
Segmenting networks with VLANs
Logically Tunneled
The most obvious network separation is routinely carried out between the Internet and the internal network. The connection of the IT infrastructure of a company to the outside world is typically implemented in a demilitarized zone (DMZ), which is a subnet that provides controlled access to public servers and services that exist in it. A firewall separates the Internet from the DMZ, and another firewall separates the DMZ from the internal network (Figure 1). Thanks to this separation, access to publicly accessible services, such as email, Internet, DNS, or voice over IP (VoIP), can be granted while still protecting the internal corporate network from unauthorized access from the outside. Also, the distribution of the data streams into virtual LANs (VLANs) takes place in the DMZ.

If you use VoIP, the Enterprise Session Border Controllers (E-SBCs) are also installed in the DMZ. This is a kind of Session Initiation Protocol (SIP) firewall. The data firewalls pass the VoIP/video streams to the E-SBC via an open port. Because the E-SBC is an application-specific test component, it performs "deep packet inspection" and ensures that only legitimate SIP messages reach the VoIP/video components in the corresponding voice VLAN.
The E-SBC acts as a proxy and can perform VoIP/video interception or check encrypted connections. After the check, the data is encrypted again and redirected to the recipient. Additionally, an E-SBC can prevent denial-of-service (DoS) attacks on the telephone system. Positive and negative lists of IP addresses belonging to trusted communication partners and known attackers also can be created. Failed logon attempts are registered and the potential attackers then blocked. This prevents flooding of the call server with registration messages.
Advantages of VLANs
Network virtualization ensures that systems can be structured from a logical point of view – that is, independently of the physical topology. In traditional LANs, the devices of a physical wiring area, such as a floor or a building, usually make up a contiguous network group. Subdividing networks with VLANs typically offers various advantages, including flexibility in assigning devices to network segments.
A VLAN is a logical grouping of network devices or users that is not limited to a physical segment. VLANs segment switched networks logically by function within an organization by project team or application. For example, all VoIP phones and VoIP servers can be connected to the same VLAN regardless of their location on the network.
Performance can be improved thanks to VLANs. For example, the delivery of specific traffic types (e.g., voice) in a VLAN can be prioritized in the transmission. Admins usually only reduce the broadcast domains and thus prevent broadcasts propagating over the entire network. A VLAN is a broadcast domain that spans one or more switches. Packet forwarding between the different VLANs takes place at level 3. To do this, each VLAN must have a connection to a router.
VLANs do not protect networks against spying or sniffing, although they can be monitored like switched networks using data analyzers (e.g., Wireshark). Despite this failing, VLANs are considered safer than normal networks. In truth, a network is also based on a VLAN where all nodes on the network work with a VLAN ID of 0.
Multivendor VLANs
Multivendor VLANs can be created on the basis of IEEE 802.1p/Q. The type field in the corresponding package format is shifted back by four digits. The 802.1p/Q package format also begins with the usual destination address (2 bytes), followed by the source address (2 bytes). Instead of the type field, another 4 bytes are added in the extended package format, while the following Ethernet header information for these 4 bytes is moved backward. These additional 802.1p/Q bytes contain the VLAN ID and prioritization – 2-byte type ID of the VLAN, 2-byte tag control information (TCI). In the Ethernet packet, the familiar type field ID, the data, and the CRC checksum then follow.
The IEEE unambiguously defined the value "8100" as a VLAN type ID. The 16-bit TCI that follows is for data prioritization (3 bits), token-ring encapsulation (1 bit), and identification of the respective VLAN identifier (12 bits). A maximum of 4,096 VLANs can be set up with the 12 bits of the VID (VLAN identifier) field. Tagged VLANs differ from the older, tagless, port-based VLANs. The term "tagged" refers to defined network packets that have an extra VLAN tag.
Ensuring Quality of Service
To ensure the quality of service within the MAC layer, the IEEE defined an extension of the IEEE 802.1d (MAC bridges). The 802.1p standard (traffic class expediting and dynamic multicast filtering) describes methods for providing quality of service at the MAC level. IEEE 802.1p defines the following QoS parameters:
- Service availability: Decides whether a service is provided in bridged LANs.
- Frame loss: Equivalent to packet loss
- Frame misorder: Re-requests of packets/frames are not possible at the MAC level; the packet order is thus a QoS parameter.
