
Freeing your data from ransomware
Get Yours
One of the latest trends among cyber criminals is to encrypt files on a network, forcing the user to pay a ransom for the decryption of their data. Of course, criminals use cryptocurrencies such as Bitcoins, not your typical bank transfers. The attackers achieve their objectives via many routes. For example, a potential victim might be prepared to pay money for files because they have a certain emotional or economic value. An attacker will not be interested in why the owner wants to restore their files – as long as they are prepared to pay money for the decryption.
Based on current research, TeslaCrypt ransomware (which is also known as AlphaCrypt) seems to be backed by a fairly established team. Some years ago, CryptoLocker became famous for blackmailing its way to a $3 million fortune. TeslaCrypt is just one variant of many in the field of ransomware, including larger and more lucrative tools such as CryptoLocker, CryptoWall, and CryptoWall 2 and 3. The CryptoWall variants in particular are developing increasingly complex techniques to protect themselves against deletion or against decryption of the ransomed data.
TeslaCrypt Approach
In February 2015, the first successful attacks by TeslaCrypt were reported against both private users and large-scale enterprises, although it is unclear whether the enterprises were targeted actively. At first sight, the attacks seemed to be similar to those by CryptoLocker. Once TeslaCrypt infested a system, it performed a targeted search for photo and video files, as well as gaming files, including high score and activation keys for Valve's Steam gaming platform. This particular malware tool typically uses email attachments to invade a system or forwards the victim to a rogue website where their system is then infected. An exploit kit stored on the site then uses a Flash vulnerability (CVE-2015-0311) to run TeslaCrypt on the system.
A check is performed to see whether the URLReader2 COM interface has been installed correctly in the DirectShow Filter Graph List [1]. The malicious code files are then unpacked and executed after this check. The process launches autonomously, escalates its privileges, and copies the malicious files to a randomly chosen name in the user's home directory. A new process then launches, and the existing process is migrated to this process. Then, the original process is terminated and the original unpacked files are deleted. Now the new process runs the malicious code routines with escalated privileges and launches a window that is visible to the user with a prompt to pay up (Figure 1).
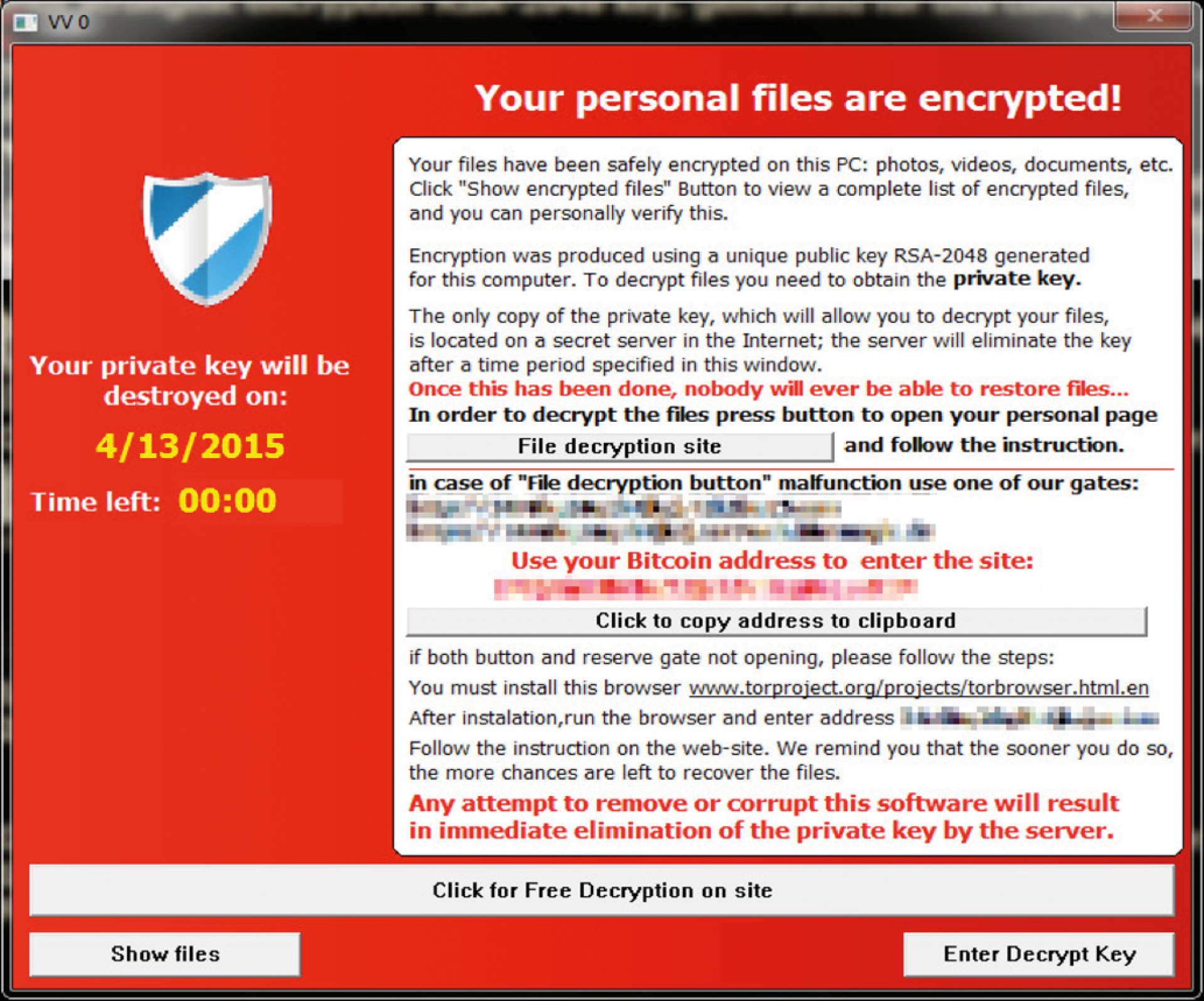
Before the encryption process is run on the system, the following routines are run by the malware tool with the aid of five new process threads:
- Delete all Windows shadow copies
- Create and encrypt the key file (
key.dat) - Transfer the key file to the command and control server
- Implement a defense function every 200msec that prevents calls to the following processes, or keeps them from running:
taskmgr,procexp,regedit,msconfig, andcmd.exe.
