VMware AirWatch mobile device management
Mastery of the Airwaves
Mobile devices are an indispensable part of business, even though some administrators might wish they were gone. VMware AirWatch [1] looks to introduce order to the device zoo. In the lab, the software mastered this challenge with flying colors.
The implementation of an extensive mobile security solution is not an easy task. Different mobile platforms and the constant mix of consumer and business use coincide with an overall increase in the number of smart devices. In this environment, it is important to protect commercial data against unauthorized access. AirWatch mobile device management (MDM) lets administrators manage various mobile devices centrally. Operations are essentially from a centralized, browser-based management console based on HTML5, where IT professionals can configure mobile devices remotely, update apps and operating systems, and check security settings. AirWatch itself runs on a Windows server system.
Multiple Servers
For test purposes, you can install all the components on a single server. Usually, however, you will have a setup with at least one server in the DMZ that client systems address over the Internet and a management server on the local network. Depending on the expansion level – color highlighted in AirWatch – more servers may be needed. At least one AirWatch Cloud Messaging Service (AWCM) machine is necessary. The administrator can distribute the various services, such as the device service or the API, as needed across different servers and safeguard them with load balancing or reverse proxy technologies.
The primary AWCM service is a proprietary development based on Java and offers the option of reaching mobile devices with Android and Windows Phone directly without having to use vendor-specific services such as the Google Messaging Service. Apple devices, however, have no alternative to the Apple Push Notification Service (APNs). All told, AirWatch uses more of a pull than a push mechanism. The devices report to the AirWatch server at an interval that is adjustable depending on the platform and get their orders for inventorying, compliance audits, or app deployment. Technically speaking, the tasks in the MDM field are XML packages interpreted by the client.
One server is enough for a simple MDM in the scope of the VMware AirWatch Green Management Suite [2], with the MDM, container, and catalog modules (Table 1). The Orange Suite has a special inbox for secure incoming mail, and in the Blue Suite, App Wrapping joins the fray to protect apps against the local operating system. Also included in the Blue Suite is a proprietary browser, the Content Locker security feature, and the VMware Identity Manager.
Tabelle 1: VMware AirWatch MDM
|
Product |
Software for centralized management of various mobile platforms. |
|
Price |
In the cloud-based pay-per-device version, pricing starts at $51/yr for the Green Management Suite. Alternatively, VMware offers a pay-per-user system with up to three devices per user starting at $102/mo. The Green Deployment Service costs $1,500 as a one-off in the cloud version or $2,500 for an on-premises installation. |
|
System Requirements |
AirWatch supports Android, Apple iOS, BlackBerry, OS X, Symbian, Windows Mobile, Windows PC/RT, and Windows Phone devices. On-premise installations require a current Windows Server with an SQL database and the firewall set up to allow ports 443 and 2001. |
In the lab, I focused on the typical MDM. Instead of a separate installation with Active Directory connectivity, I chose the cloud variant, which offers the same functionality as the on-premise installation. Again, you can integrate an LDAP-based directory service, such as Novell eDirectory or Microsoft Active Directory, but I made do with AirWatch's local user administration. The free trial version for up to 30 days, including all the necessary certificates can be ordered on the website [1], but without a personal conversation with a member of the sales staff, you cannot access the management interface.
Simple Initial Entry of the Endpoints
In the lab, I initially focused on setting up the AirWatch MDM. Even before I was able to familiarize myself with the menu structures, an installation wizard popped up asking whether I wanted to integrate a device. After I said yes, I was confronted with the question as to whether I wanted to manage Apple devices. A yes to this question took me to the dialog for an Apple Push Certificate. Compared with the acrobatics that were necessary to accomplish this just a few years ago, the process has been simplified significantly. With just a few mouse clicks over three minutes, the AirWatch server was able to talk to iOS devices over APNs, and I added my first test device, an Apple iPad Mini with iOS 8.4.0 to the management console just as quickly.
