out of the box. Alternatively, openQRM also offers official support for the enterprise versions of Red Hat, SUSE, and CentOS.
In our lab setup, I used a physical server with Debian Wheezy. While you are installing Debian, make sure to assign a static IP address and choose the following layout in manual partitioning:
- Root partition
- Swap partition
- Dedicated partition to provide storage space with virtual machines
Mark the dedicated partition in the Debian installer as "do not use"; it will be integrated into the openQRM server later on. In the software selection of the installer, only select the SSH server. Then, upgrade all packages after completing the installation and proceed to install Apache with PHP 5:
apt-get update && apt-get upgrade apt-get install apache2 libapache2-mod-php
When you are done, check whether the PHP functions for the Apache server were disabled below disable_functions in the /etc/php5/apache2/php.ini file. If so, delete them; then, restart Apache.
You can pick up an evaluation license or the full version of openQRM Enterprise [1]. Unpack the tarball on your server's root directory. After changing to the new openQRM-5.2.3-Enterprise-Edition-Eval directory created by this step, become root and initiate the installation of openQRM by typing:
./install-openqrm.sh
The installer downloads all the required components in the background and sets up a basic configuration. During the installation, you will be prompted to enter a root password for the MySQL server and the Nagios administrator. So that openQRM can send notifications by email later, you also need a working Postfix configuration, but you can install this retroactively.
Additional setup steps then occur in the openQRM GUI in your browser. You can access the Web GUI on http://IP_address/openqrm. Log in with a username and password of openqrm and confirm the network interface card that you want openQRM to use (this is typically eth0). Then, openQRM creates the required MySQL database; the root password you defined for MySQL is needed during the install.
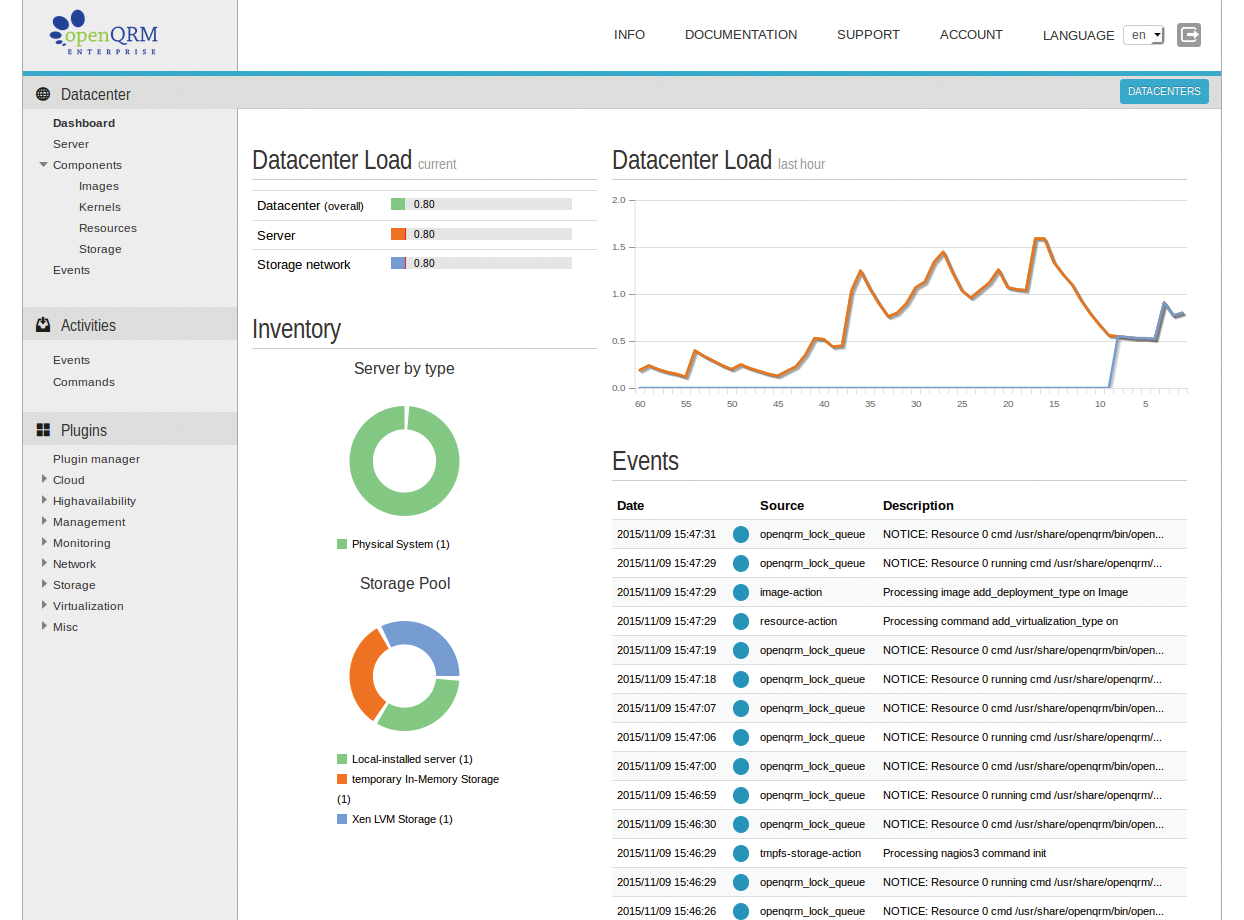
Finally, you need to upload a valid license, which consists of two parts: the public key and the actual license file. Upload the two files to your server using the corresponding buttons in the Info | Upload License Files configuration dialog. This completes the installation, and you are automatically taken to the openQRM dashboard (Figure 3).
Overview and Initial Steps
The navigation menu on the left side is used for all tasks in openQRM. The functions are divided into three main areas: Datacenter, Activities, and Plugins.
