News for Admins
Tech News
openSUSE Comes to Windows 10
Ubuntu is the officially supported version of Linux to run inside Windows, using the Windows Subsystem for Linux (WSL) technology; however, engineers have discovered that you can replace the Ubuntu-based environment used in WSL with other versions of Windows.
SUSE/openSUSE engineers have managed to bring openSUSE to Windows 10. In a January 12 entry in the SUSE blog, Hannes Kühnemund, Sr. Product Manager at SUSE, detailed the process of replacing the Ubuntu Bash shell with openSUSE Leap in Windows 10.
A user needs to be part of the Insider Program with WSL enabled. The procedure detailed by Kühnemund requires the Ubuntu Bash shell to be already installed on the system; it simply replaces Ubuntu with the openSUSE userspace. You can also install SUSE Linux Enterprise, said Kühnemund.
This could be a useful workaround for those developers and sys admins who run Linux on Azure machines, because they can run both Windows and Linux utilities on their systems without the overhead of a virtual machine or dual booting.

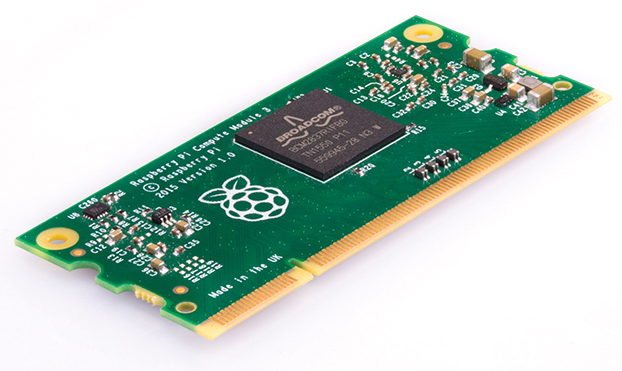
Raspberry Pi Compute Module 3 Released
The Raspberry Pi foundation has launched two versions of the Raspberry Pi Compute Module 3 (CM3).
The standard version is based on Raspberry Pi 3 hardware. It runs on a CM2837 processor (up to 1.2GHz) and comes with 1GB of RAM, plus 4GB of on-board eMMC flash storage.
A Lite version of CM3 (CM3L) comes with the same processor and same amount of RAM, but instead of on-board storage, it comes with an SD card interface to the Module pins so a user can connect the module to an eMMC or SD card of their choice.
The foundation has also launched an updated version of the Compute Module IO Board V3 (CMIO3), which offers an easy-to-use "base" into which you can plug your compute modules, program them using the HDMI and USB connectors, and then use them in various applications.
The Compute Module has already gone beyond the DIY and maker communities and has made its foray into the commercial space. NEC is using the compute module in their commercial displays for corporate customers.
CM3 and CM3L are priced at $30 and $25, respectively. The Foundation has also dropped the price of the original Compute Module to $25. One of the core goals of the foundation is longer shelf lives of their devices. As a result, CM3 is kind of backward compatible with the CM1 design, which means you can simply remove the older CM and replace it with CM3. The only caveat is that CM3 can run a bit hotter than the previous board, and it's 1mm taller, so you do need a heatsink and take into consideration the 1mm of extra space.
Critical Security Holes Found in PHP7
IT security firm, Checkpoint, has found serious vulnerabilities in PHP 7. Checkpoint has analyzed the code of PHP7 to look into any vulnerabilities, especially "the unserialize mechanism" that was heavily exploited in PHP 5, thus compromising platforms like Magento, vBulletin, Drupal, and Joomla.
What they found was not encouraging, Checkpoint wrote in a blog post, "Throughout our investigation we discovered 3 fresh and previously unknown vulnerabilities (CVE-2016-7479, CVE-2016-7480, CVE-2016-7478) in the PHP 7 unserialize mechanism. These vulnerabilities can be exploited using a technique we've discussed back in August."
The first two vulnerabilities, according to Checkpoint, gives attackers complete control over servers. The third can create a DoS (Denial of Service) attack, which exhausts the memory consumption of the target site and shuts it down.
The PHP team was informed of the vulnerabilities in August and September. The fixes for two vulnerabilities were released on October 13 and December 1. Users are advised to ensure they are running the latest version of PHP.
Check Point has issued IPS signatures for these vulnerabilities to protect users from possible attacks.

© Yevgeniya Ponomareva, fotolia.com
New Android Malware Found
Security researchers at Kaspersky Labs have discovered a new malware that affects Android devices. Nikita Buchka wrote on a blog post, "Instead of attacking a user, it attacks the Wi-Fi network the user is connected to, or, to be precise, the wireless router that serves the network."
The trojan deploys the brute-force attack to guess the password and access the device. Once the password is cracked, it modifies the DNS server in the router, redirecting all traffic through their own servers and malicious websites.
What makes things really bad, Bucha explained, is that, instead of affecting users, the malware affects the entire network, which means every user on that network is exposed. Kaspersky recommends checking the DNS settings of your router.
There are currently two versions of the app: one is a fake mobile client for Chinese search engine Baidu and the second one is about WiFi network. It's the same old story where cybercriminals are offering malicious fake apps outside of official app stores. Always use the official apps stores. If you stick with the official Google Play store, you'll have a safer Android experience.
The lesson here is: don't install random apps from random websites.

© Sergey Konyakin, 123RF.com