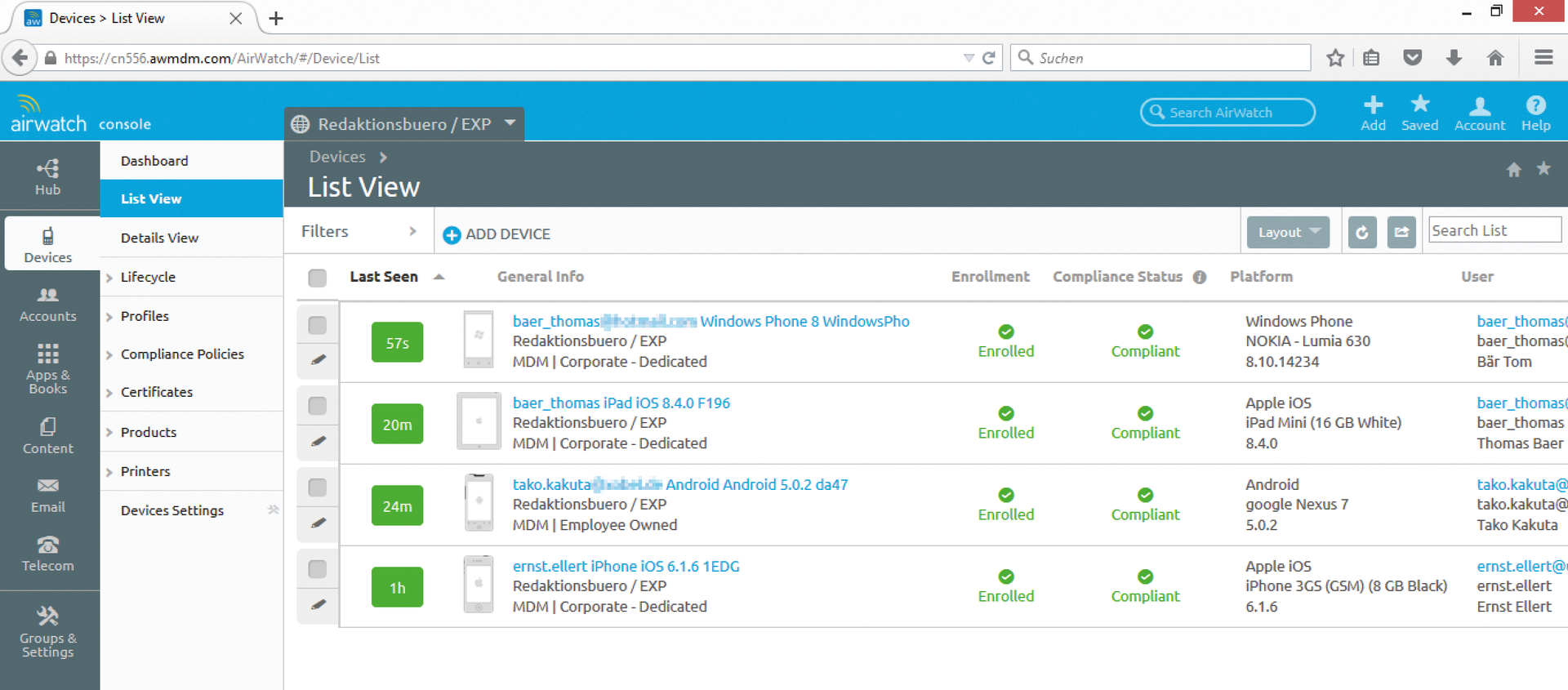
Other test devices – an Apple iPhone running iOS 6.1.6, a Nokia Lumia 630 with Windows Phone 8.1, and a Google Nexus 7 with Android 5.0.2 – integrated without difficulties, as well. If a device is already integrated into another MDM structure, the profile install does not work, at least on iOS systems, and ends with a Profile already exists error. Whether integrating an endpoint into two MDM environments makes sense is a totally different matter. Users can also remove a management profile at any time and without the consent of the administrator. At the end of the day, the user always comes out on top – administrators can only influence active profiles. These restrictions are not attributable to AirWatch but are rooted in the platforms.
The AirWatch installation wizard also invites you to complete the setup at a later date. By showing percentages and different color fields, the software indicates which parts of the setup process still need to be completed (Figure 1). Anyone who has ever set up other server solutions that guide the administrator through endless pages will appreciate this support.
After the initial configuration, I looked at the basic installation for the environment. Depending on how the software is to be used, it makes sense to create clients first. The ability to inherit settings in AirWatch proves to be highly practical. If you enable a setting at the root level that prevents the use of the camera on iOS devices, this configuration applies to all subordinate structures for which Inherit is checked. Changes at the client level only apply if you change the setting for that level to Override. However, it is advisable to leave the root level as is and to emulate the organizational structures of the enterprise for which different settings will apply in the Settings dialog box. For IT consultants looking to deploy a powerful MDM solution for their clients, multitenant use is also very helpful.