The Datacenter area is used to manage resources such as the Server, Images, and Storage. The term "server" doesn't mean a server in the traditional sense; instead, it refers to a master object or a service in the meta layer, for example, "Web Server on Linux virtualized on KVM on Host 1 with network configuration xy." Components such as Images, Kernels, Resources, and Storage are now assigned to the master object. The reason for these idiosyncratic abstractions is that subcomponents of a server on openQRM need to be replaceable at any time.
High Availability
OpenQRM defines high availability in three ways:
- High availability for the openQRM server: Because openQRM works with standard technologies (filesystem, Apache with PHP, MySQL/PostgreSQL), the high-availability system can also be set up with built-in Linux tools such as Linux-HA, Pacemaker, or Corosync.
- High availability for server objects on the openQRM server: OpenQRM provides its own plugin that lets you easily make server objects highly available at the press of a button. OpenQRM takes care of distributing the existing resources itself.
- High availability for applications: OpenQRM also supports Linux-HA, Pacemaker, and other high-availability tools at the application level. For simple configuration of highly available applications, openQRM comes with a plugin for LCMC (Linux Cluster Management Console).
Below Activities, you will find information about the operating status (Events and Commands) and activities that the openQRM server is currently running. The plugin manager (Plugins) is used to install and manage extensions for openQRM. To improve the overview, openQRM sorts the installed plugins by categories such as Cloud, Monitoring, Virtualization, and so on.
If you did not configure the SMTP server during installation, this is a good time to do so. A correctly installed SMTP server is needed for the Event Mailer plugin to send warnings, error messages, and other events to the administrator. The end-user cloud portal also relies on the local SMTP server.
Users who generate an account via the self-service portal are sent a security token by email that lets them complete the registration of their accounts. If you already have a mail groupware server on your network, simply select Internet with Smarthost in the Postfix configuration dialog (dpkg-reconfigure postfix) and enter the IP address of your internal mail server as the SMTP Relay Server.
Because openQRM defines itself as a central management instance on the network, it also provides space services such as DNS and DHCP. Of course, these services typically already exist on a network (e.g., via Active Directory). You just need to be careful when you commission an openQRM server. To avoid the risk of having active DHCP servers on your network that independently assign IP addresses on the same subnet, you might want to assign the openQRM server its own VLAN or subnet.
