
Microsegmentation with VMware NSX and vRealize Automation
Micro Net
Companies can easily and efficiently validate and control network traffic within the data center through microsegmentation. Microsegmentation is a collection of techniques designed to isolate network traffic through switching and software-defined networking. VMware's NSX for vSphere adds security to software-defined networking and microsegmentation, allows admins to filter network traffic at the level of the virtual machines (VMs) and network cards without installing an agent on the VM.
In traditional environments without NSX, traffic needs to be redirected for security checking using centralized security components that often exist as physical appliances. In NSX, traffic can be analyzed on the hypervisor itself.
NSX also supports automatic creation of logical, software-segregated, VXLAN-based networks, as well as network components such as firewalls, routers, gateways, or VPN endpoints. Automated solutions today reduce the deployment time for such applications from several days to just a few minutes – and with fewer errors, as the need for manual configuration is removed.
Extensive Set-Up Time
To provision both microsegmentation and network automation in the VMware environment, you'll need the vSphere Enterprise-Plus Edition (which supports distributed switches), vRealize Automation Advanced, and Orchestrator products in addition to NSX.
You'll need to start with some preparatory work on the vSphere and NSX side, including:
- Configuring a distributed switch in vSphere.
- Installing NSX, which includes preparing of the physical network, configuring VXLAN, defining segment IDs, and defining one or more transport zones.
Once you have completed these preliminary tasks, you can begin the actual work, which consists of:
- Preparing NSX for vRealize automation
- Creating an NSX endpoint in Orchestrator
- Configuring NSX vRealize automation
- Creating network profiles
- Applying the microsegmentation features to blueprints (a kind of building plan detailing the deployment process)
Preparing NSX for vRealize Automation
To set up NSX vRealize automation, you first need to create a provider edge gateway that connects the automated NSX world to the external network. In addition, you need to create a Distributed Logical Router (DLR) associated with the provider edge via an uplink. Ideally, this connection is made on the basis of a logical switch on the VXLAN that allows communication between the DLR and the provider edge gateway. The required configuration is shown in Figure 1. Setting up these components so that vRealize Automation can handle network automation and create logical switches at run time is a prerequisite. You can create all three required components of the NSX in the VMware vSphere web client.