- Frame duplication: Packet duplication is not supported by MAC services.
- Transit delay experienced by frames: The time that elapses between the request and the confirmation of a successful transfer.
- Frame lifetime: Limiting the lifetime of a packet within a network prevents the possible formation of loops (equivalent to the Time-to-Live TTL value in the header).
- Undetected frame error rate: Very low error rate if the procedures for determining checksums (FCS, frame checksum) are used.
- Maximum service data unit size supported: The maximum size of a packet within a network. Defined by the network element that has the smallest packet size.
- User priority: Handled as a QoS parameter at the MAC level.
- Throughput: Data throughput
The distinction of the packets and the corresponding mapping to queues can be achieved by identifying the priorities of a packet or frame. IEEE 802.1p recommends user priority and its mapping to traffic classes and existing queues. Table 1 shows this relationship.
Tabelle 1: Traffic Class Mapping
|
User Priority Number of Available Traffic Classes |
||||||||
|---|---|---|---|---|---|---|---|---|
|
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
|
|
0 |
0 |
0 |
0 |
1 |
1 |
1 |
1 |
2 |
|
1 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
|
2 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
1 |
|
3 |
0 |
0 |
0 |
1 |
1 |
2 |
2 |
3 |
|
4 |
0 |
1 |
1 |
2 |
2 |
3 |
3 |
4 |
|
5 |
0 |
1 |
1 |
2 |
3 |
4 |
4 |
5 |
|
6 |
0 |
1 |
2 |
3 |
4 |
5 |
5 |
6 |
|
7 |
0 |
1 |
2 |
3 |
4 |
5 |
6 |
7 |
The specified user priority is defined by the application or by the user's authorizations. Within a network, the transported information (traffic types) is broken down into traffic classes (see Table 2).
Tabelle 2: Traffic Classes
|
User Priority Value |
Traffic Class |
Comment |
|---|---|---|
|
0 |
Best effort |
Normal data traffic |
|
1 |
Background |
Large-volume data transmissions that are time critical and do not have special priority |
|
2 |
Spare |
Not precisely specified |
|
3 |
Excellent effort |
Important data |
|
4 |
Controlled load |
Time-critical data with high priority |
|
5 |
Video |
Image transfer (delay <100ms) |
|
6 |
Voice |
Voice transmission (delay <10ms) |
|
7 |
Network control |
Network management data, to keep the network running; server to determine the shortest route |
Packet prioritization and the corresponding mapping to queues in the switch is achieved by the priority field in the VLAN tag (bits 1 to 3). The IEEE 802.1p standard defines the mapping of priorities to the respective traffic classes and existing queues. Within a network/VLAN, the transported information is assigned to different types of traffic. Usually, the respective packet priority is defined by the application or by the user's authorizations.
Distinguishing seven types of traffic as opposed to eight defined traffic classes reduces the number of queues required in the layer 2 switch. In practice, the number of available queues in the switches is less than the number of existing traffic classes. Currently, only two or four queues are used by most network components. For this reason, the administrator needs to adjust the traffic classes to reflect the queues that exist in the switch.
Cross-Switch VLANs
Where one or more VLANs extend across multiple switches, VLAN trunks (VLTs) are used. In the case of port-based VLANs (for packages that have no tag), a VLAN tag that indicates to which VLAN the packet belongs is added to forward a data packet across a trunk; this typically happens before feeding into the trunk. The switch on the receiving side needs to remove this again. In the case of IEEE 802.1Q VLANs, however, the packets are tagged by the device or at the input port on the switch. Therefore, a switch can feed a packet into a trunk without any changes. When a switch on a VLT port (trunk port) receives a packet with an 802.1Q VLAN tag, it can transfer the packet unchanged.
If it receives packets without tags on a trunk port, they can either be assigned to a default VLAN depending on the configuration (the switch later adds the tag), or they are discarded.
Dynamic VLANs with GVRP
VLAN memberships of devices can be assigned statically via a management tool, but also dynamically on the basis of the Generic Attribute Registration Protocol (GARP) VLAN Registration Protocol (GVRP). However, you need to bear in mind that a dynamic VLAN assignment is only useful if topology changes occur because of the use of the spanning-tree protocol and the switches thus need to re-learn the existing MAC addresses.