Once you meet these preconditions, fire up your editor and modify the domain name OPENQRM_SERVER_DOMAIN="oqnet.org" in the file /usr/share/openqrm/plugins/dns/etc/openqrm-plugin-dns.conf and install or launch the DHCP daemon, DNS, and Tftpd plugins. By default, the openQRM DHCP server assigns a complete IP range of the local subnet. You can easily change this by modifying the range in the /usr/share/openqrm/plugins/dhcpd/etc/dhcpd.conf file. In combination with the DHCP server, openQRM also provides a PXE/TFTP environment for booting over the network. For this reason, it also makes sense to install the Tftpd plugin via the plugin manager
Virtualization with KVM
OpenQRM already comes with a very powerful hypervisor in the form of KVM, on the basis of which I will now be provisioning a couple of virtual machines as examples. Please note that if you are running Windows on a virtual machine on KVM, you need to enable the Intel VT/VT-x CPU extensions in the BIOS. If this has not already happened, fire up the plugin manager again and install the following plugins: dns, dhcpd, tftpd, network-manager, local-server, device-manager, novnc, sshterm, linuxcoe, kvm.
The plugins have mutual dependencies in part; therefore, you need to watch out for small yellow pop-ups during installation. These pop-ups are very subtle reminders of unresolved dependencies in the dashboard. To resolve these, simply install the desired plugins in the specified sequence.
Setting up a Network Bridge
For openQRM to be able to add virtual machines and other internal and external resources to its network management scope (DNS/DHCP) later on, you need to set up a network bridge on the host system's network interface card. To do so, click on Edit for the openQRM server object and change to Plugins option Network | Network Manager and click Add new network bridge.
In the dialog that appears, you need to assign a Name for the new bridge (br0) and enter the static IP that you assigned to the physical server during the installation below IP (here, this is 192.168.0.30 on the interface eth0). Fill out the Subnet (255.255.255.0) and Gateway (192.168.0.254) fields appropriately. In the background, openQRM sets up the new network bridge and installs Debian packages required for this purpose.
If the system seems to freeze when setting up the network bridge, this may be because name resolution is not working correctly on the server. In this case, check that the /usr/share/openqrm/plugins/dhcpd/etc/dhcpd.conf file Standard configuration directives option domain-name-servers 192.168.0.253 192.168.0.254 has the correct name server entry or entries and change the settings if needed.
You can also prevent openQRM from autonomously modifying name resolution on your system by setting
OPENQRM_SERVER_ADJUST_RESOLV_CONF="no"
in the /usr/share/enqrm/plugins/dns/etc/openqrm-plugin-dns.conf file.
LVM Storage for VMs
Compared with Blockfile Storage, using KVM LVM Storage offers greater flexibility (snapshots, cloning). I will thus be assigning the partition prepared during the installation of Debian (but not previously assigned) as LVM storage for the virtual machines. Each VM will then later have its own logical drive from the LVM storage pool.
When it comes to enabling the KVM LVM storage, openQRM again handles the configuration of the required Debian LVM packages in the background. Click on the Manage button for Storage | KVM LVM Storage and then select Add new volume group. Select the partition you want to assign from the drop-down menu (e.g., /dev/sda3), type a name (e.g., kvmg) and confirm with Submit.
The next step is to set up a virtual machine in KVM. The installation is like other virtualization systems after creating the virtual machine: You need an installation medium with the operating system – typically an ISO image. Then, mount this image as the primary boot medium before you start the virtual machine; the installation will start directly from this virtual CD drive.
Note that openQRM has a plugin for LinuxCOE (Linux Common Operating Environment) [2]. LinuxCOE is an open source tool by HP that generates ISO images for CentOS, Debian/Ubuntu, Fedora, and many other Linux distributions. The special thing here is that the tool also supports these distributions' automatic installers. In other words, you can easily create installation ISOs that run automatically. To discover how to use LinuxCOE with openQRM, check out the exhaustive tutorial on the openQRM website [3]. If you prefer not to work with the COE plugin, then copy an ISO image of your Linux distribution choice to a directory on the openQRM server.