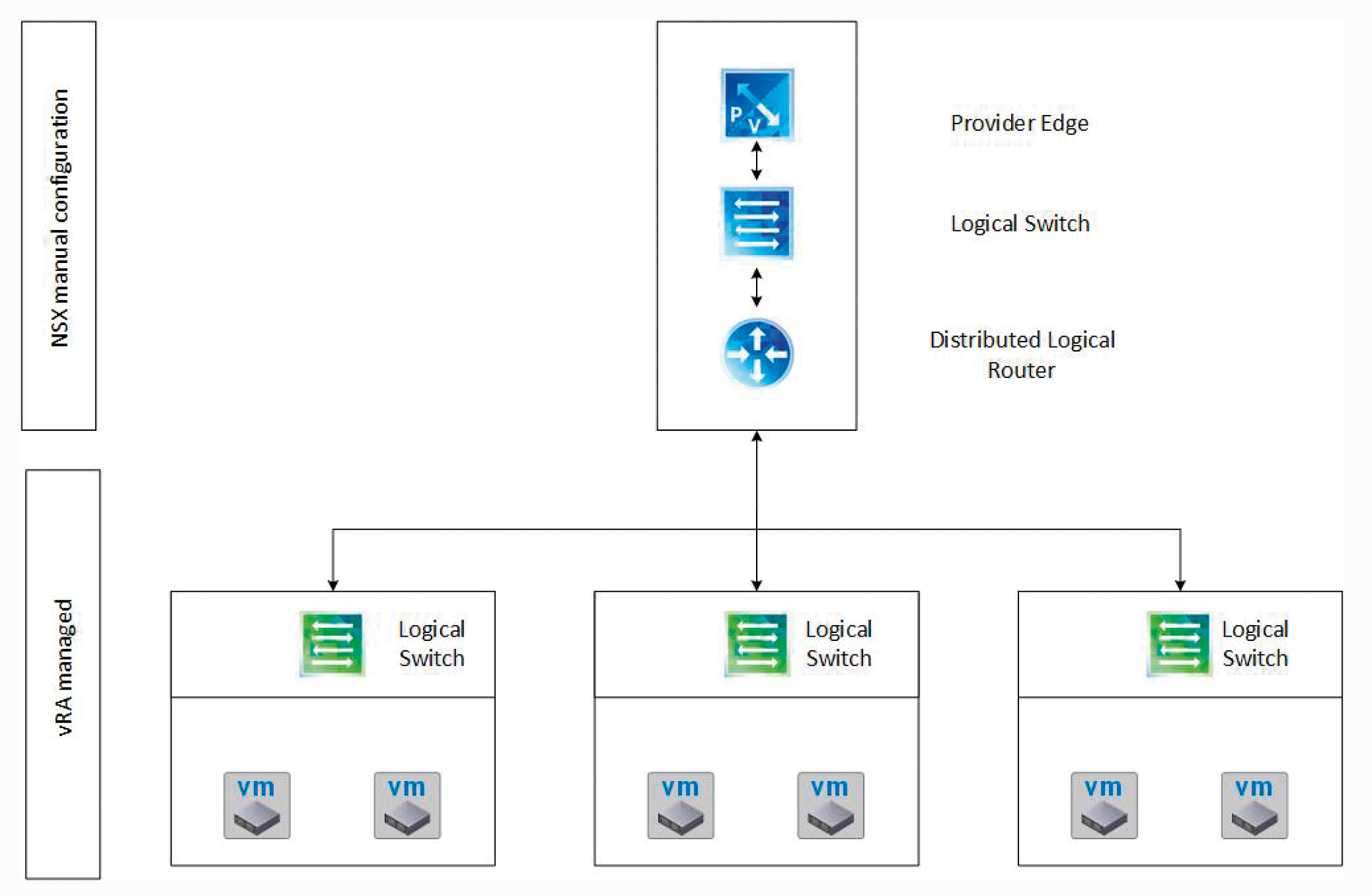
To set up the logical switch, go to the Networking & Security menu in the GUI and select Logical switches. In the NSX Manager's NSX Manager Drop-Down List, select where the configuration should take place. Then press the + button to create a logical switch. You need to assign an appropriate name, optionally a description, and the replication mode (usually Hybrid or Unicast). Finally, check the Enable IP Discovery box and press OK to finish the wizard.
Creating the provider edge is minimally less complex. First select the menu item NSX Edges in the navigation pane and then press the + button to launch the Create wizard. At this point, the configuration starts: In the first dialog, check the Edge Services Gateway box to choose to create an "edge" (a VM with routing functionality and possibly other functions), and enter a name, a description, and a tenant. If high availability of the edge is required, check the Enable High Availability box. Before you continue to the next page of the dialog, you need to enable the Deploy NSX Edge option. In the settings dialog box, specify a username, a password, and the SSH settings. Check the Enable Auto Rule Generation box and click Next.
The next step is to configure deployment. Define the CPU and RAM for the edge VM, and select the hypervisor on which the edge will be created. The network configuration of the edge deserves special attention in the further course of the configuration wizard. As mentioned, it is necessary to create two network cards: For communication with the outside world, you need an uplink network card, which is typically associated with a VLAN port group on a vSphere distributed switch. Configure the second interface as an Internal type, and connect it with the previously created VXLAN-based logical switch. You also need to define matching IP addresses and the Subnet Prefix Length for the two network cards. Choose 1500 as the MTU size. Once the configuration is complete, click Next.
The final steps are simple: First, define the default gateway and the MTU size on the Default Gateway Settings page, and choose to use the previously created uplink network interface card for external communication. On the Firewall and HA page, check the firewall security rules; then start the edge deployment process on the last page of the dialog.