GARP is defined in the IEEE 802.1D standard; with its help, devices can transmit their attributes to the switch and from switch to switch. To register devices in VLANs, GARP was extended to include VLAN functionality (GVRP). The registration services provide a GARP application. The application is responsible for defining the semantics of the parameters to be transferred and generates the Protocol Data Units (PDUs). To exchange the necessary information, GVRP uses the GARP Information Declaration (GID) and the GARP Information Propagation (GIP).
GID describes the current states for registrations and declarations and determines the required actions. A registration or declaration can be made, for example, using a GID_JOIN or GID_JOIN request, and deleted with a GID_LEAVE or GID_LEAVE request. Joins are regularly repeated per port and multicast group.
GIP is a feature that distributes registrations and declarations on one port to all switches on the LAN. Moreover, the switches discover which VLANs the users are currently working in. GIP also reacts to topology changes triggered by spanning tree. Information is forwarded to GVRP nodes via a specific multicast address. For this purpose, the multicast address 01-80-C2-00-00-21 is set as the destination address for the GVRP protocol data units.
VLAN Troubleshooting
During troubleshooting, you need to examine the data acquired using an analyzer for packets from the corresponding VLAN. Check whether the data stream is correctly tagged by trying to find the VLAN tags in the captured data. In practice, it happens time and time again that the VLAN tags are missing in the traces; complete analysis of the errors is thus impossible.
On many machines, this is a normal phenomenon. The reason is that the VLAN tags are not displayed and are filtered out by the network card before being captured. The suppression of VLAN tags during traffic analysis has its origin in the operating system. Windows, for example, has no built-in mechanism for recording the VLAN tag. Most Ethernet adapter drivers either discard the VLAN tag or remove it automatically before processing. It thus looks as if the Ethernet packet has no VLAN tag. To eliminate this representation problem, each network card used must be considered individually. On Intel cards, the current drivers must be installed. Then you can also take advantage of this feature.
Also, additional manual intervention in the Windows registry is required. Intel provides a corresponding guide [1] for reconfiguring Windows machines. The current driver must also be installed for Broadcom adapters. In the registry you then need to search for the value TxCoalescingTicks and, after clicking on the instance number (e.g., 008), add a new string entry with the name PreserveVlanInfoInRxPacket and a value of 1.
After the change, the respective analyzer should be able to display the respective VLAN tag correctly. It goes without saying that registry changes always involve a certain amount of risk in terms of system stability.
Mapping of Devices and Users
The safe and reliable assignment of users and devices to the correct VLAN enhances security and allows for unique authentication and authorization of users. A node is authenticated by the authenticator at the network access point, a physical port on the corporate network, a VLAN, or a WiFi using this method. The authenticator checks the credentials submitted by the node by means of an authentication server and allows access to the services offered by the authenticator (LAN, VLAN, or WiFi) or rejects access. An endpoint is only capable of communication within the allocated network resources after authorization.
The standard recommends the Extensible Authentication Protocol (EAP) or the PPP EAP TLS authentication protocol. Generally, the services of the authentication server are provided by the RADIUS server (Figure 2). The network access port is a connection point between the supplicant and the unit to which it wants access. IEEE 802.1X envisages three possible network access types for the supplicant:
-
force-unauthorized: Blocks any access of the supplicant. It does not matter whether the supplicant successfully authenticates. -
force-authorized: Access is always granted to the supplicant. It is not important whether the supplicant can authenticate against the authenticator. -
auto: Requires successful authentication of the supplicant. Once the supplicant has successfully authenticated, access is granted, otherwise access is blocked.