Creating the Server Host Object
Next, go to Server | Add Server and create a new server object. To make sure that the new object matches the openQRM naming conventions, press the Generate name button and assign a meaningful description in the comment box. Apply the default openQRM Server (Physical system) in the next window, and then press Submit. In the list with the server overview, edit the server object you just created by selecting KVM Host as the virtualization type in the drop-down. Finally, apply the settings by pressing Submit.
The virtual machine also needs a server object. Create it as previously with Server | Add Server. In the window that follows, select New Resource and assign KVM (localboot) Virtual Machine as the type. You are automatically taken to the KVM host server selection. When you get there, click on VMs and select Add local VM to add a new virtual machine. Set the desired parameters, such as the number of CPUs and memory, and make sure that the first network adapter (Network_0) is connected with the network bridge (br0).
In the Boot from section, select ISO, press the Browse button, and navigate to the directory in which you stored the ISO image previously (this is /root in this example). Assign a VNC password, which you will use later to access the virtual machine via noVNC and to initiate the operating system installation. Then, complete this step again with Submit. What is slightly confusing is that you end up back in the wizard again, so you will need to press Submit yet again to confirm the resource you just created.
Creating an Image and a Logical Drive
Once you have also completed this step, the wizard shows you a New Image button. When openQRM refers to an image, it means a logical object that will be mapped to physical storage later on. Click on New Image | LVM deployment for KVM and select LVM in the KVM host selection. The kvmg volume group, which you created as LVM storage earlier, now appears (Figure 4).
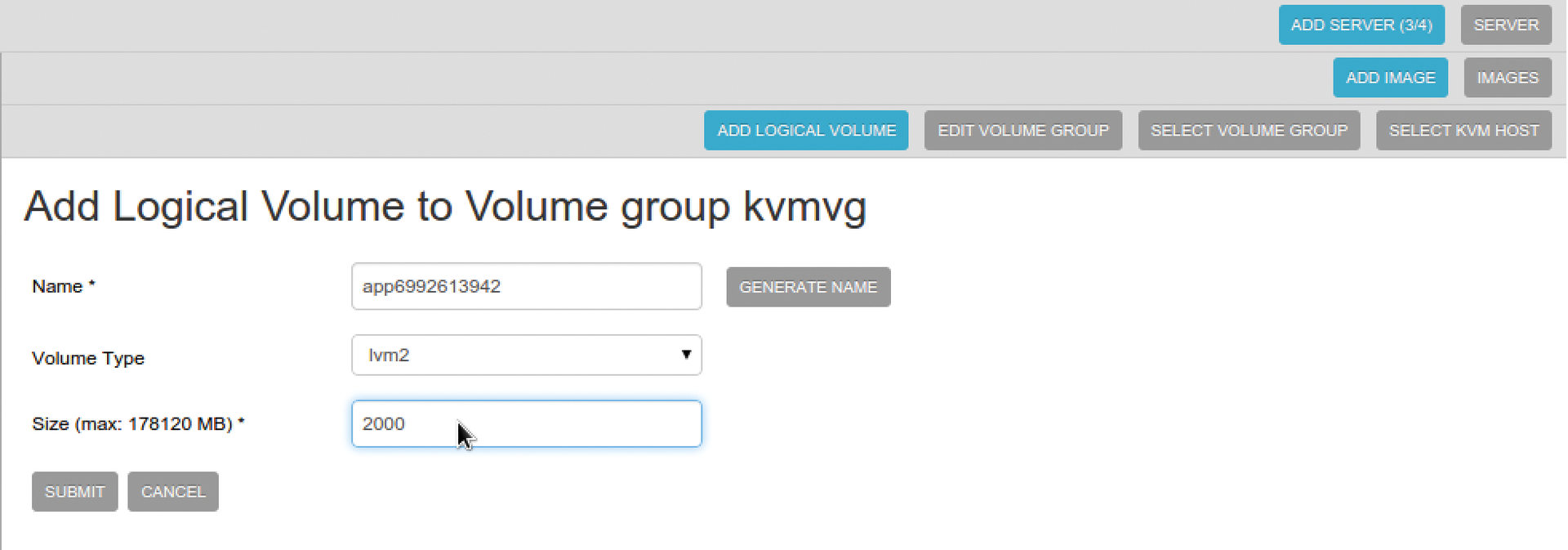
You can press Select | Add new logical volume to add new logical volume. Define the logical volume's size in megabytes and complete the remaining settings. Then, press Submit to open the image in edit mode. Now define the operating system type (Windows, Linux, or Other). In the case of an automatic installation with LinuxCOE, you could also give the installer the root password here; of course, you do not need this step in a manual installation scenario. Submit takes you back to the list of servers with your new virtual machine at the bottom. Pressing Start now fires up the virtual machine.