The process of creating the DLR is similar to creating the provider edge, but in the first step of the wizard, you need to check the Logical (Distributed) Router box. In addition, you need to configure an uplink network card (which must be connected to the logical switch) and, if appropriate, the routing between the DLRs.
Creating an NSX Endpoint in Orchestrator
At run time, vRealize Automation does not create networks through direct communication with the NSX Manager but uses the vRealize Orchestrator orchestration engine as an intermediary. For this reason, you need to configure the Orchestrator to cooperate with NSX and create an NSX endpoint. Select the Workflow directory and run the Create NSX Endpoint workflow (library/NSX/configuration). In addition to a name for the endpoint, you need to enter the appropriate access data and the URL of the NSX Manager.
After workflow execution has completed, check whether the setup has worked out in the Orchestrator inventory: If you can expand the NSX menu item, and if the corresponding NSX components appear, the configuration was successful.
Configuring NSX vRealize Automation
You need to configure some settings on the vRealize Automation side. First, customize the vSphere endpoint by changing to the Infrastructure | Endpoints | Endpoints page in the graphical user interface. When you get there, edit the corresponding vSphere endpoint (Figure 2). Now check the Specify Manager for Network and Security Platform box, enter the URL of the NSX Manager below Address, and enter the corresponding NSX access data before closing the dialog box by pressing OK and saving the changes.
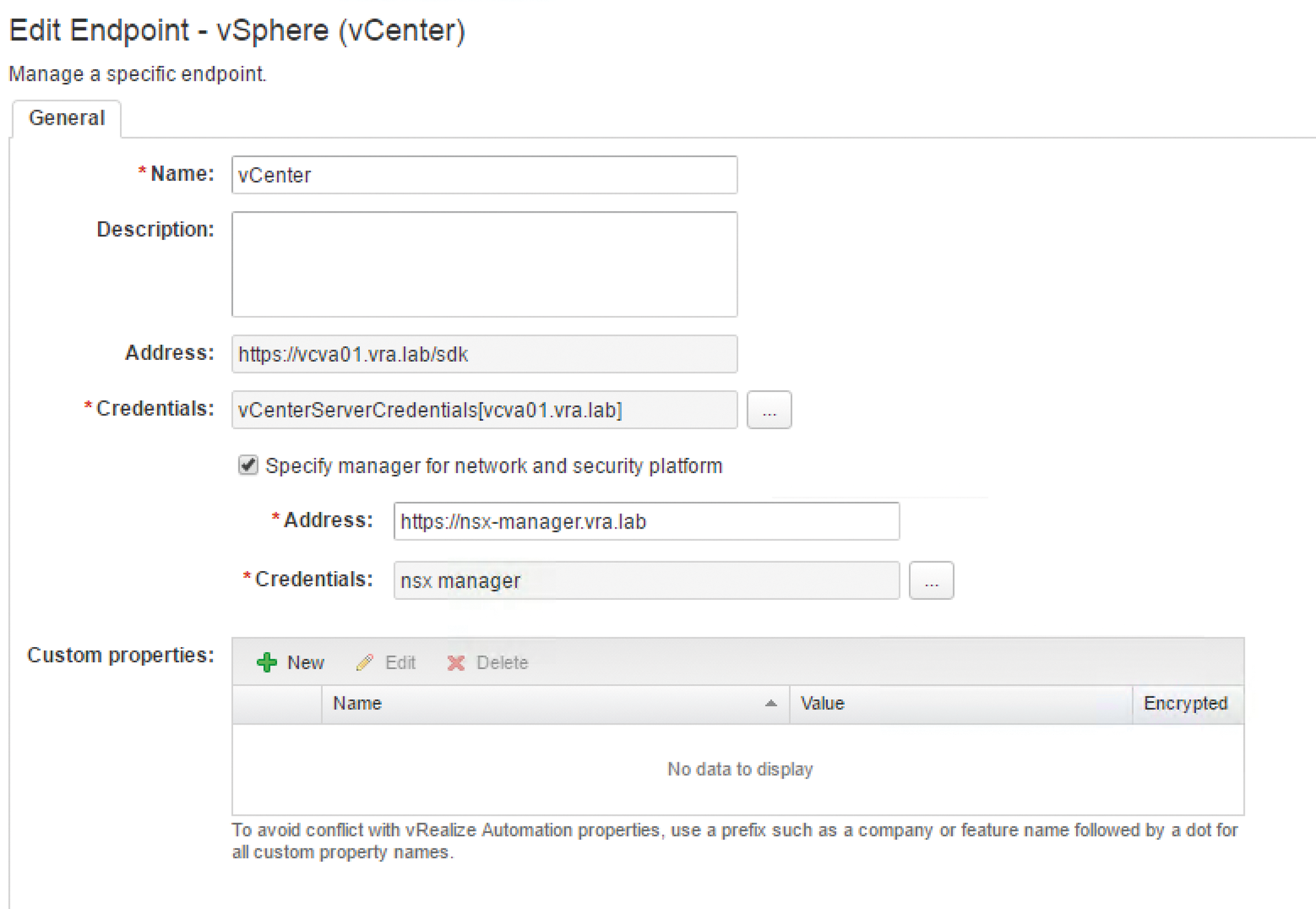
You also have to run an inventory scan so that vRealize Automation is notified of NSX. To run an inventory scan, navigate to the Infrastructure | Compute Resources | Compute Resources menu and start data collection for the appropriate resource.
Creating Network Profiles
The next step is to configure the network profiles in vRealize Automation. Network profiles store information that vRealize Automation needs at run time to create a new network. vRealize Automation uses four different types of network profiles:
- External network profiles point to existing networks (i.e., vSphere port groups). This type of network profile stores network information such as DNS servers, gateway, or IP addresses that can be assigned when provisioning VMs.