Interface
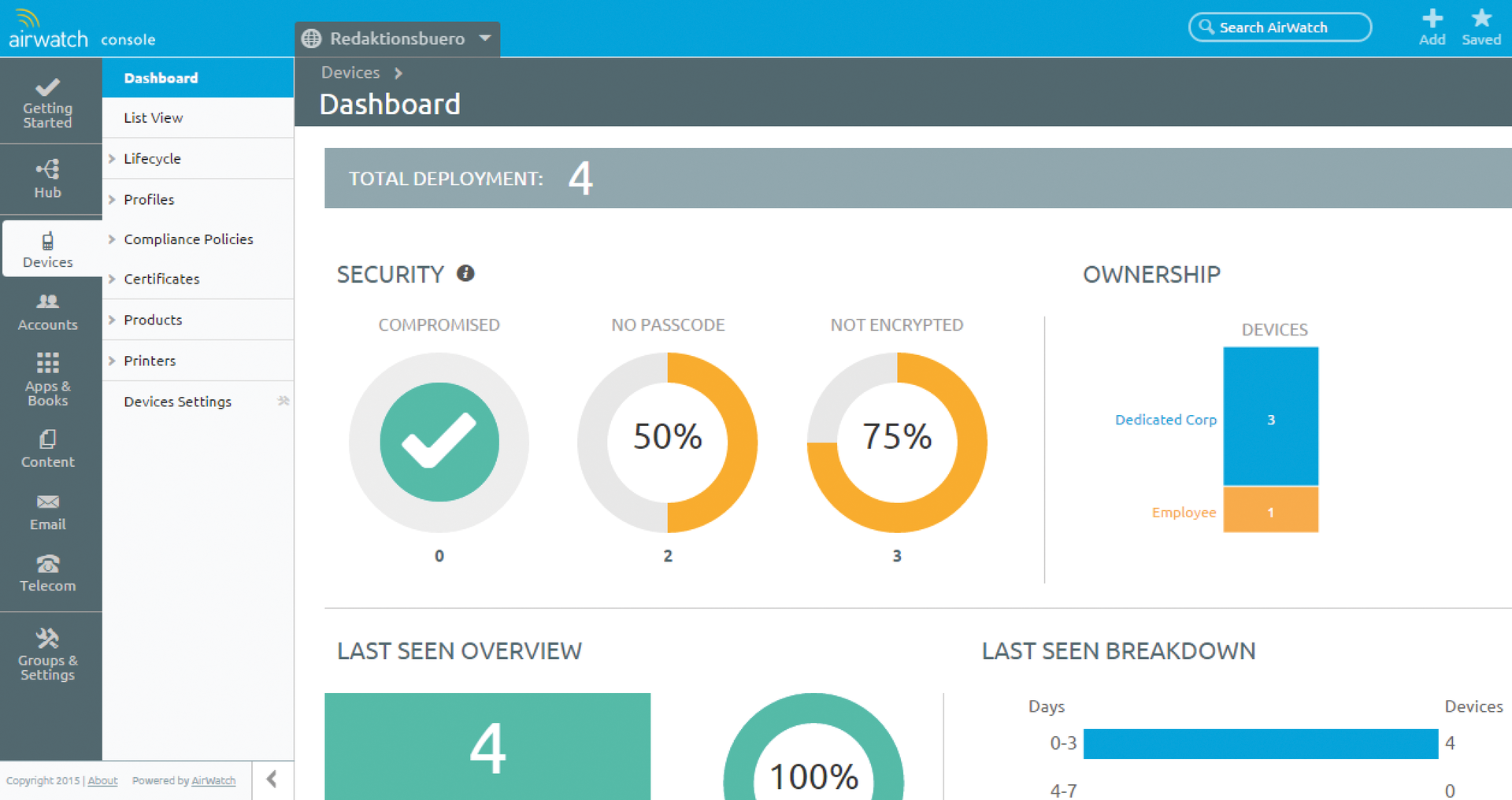
In principle, all MDM solutions are similar in terms of the use options on devices running Android, Apple iOS, BlackBerry, Mac OS, Symbian, Windows Mobile, Windows PC/RT, and Windows Phone. The main difference lies in the way in which the devices connect the management server and how administrators manage the mobile devices in the GUI. All current MDM solutions provide the mandatory dashboard, which displays potentially problematic devices that have been rooted or jailbroken. A graphical representation of the distribution of the platforms and lists of devices without a password are provided by almost all the clients (Figure 2). In the case of AirWatch, you can very easily click directly through the graphical list and customize the dashboard to suit your own needs via the Layout drop-down box.