Installing the Operating System
You are now ready to install the operating system on the virtual machine. When it started up, the virtual machine booted the installation ISO image; it is now waiting for keyboard input. To continue the installation, use the Novnc button to access a virtual machine; you need the VNC password that you defined previously for this. If everything worked out, you should see the Debian installer start screen and be able to complete the installation of the operating system in the normal way.
After completing the installation of the new operating system on the VM, you need to remove the ISO image as the boot medium and set the virtual machine to local boot. To do this, open the server overview in the dashboard and pause the server you just set up by pressing Stop. Open the overview of your virtual machines with the plugin manager Virtualization | KVM | Hosts dialog; you will see the virtual machine assigned to the server object with a current status of Idle. Pressing Update takes you back to the settings dialog for the virtual machine, where you can change the boot order from ISO to Local. The next time it starts, the server will boot from its local boot medium.
Integrating Local VMs into System Management
Finally, you will now want to install the openQRM client on the new virtual machine. It provides an interface between the operating system on the virtual machine and the openQRM host server. This gives you an easy approach for integrating local virtual machines into your openQRM system management – and thus, for example, enabling monitoring of a virtual machine with Nagios, configuration management with Puppet, or shell access to the virtual machine using SSH. Download the openQRM client from the Plugins Misc | local-server | Local VMs and copy it to the virtual machine:
scp openqrm-local-vm-client root@IP-der-VM:/root
To install the client, use SSH to log on to the virtual machine; change to the /root directory, and make the client executable:
chmod +x openqrm-local-vm-client
You can then start the installation by typing:
./openqrm-local-vm-client
Missing packages are automatically downloaded and installed in the background. After completing the client installation, you can then use SSH Term (Secure Shell in the browser window) to access your Linux virtual machines or add virtual machines to system management with Nagios. To do so, click on the corresponding buttons with the plus signs in the server list on the dashboard.
Note that you can use the same approach to add physical or virtual (Linux) servers that already exist on the network to your openQRM management. They then appear as new resources on the dashboard and can be used, for example, as additional storage servers.
To do this, copy the client below /usr/share/openqrm/plugins/local-server/bin/openqrm-local-server to the existing Linux host and run:
scp /usr/share/openqrm/plugins/ local-server/bin/openqrm-local-server root@VM:/tmp ssh VM /tmp/openqrm-local-server integrate -u openqrm -p openqrm -q 192.168.0.30 -i eth0 [-s http/https]
The IP address 192.168.0.30 belongs to the openQRM server in this example.
Virtualizing Windows with KVM
Of course, you can install Windows on a virtual KVM machine. To do so, you need to enable the virtualization extensions (VT-X) on the physical openQRM host. If you applied the default setting of virtio when creating a virtual machine, Windows also needs additional drivers for the VirtIO SCSI controller before it can identify a local disk during the installation.
The driver, along with the driver for the VirtIO Ethernet adapter (also necessary), is available from a driver collection belonging to the Fedora project. Download the latest ISO of the collection [4] and mount it in your virtual machine's configuration as a second CD-ROM drive. The Windows virtual machine will then boot from the first CD-ROM drive, and you can load the drivers from the second when prompted to do so by Windows Setup.
Once Windows is installed on the virtual machine, you will definitely want to install the openQRM Enterprise Windows plugin, which gives you the tools required to prepare the Windows operating system for cloning and snapshots in openQRM. These Windows master images, created with Sysprep, can then be cloned multiple times and used for cloud deployments, for example.