- Routed network profiles allow the dynamic creation of a network with various subnets and a matching routing table. They enable end-to-end communication between machines on different networks with separately allocated IP addresses.
- One-to-one network profiles ensure that the machines generated are given an internal NAT network address, as well as an external IP address.
- One-to-many network profiles behave just like one-to-one network profiles, except that all internal machines share a single external IP address. In both cases, Orchestrator creates corresponding source NAT rules in the NSX.
If a routed network profile is used for the deployment, vRealize Automation creates a new network with the help of Orchestrator and registers this network with the DLR so that the newly-created network can be routed through the L3 gateway.
To create a routed network profile, you need to create the routed network profile and then link the profile with the vRealize Automation reservations you wish to use.
Because an external network profile is already present in most environments, you can jump right to creating the routed network profile. Navigate in the vRealize Automation GUI to the Infrastructure | Reservations | Network Files page, press the + New button, and then choose the Routed option. During the configuration, you first need to type a name and optionally a description. Then select the external network profile with which outside communication will take place from the External Network Profiles drop-down list. Once this value is set, vRealize Automation automatically populates the DNS/WINS settings at the bottom of the screen. The fields Subnet Mask, Range Subnet Mask, and Base IP are of particular interest. The Subnet Mask defines the start of the subnet bit range in the 32-bit IP address. The Range Subnet Mask defines the end of the subnet range. According to VMware documentation, "vRealize Automation generates 255 IP ranges if the subnet mask is 255.255.0.0 and the range subnet mask is 255.255.255.0." Base IP defines the start of the IP address range. Before you save the network profile, go to the IP Ranges tab and generate the n to reflect the previously defined values. Then save the network profile by clicking OK. In some cases, you might need to adjust the firewall rules to match your configuration (Figure 3).
