
Halting the ransomware blackmail wave
Ransomware Storm
Since February, there have been continuous waves of Locky infection. Windows users are attacked by drive-by downloads or email attachments. After infection, the malicious program encrypts individual files or even the entire hard disk, and demands an anonymous Bitcoin ransom payment from its victims. Locky, an encryption trojan, has found many victims, including well-known corporations and institutions. The trojan changes almost weekly and is known under the following names:
- Ransom: Win32/Locky.A:
- TrojanDownloader: O97M/Bartallex
- TrojanDownloader: BAT/Locky.A
- TrojanDownloader: JS/Locky.A
Encrypt and Blackmail
The name "Locky" already suggests its function. The ransomware encrypts files on the affected computer, on network drives, and even in the cloud, thanks to synchronization. These data can only be restored if you have the decryption key or have made copies of the files on an external, non-affected storage medium. Locky searches specifically for audio files, documents, movies, images, databases, and archive files. Once the trojan has found these files, it encrypts them using the Advanced Encryption Standard (AES). In addition, the malware deletes volume shadow copies, which could be used to recover the encrypted files.
Once the encryption process is complete, Locky stores a ransom demand and also sets up a desktop background with a ransom demand. It requires the victim to pay a ransom of 0.5 to 1 bitcoins (about EUR200-400/$217-434) to the cybercriminals. In return, the victim receives the private key for decrypting the files.
This blackmail trojan is currently spreading rapidly throughout Germany, according to some security researchers, with up to 5,000 new infections per hour. The Netherlands and the United States follow in the ranking at some distance. Locky is mainly spread by email. A fictitious invoice serves as the infection channel. Apparently, the malware developers have succeeded in making users believe that the email contains a genuine bill. Parallel to this, harmless-looking but infected websites serve as the distribution channel via "Drive-by Download." Exploit kits, such as Neutrino, are used for this purpose. They use a wide range of security vulnerabilities in the browser and plugins to inject malware into the computer. To fend off such attacks, users are forced to maintain their systems at the latest patch level.
Symptoms of Infection
A message (Figure 1) is the most noticeable symptom of infection with Locky (and with other ransomware). Additionally, files and data on network drives and in cloud storage are encrypted and therefore unreadable. Locky also attacks disconnected network drives if they are still accessible – a novelty. In the case of an infection, the following files (or similar files) appear on the system:
_Locky_recover_instructions.txt _Locky_recover_instructions.bmp %temp%\svchost.exe (Locky ransomware) [ID][identifier].locky (encrypted files)
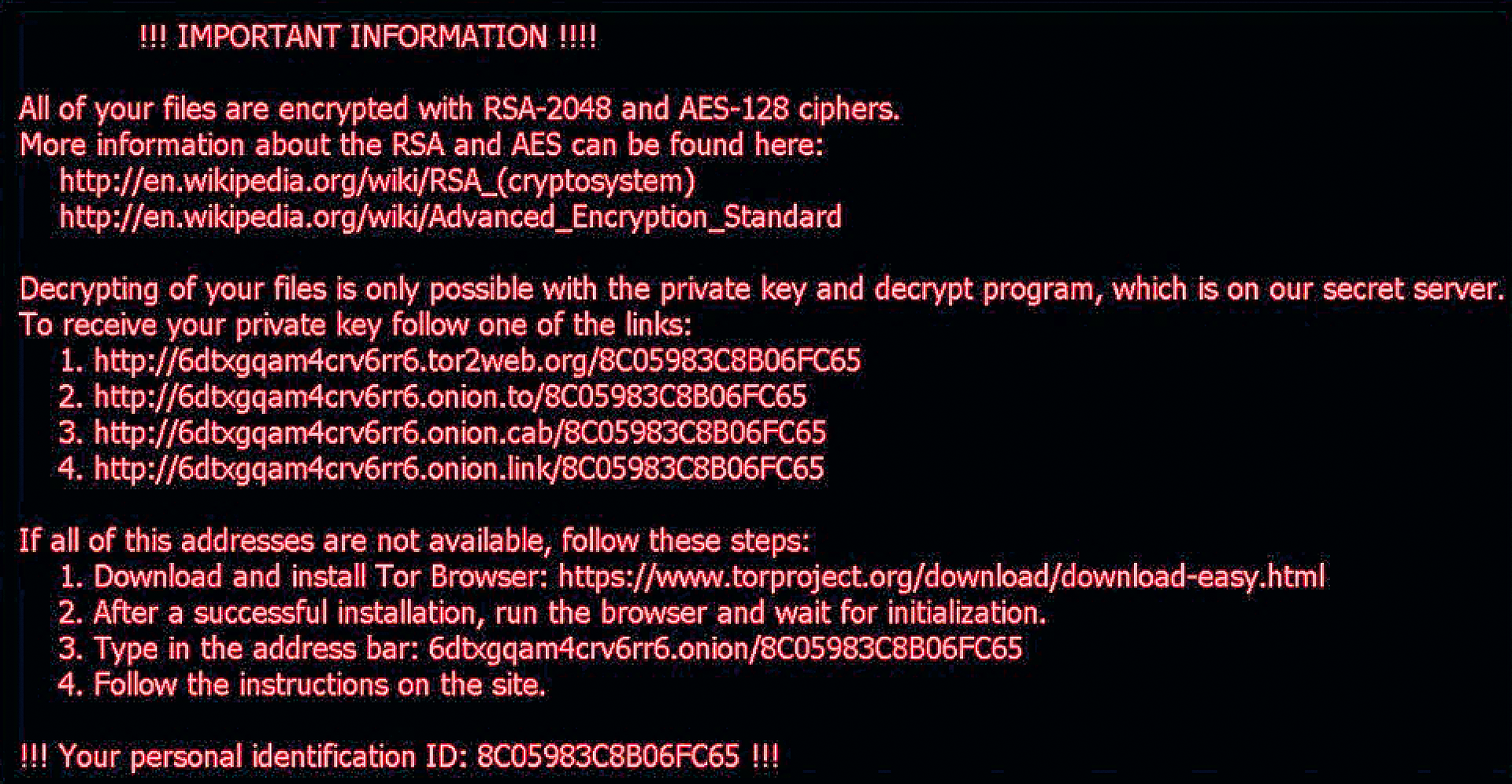
The malware also attempts to contact the following internet addresses:
http://vjwmpxseu.fr/main.php http://jywdohhfkypg.de/main.php http://blydeylrayu.it/main.php http://obvpxgcohmpsou.it/main.php http://cqvgwp.uk/main.php http://tdxgp.eu/main.php http://109.234.38.35/main.php
Finally, several changes in the registry are identifiable under the HKEY_CURRENT_ USER\Software\Locky key.
Camouflage: Batch Files and Fax Messages