After installing the Windows plugins via the plugin manager, you will see that the openqrm-client.exe client is available for downloading below the Plugins Deployment | Windows option. The easiest approach is to run the openQRM web interface with the browser on a virtual Windows machine. To do this, again use the noVNC plugin to access a virtual machine. Save the client in the top-level directory, C:\, and call the group policy editor, gpedit.msc.
In the editor, now add the openqrm-client.exe file as a start script: Local computer policies | Computer configuration | Software settings | Windows settings | Scripts (Start/Shutdown) | Start. As the start parameter, again enter the IP address of the openQRM server.
Sysprep and Generalized Images
To be able to provide the Windows image you created automatically to other virtual machines later on, now launch sysprep.exe and create another generalized Windows image. To do this, download the unattend.xml configuration file from tht Plugins Deployment | Windows option onto the administrator desktop and enter a complex password in the Administrator keyword | Value section. This password will be the administrator password for the automatic Windows installation later on.
Before you launch Sysprep, it is a good idea to defrag the virtual machine's hard disk first. It can use the built-in Windows tool defrag.exe to do so; after completing defragmentation, open a Windows command shell with administrative rights and run the following in the shell:
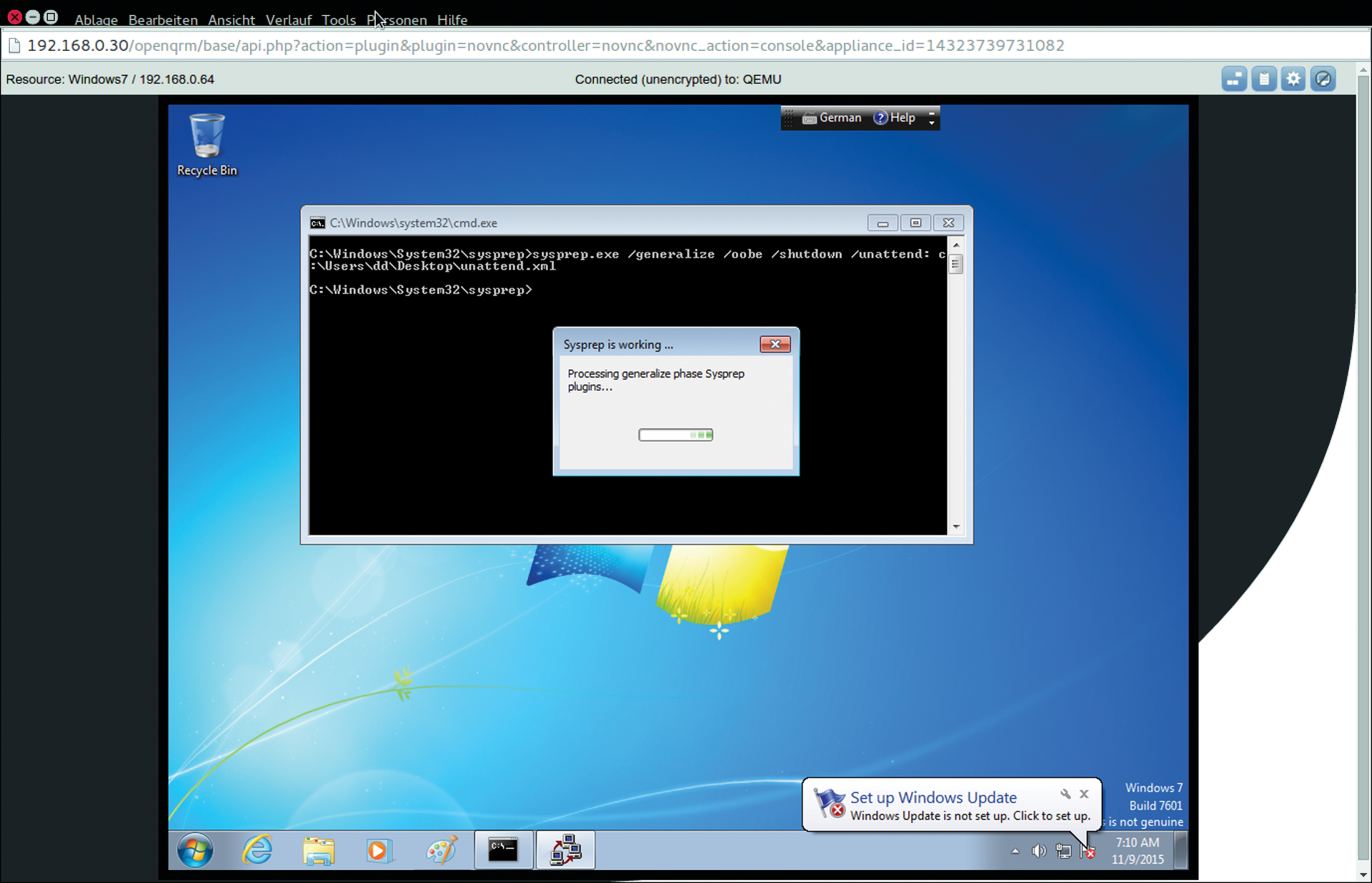
C:\Windows\System32\sysprep\sysprep.exe /generalize /oobe /shutdown /unattend:C:\Users\Administrator\Desktop\unattend.xml
After completing the Sysprep action, the Windows system shuts down, and the Windows image is ready for cloning, or the snapshot is ready for further cloud deployments (Figure 5).