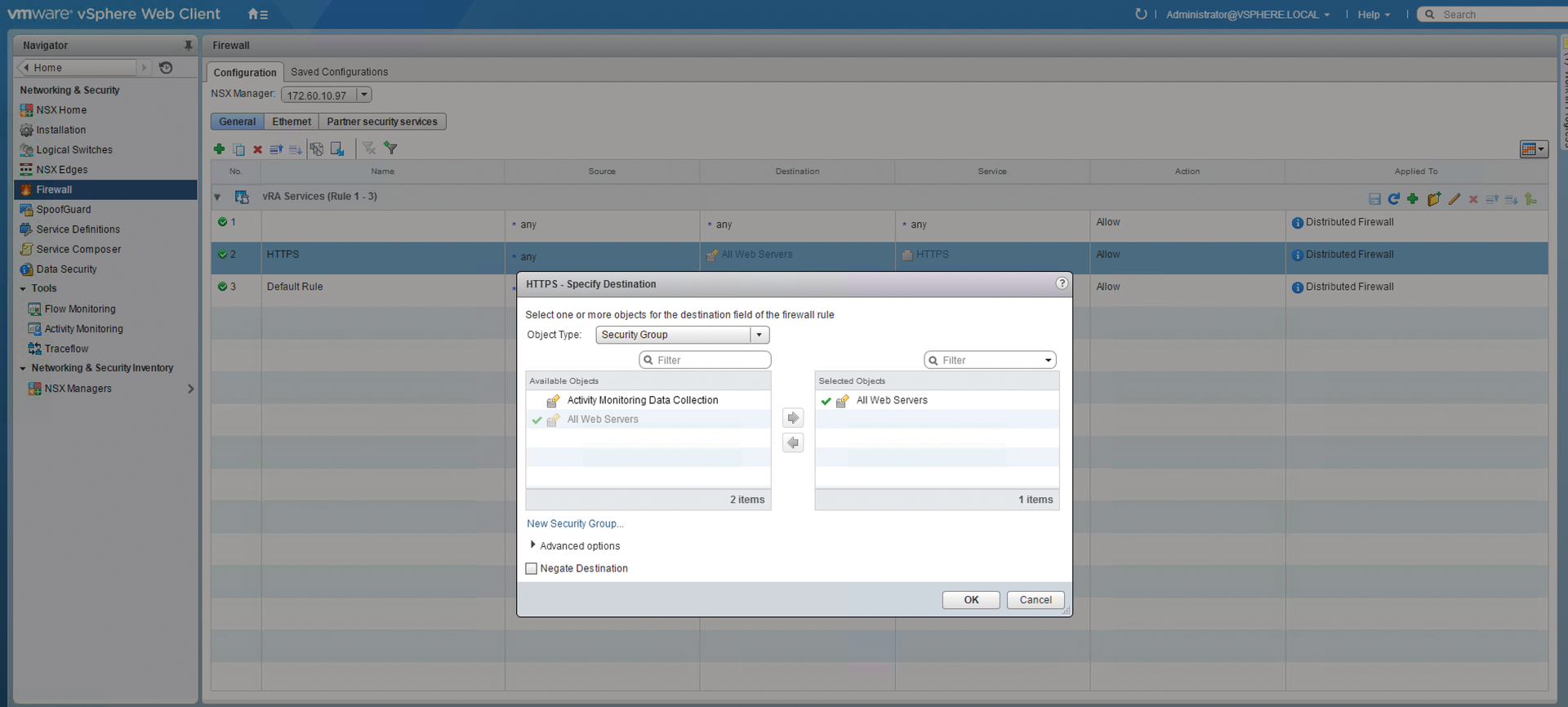
Now you only need to assign the profile to a reservation, so that you can use the network profile when creating a blueprint. To assign a profile to a reservation, go to the GUI below Infrastructure | Reservations | Reservations in the Network tab. You need to assign the external uplink network profile to the appropriate network in the Network section. Below Advanced Settings, make sure that the Transport Zone is set correctly. In the Routed Gateway section, you need to install the distributed load balancer with the network path and network profiles from the external network profile (this was configured when setting up external communication). After this configuration work, you are done at this point and can start creating blueprints. See the box entitled "NAT Profiles" for more on configuring network address translation.
Conclusions
vSphere, NSX, and vRealize Automation give admins the ability to create dynamic networks and, at the same time, control network traffic with microsegmentation. The interaction between NSX and vRealize Automation is critical to the configuration. Security rules can be defined centrally in NSX for use with vRealize Automation.