Hardly a week passes without new Locky variants making an appearance. The motivation for this is clear: Constant change and development significantly complicates detection by antivirus programs. Typically, manufacturers need about 12 hours to respond to known malicious code to adjust their signatures – in this period, very few protection programs detect the new ransomware.
To avoid detection, the cybercriminals recently used batch files and the Windows Script Host cscript.exe to download and execute the crypto trojan. Apparently, this variant was very successful. Spam fax messages are another creative form of attack. At first glance, the matching and deceptively realistic fax by VoIP provider sipgate attempts to deceive the user and motivate them to open the document (sipgate has already warned users about this variant on its own site). The subject of the email ("New fax from 034205-99 …"), and the realistic details in the email text entice the user to open a ZIP file attachment.
Better Prevention
Should you fall victim to the encryption trojan, it is not a good idea to follow the ransom demand. Instead, you should back up the evidence and file a legal complaint. In addition, it is recommended that you back up the encrypted files, which you may be able to decrypt some time later if security vendors find a cure.
In general, a comprehensive IT security strategy is advisable. Start with effective hardening measures through widespread adherence to the principle of minimal privileges. In addition, a restrictive firewall configuration prevents potential communication between the ransomware and the C2 server. Ideally, you will want to use security systems on the gateway that also analyze incoming files based on their behavior, and thus detect malware regardless of signatures.
Of course, you should keep your computer systems updated with the latest patches. In conjunction with an up-to-date virus protection solution and regular scans, this reduces the risks significantly. In addition, tell your users to avoid opening any email attachments from unknown senders. The same applies to links in emails. If you use Microsoft Office products, make sure to disable the automatic execution of embedded macros. Macros should be enabled only for documents in trusted locations if you absolutely rely on using them.
Of course, there is always a residual risk, so back up your data periodically using different generations. A good, reliable, and tested backup strategy is a must-have, and not only in this scenario. Of course, the backup media must not be permanently connected to your computer. Otherwise, the backed-up data is also useless in the event of an infection.
New Tool Against Ransomware
The anti-malware vendor Malwarebytes has published a free tool, Anti-Ransomware [1], to explicitly protect users against ransomware. The tool is currently in beta, but has been successful in various tests. It analyzes the behavior of programs and blocks their execution before disk encryption takes place. Among others, the software helps combat the ransomware variants Locky, CryptoWall4, CryptoLocker, TeslaCrypt, and CTB-Locker.
Conclusion
The year 2016 started off early with the first big ransomware blackmail wave. Attackers are taking increasingly sophisticated approaches, and malicious emails are very difficult to distinguish from bona fide communication. They even use legitimate, existing companies including email signatures as the sender. Comprehensive protective measures are therefore more important than ever.