Setting Up a Cloud Front End
The openQRM cloud plugin provides a fully automated server provisioning workflow with its own web portal. External users can register with this portal in a self-service action, or they can be added manually by the administrator. Depending on their group assignments, users can then submit cloud orders. Depending on the configuration, these orders can be manually or automatically released – openQRM autonomously takes care of the complete provisioning workflow.
The process of setting up a cloud front end is described in a how-to online [5]. The basic setup of the service is handled in the plugin manager below Cloud | Configuration | Main Config. You need to configure at least the following settings:
cloud_admin_email - openQRM administrator's email address auto_provision - true show_private_image - true
You can optionally modify the following parameters at this point:
-
external_portal_url: Enter an external DNS/domain name for the cloud portal. -
cloud_currency: Choose whether to show the cloud currency for the users in US dollars or euros. -
cloud_1000_ccus: IMAP the virtual cloud currency, CCU, to hard cash. -
vm_loadbalance_algorithm: Load-balancing algorithm for virtual machines; for example,0= Load,1= Memory,2= Random,3= first available host until the virtual machine limit is reached.
In the course of the configuration, you then create the cloud products, which users can later book with their access credentials, and define the user groups, prices, and billing mode for resources booked via the cloud portal. End users can reach the cloud portal on http://server_ IP_address/cloud-portal/.
Backing Up and Restoring
"Keep it simple" is the way to go for backing up and restoring an openQRM environment. Because an openQRM installation only consists of files in the database; all you need to do is back up these two components for the worst case. Basically, that just means copying all the files below /usr/share/openqrm, along with a dump of the MySQL database from openQRM to a safe place. You can do this as root with the following commands:
cp -aR /usr/share/openqrm /usr/share/openqrm-5.2.before-update mysqldump openqrm -p > /usr/share/openqrm-5.2.before-update/openqrm-db-5.2.sql
You are interactively prompted for the root password for the database for the MySQL dump. Restoring just means moving the original directory and copying the backup files and database dump that you created previously back to the original location before restarting the openQRM services.
That said, the state-backup feature gives you an even easier approach; it automatically backs up all of the configuration files and the database content with a single command:
/usr/share/openqrm/bin/openqrm state backup -n 5.2.before-update
The following command lists all backups created in this way:
/usr/share/openqrm/bin/openqrm state list 5.2.3.before-update-05-06-15_09.14.20 Test-State-Backup-05-24-15_13.09.05
To restore the system configuration from the Test-State-Backup-05-24-15_13.09.05, you would just enter the command shown in Listing 1.
Listing 1: Restore System Configuration
/usr/share/openqrm/bin/openqrm state restore -n Test-State-Backup-05-24-15_13.09.05 openQRM-server: Restoring server state from /var/spool/openqrm-state/Test-State-Backup-05-24-15_13.09.05.tgz Restoring the openQRM-database from /usr/share/openqrm/database.sql
Licensing and Prices
The openQRM Enterprise Edition license is based on a perpetual model; in other words, you can still continue to use licenses after your maintenance agreement has expired. A server license always comprises a license for the openQRM host and client licenses for managing one client each (=physical hosts). The price includes maintenance (updates and bugfixes) and support for 12 months. Client licenses for integrating further hosts can be purchased at any time.