The user will be unable to launch other processes besides those listed at this point, because TeslaCrypt remembers the name of all processes launched on the system.
Solid AES Encryption
TeslaCrypt's main function is to encrypt the files that exist on the infected system. It is frightening to see that more than 170 million file types are potential encryption candidates. After TeslaCrypt has completed the init routine and deleted the Windows shadow copies, the key file key.dat is created, which contains all the encryption keys: primarily the payment key and the master encryption key. These keys are combined to encrypt files using a proprietary algorithm.
Other versions of TeslaCrypt create a third key known as the recovery key, which simply serves the purpose of allowing the victim to upload the file to a website before paying if no other actions are possible after infection with TeslaCrypt. This step is necessary because encryption differs from system to system. The file containing the recovery key is uploaded to a site on the deep web (a non-indexed part of the Internet). The typical payment method for this kind of site is the Bitcoin Internet currency. This means that the victim is forced to buy Bitcoins and then send them to the stated Bitcoin address. The keys are generated by reference to the following system information:
- Global LAN network statistic of the infected system
- 64 bytes generated randomly by the Windows cryptography function
- All descriptions of the active processes
- All modules loaded in each process
- The physical memory information of the infected system
Once all the data has been gathered, a very large array with many SHA1 hashes is generated. Each hash contains the first 20 bytes of the collected data. Then a global SHA1 hash is formed from all the arrays and stored temporarily. With the help of the globally generated SHA1, the master key and payment key are generated using a proprietary algorithm and SHA256 and written to the key.dat file. Each key has a length of 32 bytes (256 bits).
Encryption of the individual files occurs in a separate process. The routine goes through the following steps:
- Lists all the files that are candidates for encryption
- Generates a 16-byte initialization vector for AES
- Reads the target files
- Initializes the AES encryption algorithm
- Encrypts the target files with the help of a 256-bit AES CBC algorithm
Once this process is complete, all candidate files are encrypted with the stated algorithm. The user now has no chance of decrypting without a key. It is important to note that the user only has a certain time window in which to decrypt their data. If the user does not decrypt within a certain time, the key deposited on the C&C server is deleted.
By the way, the pop-up that prompts the user to decrypt shows misleading information. It claims to use RSA-2048 for the encryption, which, as you might know, is asymmetric encryption and would mean that it is impossible to decrypt the data without a backwards compatible private key.
As this article and other sources have stated, TeslaCrypt only uses symmetrical AES encryption. Of course, the matching key is required to decrypt the files because AES-256 has so far not been compromised.
Protections Against Infection
Full protection against this kind of malware is not possible. The attack and infection patterns can be fairly easily changed by the programmers so that signature and heuristic data required for detecting the malware by antivirus tools might be useless. Nevertheless, the following safeguards are meaningful to prevent infection by variants:
- Operate the system without permanent administrative privileges
- Patch software (in particular browser plugins) and the operating system with the latest updates
- Get the latest malware definitions
- Activate the local firewall
- Block known command and control target addresses to prevent communication with control servers
- Create valid and independent backups
These measures cannot completely prevent an infection.
Decrypting the Files
First, we can only advise you not to accept the blackmailer's offer by paying a ransom. Transferring the money just encourages cyber criminals to increase the sum requested. Second, it is unclear whether you will ever receive a working key after paying. Security vendors have repeatedly offered special decryption tools that are capable of restoring the encrypted files – if you don't have a recent backup.
In the case of TeslaCrypt, the Cisco Talos group has created the option of decrypting the files without paying. The tool required for this, Talos TeslaCrypt Decryption tool [2], can decrypt by using the generated key.dat file. This file typically resides below the user data directory on the system (user Application Data directory in Windows), but you should only run the command-line tool after first backing up all the encrypted files. Some data loss is possible if the files cannot be correctly decrypted. Use and deployment of this program is at your own risk. The parameters in Table 1 can be used with the command-line tool.
Tabelle 1: Parameters for Talos Tool
|
Parameter |
Action |
|---|---|
|
|
Manually specifies the master key for decryption |
|
|
Specifies the path to |
|
|
Decrypts a file |
|
|
Decrypts all ECC files in the target folder |
|
|
Decrypts all ECC files on the target system |
|
|
Keeps all original encrypted files |
|
|
Automatically terminates and deletes the TeslaCrypt malware |
Conclusions
A number of variants of the TeslaCrypt ransomware are currently invading the malware markets. In fact, just before this magazine went to print, TeslaCrypt 4, which uses RSA-4096 for data encryption, was discovered. This variant was impervious to known decoding tools at the time, which makes suitable measures all the more important. Keeping current with patches and malware signatures for both the operating system and all third-party applications are part of your mandatory defenses.
If worse comes to worse, do not pay, but try to restore your files using decryption tools. Better still: Restore the current backups on a system that you set up from scratch.