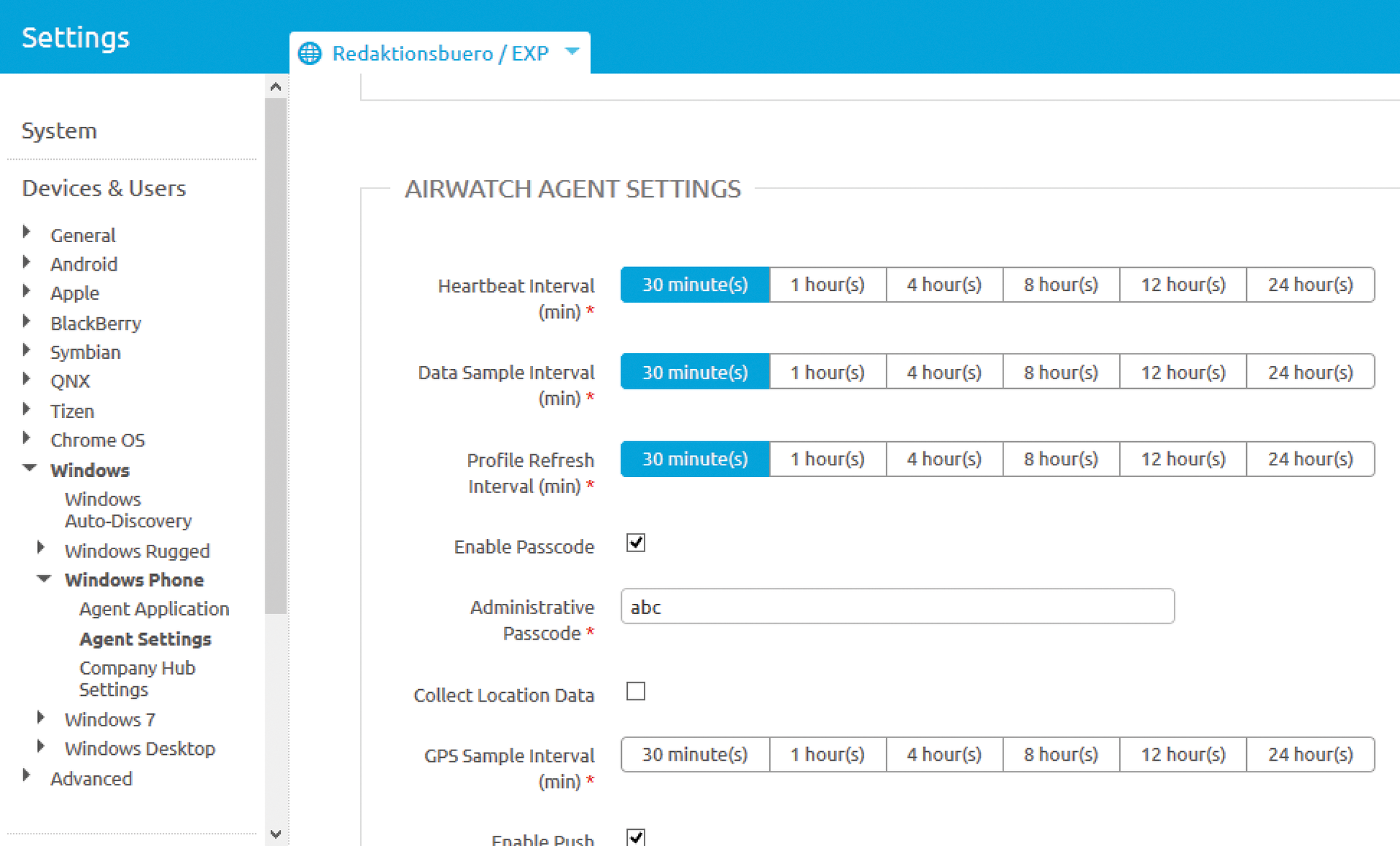
Using the configuration features of the mobile devices, the administrator can manage which configuration changes need to be controlled actively (Figure 3). For example, the existence of a special version of an app can be queried, in combination with system settings such as passwords and a device class. Dynamic groups composed in this way are known as "Smart Groups" in AirWatch-speak. IT managers often lack the ability to control individual devices separately in these groups, so the AirWatch MDM offers "tags" for this purpose. By default, the tags are Damaged, In Repair, Shipping, High, Medium, Low, Software, and Other. You can also add your own tags to suit your own needs.
All told, the software gave the impression that the developers paid a great deal of attention to detail in many places. For example, in the Add button at the top right in the menu, you find the most important commands – Add Device, Add User, and Add Admin. This removes the need to search for the appropriate commands in the depths of the menu. If you want to bookmark a frequently used command or view, click on the "star" icon. Like a web browser, the MDM software stores these favorites in the user context, which is a good solution, in my opinion.
The search functions in the interface stood out. Most MDM programs usually deliver lists, which you have to expand with a plus icon to view more details. With AirWatch, I had the option of freely adjusting the columns and lists. When I later re-opened the GUI, the views came up just as I left them. The search function in the top menu consistently searches through all the settings, whereas the search function near a table is limited to narrowing down the search results already displayed. The filter functions are another way of winnowing the search results, and you can export or print the results as PDF or CSV files.
Conclusions
VMware AirWatch is perfect for large companies with a large number of different mobile platforms, whereas it is conditionally suited to companies that primarily use their mobile systems internally and inherently restrict user access options. The product is not suitable for companies that do not use mobile devices or have a very small number of mobile devices.
I thoroughly enjoyed testing AirWatch for MDM. The parameterization options for the administrator are wide-ranging, and platform support is comprehensive, with multitenancy and user management to match, allowing providers to integrate a wide range of customer scenarios. Hardly any other MDM software is as intuitive to use as AirWatch.