The following editions of openQRM Enterprise are currently offered:
- SMB Edition Datacenter and IaaS MultiCloud 5.2, for small to medium-sized enterprises with one or multiple system administrators, EUR2,000.
- Large Edition Datacenter and IaaS MultiCloud 5.2, for organizations with a team of system administrators, including centralized user management (LDAP/AD), EUR4,000.
- Enterprise Edition Datacenter and IaaS MultiCloud 5.2, for enterprises with one or multiple data centers, a team of system administrators and connections to e-commerce platforms, including centralized user management (LDAP/AD), EUR7,000.
In some areas, openQRM additionally offers a hardware bundle with preinstalled SuperMicro hardware and installation support. Check out the website [6] for details.
Opening a Connection to the Amazon Public Cloud
The Amazon Web Services (AWS) consist of services, for example, virtual servers (EC2), storage (S3), and networking (CloudFront, VPC), which are managed in a web interface and billed on the basis of usage per hour or per resource. In addition to the AWS web front end, a programming interface lets administrators manage the AWS services at the command line.
The openQRM Hybrid Cloud plugin can integrate and manage an existing AWS account via this interface. The openQRM website [7] again offers an exhaustive how-to for this scenario; I will thus give a brief overview of the basic, required steps.
After installing the Hybrid Cloud plugin, you first need to install the current API and AMI tools on the openQRM server. To do so, log in to the openQRM server as root and run the commands shown in Listing 2.
Listing 2: Install API and AMI Tools
wget s3.amazonaws.com/ec2-downloads/ec2-api-tools.zipwget s3.amazonaws.com/ec2-downloads/ec2-ami-tools.zip unzip ec2-api-tools.zip unzip ec2-ami-tools.zip mkdir /usr/local/ec2 cp -r ec2-ami-tools-1.5.7/* /usr/local/ec2/ cp -r ec2-api-tools-1.7.3.2/* /usr/local/ec2/ apt-get update && apt-get install default-jdk
You might have different version numbers, but the numbers shown in the listing were up to date when this issue went to press. Incidentally, you will find a link to the download of the AMI/API tools in the Plugins section Cloud | Hybrid-Cloud | About | Plugin Type. The link specified there also takes you to comprehensive documentation for the tools. Add both of these programs to your system path by adding the following environmental variable to your /etc/profile:
export EC2_HOME=/usr/local/ec2 export PATH=$PATH:$EC2_HOME/bin export JAVA_HOME=/usr
To enable the environmental variables, log off and back on. Then, type
service openqrm restart
to restart the openQRM services.
It is a good idea to create a separate user account for openQRM in the IAM section of your AWS account. Then, run the following at the command line to test whether the connection to AWS is working:
ec2-describe-regions -O AWS-Access-Key -W AWS-Secret-Key
Instead of the placeholders, enter your AWS access key and secret key. The results should look something like this:
REGION eu-central-1 ec2.eu-central-1.amazonaws.com REGION sa-east-1 ec2.sa-east-1.amazonaws.com REGION ap-northeast-1 ec2.ap-northeast-1.amazonaws.com ...
You are now ready to start creating and managing instances in the Amazon Cloud.
Conclusions
To get an openQRM project up and running within a reasonable period of time, administrators either need to have a solid background in system architecture and open source tools or contact the manufacturer for professional support in their planning, installation, and configuration steps. The control logic behind openQRM is not entirely intuitive (as is the case with most cloud management systems). Missing or obsolete documentation adds obstacles to the learning process.
Administrators with experience in open source and Linux will enjoy openQRM, however. Thanks to the open, plugin-based system architecture, openQRM provides many well-known and popular system tools from the Linux world without requiring any major configuration overhead. Additionally, the manufacturer offers a reasonably priced licensing model, backed up by competent support.