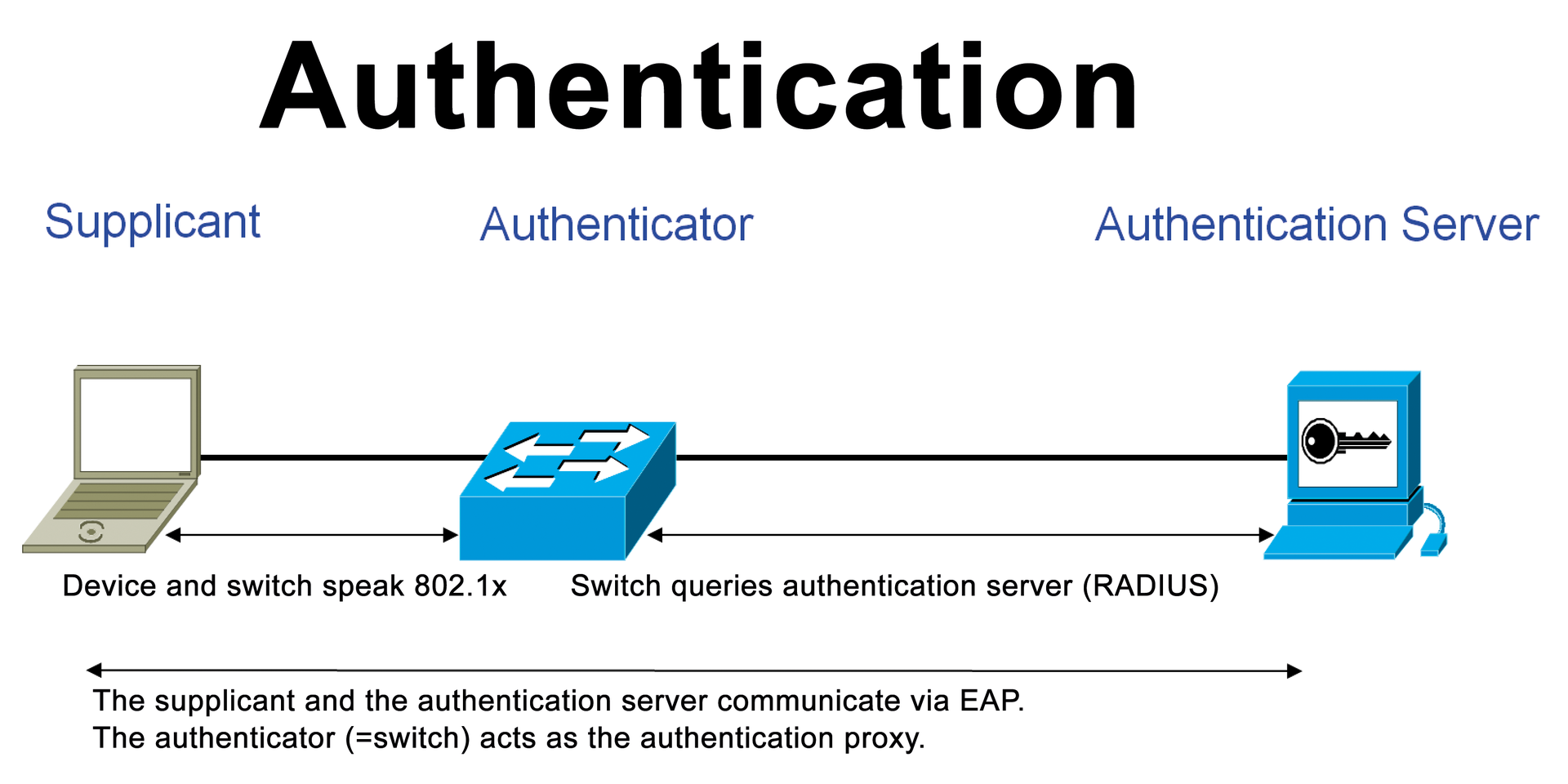
One big advantage in the use of IEEE 802.1X is RADIUS Access-Accept messages from the authentication server to the authenticator. RFCs 2869 and 3579 (RADIUS Extensions) describe a large set of attributes provided by the authentication server to the authenticator. Three interesting attributes here are Tunnel-Type, Tunnel-Medium-Type, and Tunnel-Private-Group-ID. At the end of RADIUS authentication, the RADIUS server sends an Access-Accept message to the Network Access Server (NAS). If these three attributes are appended to the Access-Accept message, the NAS can now add the supplicant to a VLAN. The VLAN ID is delivered in the attribute Tunnel-Private-Group-ID of the response package.
Conclusions
In this article, I looked at the technical details of VLANs, which help to set up logical network segments. The devices and services are separated at the software and hardware level thanks to network virtualization, and the data streams can be transmitted in parallel. However, VLANs do not provide truly comprehensive security and must be supplemented by additional security measures, where needed.
